Live long and prosper...and forget all your passwords.
~Lieutenant Commander Spock
USS Enterprise
Introduction
Many of you will remember my recent article (viewed by over 297,000 people) which discussed a method which allows users to create cryptographically strong hash-based passwords so they never create a password again. You can read that article here at CP : Destroy All Passwords: Never Memorize A Password Again[^] (Draw Your Password).
Missing Piece : Found!
However, at the time, there was one missing piece. You couldn't generate a password for the main login on your computer. That's because when your computer is sitting at the main login screen there is no way to run my application to draw your shape and generate your password. Additionally, even if you had the program running on your phone and generated the password there the password is so long (cryptographic hashes) that you'd never want to type those in by hand.
Never Type A Password Again
With this article, I've solved that problem and created a device that will allow you to avoid typing a password ever again. If you'll stick with me and really think this through (and examine my advanced idea which is near the end of the article) I believe you'll be convinced that I'm The Guy Who Destroyed Weak Passwords* once and for all!
The tyranny of keeping 30+ passwords in your head is over! It's over, my friends.
*I'm seroius and I honestly believe if you'll read the whole article you'll agree. We just transcended passwords!
Quick Overview of How It Works
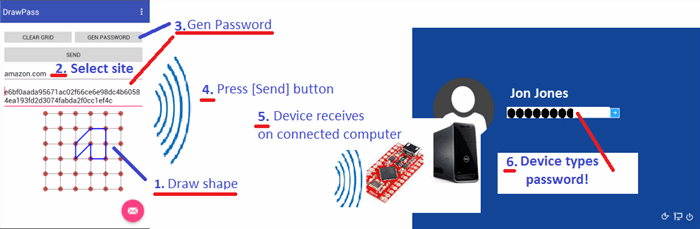
Overview: How It Works
- Draw your shape on the grid. You need only draw one shape for all your sites, because the password will be salted by the "site name" (among other factors -- many more details in aforementioned article) so the generated password for each site will be unique and cryptographically strong.
- Select the site you want to generate a password for. This will be a drop down list which will allow you to add your unique identifier that you will use to keep track of which site you use the password with. It can be any characters you want and which will provide a way for you to remember which one you use the password with.
- Generate the password. Clicking this button will generate the hash value from the points you selected on the grid along with the salt value of your "site name".
- At this point, you will make sure the paired computer is on the login screen and the cursor is in the password box. After that, click the Send button and the password will be sent over (encrypted) Bluetooth.
- The attached BlueKeySafe device will receive the password on it's Bluetooth receiver.
- Finally, the BlueKeySafe device types the password into the password text field (which has cursor focus).
Once You've Logged Into the Computer you can run the normal desktop version of DrawPass (see my previously mentioned article at the top of this article) if you want to, but you don't have to. Instead, each time you visiit a web site you need to log into, all you have to do is set the cursor in the password text box, gen your password on your paired device and press the [Send] button.
Other Features Missing From Android Prototype Version
When I created the desktop version of DrawPass there was a huge response with people saying that there has to be a way to add special characters, add uppercase characters and/or make the password a specific max length (stupid sites which force short passwords make passwords weak). However, you may not see those elements here in the Android prototype DrawPass. That's simply due to time constraints and because I'm so excited to submit this as an entry for the CP IoT Contest. If you take a look at the desktop version of DrawPass it'll give you a better idea of the final product.

Desktop and Android App (Prototype Mismatch)
Also, note that as I developed the code for the Android app some things changed for generating the hash password so until I update the other article the hashes won't match. This is all part of the prototyping process.
Update will be coming soon so both Android app and Desktop app match each other.
Now, let's take a look at how I developed the device (BlueKeySafe) and all you need to build one and then we can talk about the benefits of using it and other details.
Developing the BlueKeySafe Prototype
All of the work I put into my first entry for the IoT Contest ( Never Buy A Garage Door Remote Again: Open Your Door With Your Android Phone (via Bluetooth)[^]) paid off because I learned about the simplicity of building hardware around a neat little Bluetooth component called the HC-05.
After learning that I could easily get data from a paired device I stumbled upon another fantastic board built by the fantastically creative people at SparkFun (SparkFun Electronics[^]) called the Pro Micro. You can see details and get the datasheet at: Pro Micro - 5V/16MHz - DEV-12640 - SparkFun Electronics[^].
See Parts List for links to Amazon products for easy purchasing.

The Power of Forcing Yourself to Learn
If I hadn't done that first project where I learned about the capabilities of the Atmel chips and the the Bluetooth module, I never could've understood the power that was staring back at me in the form of this little board. That's because the Pro Micro implements an ATmega32U4. That chip can be programmed with the same code that I just used in my previous article which implements the ATMega328P chip.
Input and Output Pins
Additionally, if look closely at the board (https://cdn.sparkfun.com//assets/parts/9/3/2/6/12640-02a.jpg -- zoomed in view[^]) you will see that the holes in the board represent varoius features that can be connected to. When I saw that the board had holes marked Tx0 and Rx1 I instantaly knew that I could very easily tie a HC-05 Bluetooth module to those pins and receive and write data via Bluetooth. That meant I could easily send and receive data to any device which had the Pro Micro attached.
Moment of Inspiration
The real moment of inspiration occurred when I read that this board and that ATMega32U4 chip support the USB HID protocol. Amazing!!! Well, maybe that doesn't mean much but I knew that USB HID meant USB Human Interface Device. And, Human Interface Device meant that it could act like a keyboard.
Putting It All Together
All of this meant that I could easily:
- Connect my Bluetooth module via
Tx => Rx and Rx => Tx (connect sending / receiving serial lines) to the Pro Micro. - I could write a program and flash it to the on-board ATMega32U4 chip which would grab the received data off the incoming Rx serial line.
- Then the program would type the data via USB HID onto the device (computer) it was attached to. Voila! You can type on your computer from a remotely paired device.!
- Now, all I needed to do was add the Bluetooth pairing code and the Bluetooth sending to my Android DrawPass app and we never have to type a password again. Plus, you never have to memorize a password again, because you can generate them from DrawPass. Additionally, your passwords will be extremely strong.
Programming the Pro Micro Couldn't Be Easier
In my prevous article we learned the basics of setting up a programming environment using a USB ASP (serial programmer) which allowed us to run AVR Dude to flash the code onto our ATMega328 chips. This time, because of the amazing work by the people at SparkFun, everything we need is on the Pro Micro board.
All you need is the Pro Micro board and a USB cable with a regular USB connector at one end and a micro USB (to connect to the Pro Micro board) at the other.
Arduino IDE (Integrated Development Environment)
You will also need to install Atmel Studio so you can write our program and flash it to the chip on the Pro Micro.
You can get the IDE for free at: Arduino - Software[^]. Once you download it you just run the installer and a wizard will walk you through the steps.
Setup Pro Micro Board In Arduino IDE
Once you have Arduino installed we'll need to set up the Pro Micro as one of the boards it will talk to. It's very easy. Just point at a URL and the board will be added as an option.
Here are the steps to set up the Pro Micro board in the IDE:
- Start Arduino IDE
- Open the [File] menu item and selecte the [Preferences] sub menu.
- A dialog box will appear (see image below).

- paste the following URL (which points to some JSON data into the "Additional Boards Manager URLS" edit box (this is shown in the image below)
<code>https://raw.githubusercontent.com/sparkfun/Arduino_Boards/master/IDE_Board_Manager/package_sparkfun_index.json</code>
- Click the [OK} button to save the changes and the dialog box will close.
- Back on the main dialog on the mani menu select [Tools] then select [Board] => Boards Manager... (see image below).

- Another dialog window will appear which looks like the following. Note: You'll have to type "sparkfun pro" and click the item as shown before the
[Install] button appears. 
- Click the [Install] button.
- Once it completes, click the [Close] button.
- Now we need to choose the Pro Micro board as the one that we are going to program. Go to [Tools] menu again and down to the [Board] menu item and when it expands, way at the bottom of list you'll see the Pro Micro board as shown here:

- Go ahead and select that board as shown.
- Back to the [Tools] menu and down the the [Processor] menu item. By default, it will have selected the old 3.3 volt board and we are using the new board that is 5 volts.
- Go ahead and select the 5v board and we are all set up.

Ready to Write Arduino Code
Now we're ready to write our Arduino code which will receive the data off the serial line (incoming Rx) and write that data to the USB Keyboard. I grabbed some code from an example at the SparkFun site and altered it accordingly. You can see the original code at : Turn your ProMicro into a USB Keyboard/Mouse - SparkFun Electronics[^] You can get the code by downloading the Arduino Sketch file that is attached to this article (sendKey.zip).
#include "Keyboard.h"
int incomingByte;
boolean isWriteMode = false;
int writeModeByte[2];
int counter = 0;
void setup()
{
Serial1.begin(9600); }
void loop()
{
if (Serial1.available() > 0) {
incomingByte = Serial1.read();
if (!isWriteMode)
{
writeModeByte[counter] = incomingByte;
if (writeModeByte[0] == 38) {
isWriteMode = true;
}
}
else
{
Serial1.print("I received: ");
Serial1.println(incomingByte, DEC);
if (incomingByte != 0)
{
Keyboard.write(incomingByte);
incomingByte =0;
}
}
}
}
Not Much to the Code
Include File
The first thing to take note of is the special include file. The example at the SparkFun site is wrong on that and your sketch won't compile. Make sure you have it in double-quotes as I have it and it'll work with the normal Arudino IDE installation.
There's not much to this little sketch. Basically we set up the Serial1 (uart - universal async receiver/transmitter) which are the Rx and Tx pins on the Mega chip. After that we go into a loop and check every byte that comes in. Notice, after that we actually write -- via Serial1.print() -- back to the uart so that we can connect a serial monitor and see what the device is getting also. But, that's not the important part.
USB HID Keyboard
The important part is where we get the bytes from the serial line and then write them to the keyboard (over the USB connection). It's simple with the keyboard library provided by Arduino.
It's just that one line that does the work for us: Keyboard.write(incomingByte);
That's all there is to it. Let's look at how easy it is to wire up the Bluetooth module to the Pro Micro board now.
Wiring Up the Device
Now we just have to wire up the Bluetooth module serial lines to the Pro Micro's serial lines. That's very easy since it's just two wires. We will also wire up the Bluetooth to the Pro Micro's convenient VCC (power) and GND (ground) lines so that the Bluetooth is powered off of the USB connection when the Pro Micro is plugged into the USB port of a computer. It really couldn't be much more simple than this.
Here's the working prototype on my desk. Not a great picture, but it gives you the idea and next I'll show you the Fritzing circuit so you can tell what is connected.

All Those Wires
Basically, the Pro Micro is powered off the USB (from the computer). I've attached to the VCC pin on the Pro Micro so we can power the Bluetooth module. Then I've connected the Rx of Pro Micro to the Tx of the Bluetooth module and the Tx of the Pro Micro to the Rx of the Bluetooth. That creates a complete serial connection.
Most of the wires are just so I can get things to stay in place easily while it sits on my desktop. Of course, later we will want a complete product that is wired and soldered together and all we have to do is plug into the computer's USB port.
Here's the schematic (which is much more clear about what is connected).
Fritzing Schematic
It's a very easy circuit to wire up. Of course you'll also connect the USB cable from the Pro Micro to your computer.

Now we need our Android app which will generate our strong passwords and allow us pair with our device and send our passwords to it.
The Android App: DrawPass
Note: For this article, I just have the initial prototype version of DrawPass, but I will be updating it within the next one to two days. You can get the download the source (attached to this article) and generate hash passwords with it, but there's much more to do.
Prototype Android Code
I've altered the btFinder from my previous article so that I can connect to a Bluetooth device and send a message.
I've used this app to send messages that are then typed by the BlueKeySafe device onto your computer. It will allow you to see the Pro Micro / BlueKeySafe in action actually receiving data over Bluetooth and typing the characters on your screen.
You can download that code also and try it out. It looks like the following. Type some characters in the text box and hit the Send key, after you connect to your Bluetooth module.

How To Use the App To Test
To use the app, follow these steps:
- choose the Bluetooth device that you are going to send to (from the list of items) -- when you tap one, a message will appear at the bottom of the screen as it initially connects to the device. This is the Bluetooth device that is connected to the Pro Micro via Tx/Rx.
- Make sure your connected computer is sitting in a text document (Notepad) or something so when the characters come in you'll see them there.
- EDIT - This step has been added -- You must send an & (ampersand -- ascii 38) first to tell the Pro Micro that it should start writing following chars to the keyboard.
- Type a message in the editText box (as shown)
- Press the [Send] button. The message will appear on your computer.
Conclusion 1
You can see that this is a working prototype that needs a bit of clean up so it will work extremely easily for the end-user. I will do that over the next few days. I will also be creating a standalone device which easily plugs into the USB and has everything nicely encased (instead of bare wires hanging out everywhere).
More Thoughts: Advanced Ideas
Benefits of BlueKeySafe
- Now, you can run one app (DrawPass) on any device (an iOS app is coming as soon as I can get a Mac) and you never have to type a password again.
- Install the BlueKeySafe on a computer and multiple phones or devices can pair with it. Of course, only one device can connect at a time so that keeps it all safe. You can install these in public libraries, coffee shops, company workstations and kiosks and give your customers the convenience of signing into their sites via sending their password over bluetooth.
- To pair with the device you have to know the Bluetooth 4-digit code and you have to physically press a button to put it into pairing mode. That means you can keep unwanted users from pairing with the device if you want.
- Admins who have to manage large numbers of machines can now enter in the text key to identify the computer and/or service they are generating a password and DrawPass will track all of it for you. Passwords are not saved anywhere and the hash is generated each time you press the Gen Password button. That's safer. Now, if you have 15 computers in a room and they have a BlueSafeKey attached, you could just send to that device. Or, more likely, if you are connecting via remote desktop, you simply click in the password text box on the target machine and press send in the app. Your long and strong password is typed in for you.
Now let's move into how I've developed the BlueKeySafe because I am betting you are grinding your gears in anxious anticipation of destroying all passwords.
Security Concerns
Of course, immediately, there are many who do not understand security entirely and they will begin to murmur. "This is dangerous!! This is a security hole."
No, bad and weakly created passwords are the security concern.
But let's look at a few things that are bound to come up.
- Bluetooth can be hacked. Well, so far it hasn't been and the new Bluetooth is encrypted. So, until it has been officially hacked then we are okay. Anyways, that would mean someone is in the physical area with the Bluetooth cracker. Possible, but less likely than Internet anyways.
- Pasting passwords from the clipboard is terribly dangerous and it makes my head hurt. People believe this to be so, however, the clipboard is quite protected. If you have a trojan virus it is more likely that it has installed a keylogger and it's grabbing your keystrokes already so you are already pwned. Keyloggers are easy and the most often used thing so the clipboard thing isn't really bad. Read a bit and find out.
The Final Frontier: It Gets Even Better
All-in One Trinket
Now, imagine I create a small trinket which is Bluetooth-enabled and has an Atmel chip which can calculate the SHA-256 hash. Next, I allow the user to smply push a button on the trinket and it generates the hash (strong password) and sends it over Bluetooth to the BlueKeySafe it has been paired with.
Note: (The challenge here will be powering the Bluetooth module via battery. R/F is an energy eater compared to the ATMega chips which consume relatively little at 1Mhz.
On the receiving end, everything works exactly the same so the user can sign into his computer easily.
Press A Button On Trinket For Receive Mode: Update Salt
However, on the trinket side, you can press a button to put the trinket into receive mode (or possibly connect the trinket to a USB port) so the user can update the salt at any time. That means the user has a device that contains a unique salt that exists nowhere else in the Universe. Additionally the trinket will generate the hash off of that salt and send it to the user's paired BlueSafeKey.
RADDevus says:
Now the user can generate a globally unique cryptographically strong hash at any time and all the user has to do is press a button any time she wants to generate the hash password.
Only Place the Password Exists: The Trinket
Also, the only place the password exists (can be reproduced from ) is the trinket.
Oh No, What If the User Loses the Trinket?
That's right, she'd never be able to log in again -- never be able to reproduce the hash again.. If you're worried about that then create a backup trinket and keep it in a safe place. Just make sure that every time you flash both trinkets with the new salt so they stay in sync.
Scenario: Providing Temporary Visitor With Access
Let's say you have a visitor to your company who you want to give access but you don't want them to have to create a (possibly weak) password. Instead, assign them a userId, give them a trinket and allow them to sign on using that. Done. Easy. Just as it should be. No more weak passwords allowed in your systems!!
Points of Interest
While reading this article, I viewed CP's Insider News and the following article had been posted:
Microsoft won't fix Windows flaw that lets hackers steal your username and password | ZDNet[^]
Here's the relevant quote from that article:
ZDNet said:
To exploit this, a hacker has to trick a user into visiting a specially-crafted web page in Internet Explorer or Edge (on Windows 10) that points to their own network share. The browser will silently send usernames and hashed passwords to the network share, which can then be scooped up and stolen. If passwords are weak, they can be easily unscrambled and used to log in to user accounts.
This is the exact problem that DrawPass and BlueKeySafe solve for you. They make it so your passwords are extremely strong and cannot be cracked easily and probably cannot be cracked realistically.
Passwords Must Be Destroyed!!
- Users are forced to maintain far too many passwords. It is getting ridiculous out there. I have at least 30 different accounts with 30 different passwords.
- People use the same password on numerous sites because there are too many to memorize.
- Users create weak passwords because they have too many passwords and can't remember them.
- Users write their passwords on sticky notes and put them under their keyboards because they can't remember them.
- Users have too many passwords and they can't remember them all. This has driven many users to create logbooks (printed docs, handwritten notebooks and spreadsheets) containing their passwords and sites. Terrible!!
- Good (stronger) passwords can be extremely difficult to type on phones. This is no longer a problem because you will generate your password from the app on your phone and paste it into the site's password field. And, the password will be extremely strong -- based upon a cryptographic hash algorithm. You'll have one app to generate (not store) your passwords whether your logging in on your phone or on your desktop, laptop or other device.
- Some admins have multiple machines with multiple services and passwords numbering in the hundreds that they have to keep track of. No more of that! Generate your password and send it to the intended target via Bluetooth.
Conclusion
I'm the Guy Who Has Destroyed Weak Passwords
There is no reason that anyone should ever make up her own password ever again. It is dangerous and monotonous and only the ignorant user would ever do such a thing again. Administrators should immediately disallow passwords that are less than 25 characters and any passwords based upon natural language words for there is no longer any need to ever memorize a password again. Never!
The only reason we use word-based passwords is because humans require mnemonic devices so they can remember their passwords.
With this system in place there is never again a need to memorize a password because you never need to memorize or type one again.
Was That A Bit Extreme?
Probably not since this is the #1 security hole in the world of IT.
Parts List
- Bluetooth module Amazon.com: DSD TECH HC-05 Bluetooth serial pass-through module wireless serial communication [^]
- Pro Micro board - Amazon.com: SparkFun Pro Micro - 5V/16MHz[^]
History
Update Notes
2016-08-06 : I've altered the Sendkey.ino file and updated the code in this article. The previous code would read random bytes off the serial line and write them to the user's keyboard before the Bluetooth connection was made. This caused garbage to be sent to the user's computer -- instead of the expected data sent from a paired device.
Release Notes; To fix this issue, the Arduino code looks for a start char now (ampersand & ascii decimal 38 value). When it sees that value, it knows you want to go into write mode and all data it receives on serial line after that will be written to the keyboard.
Initial release and entry into the IoT Contest : 2016-08-05
Future Plans
I will be updating all of the software to a fully working example over the next few days. Please keep checking back for updates.
