Several weeks ago, one of my legacy web applications written in Classic ASP underwent a security scan/evaluation. The report indicated that the application contains server error response vulnerability. I had already configured the IIS to redirect the HTTP 500 - Internal Server Error to the custom error page. The users are seeing the custom error page instead of error details. So, what are we missing here? We started to debug the application by using Fiddler and found out that the application was returning status code 500 instead of 200.
Figure 1
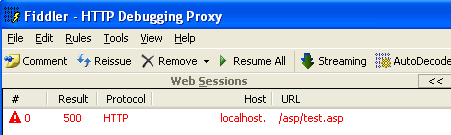
The report indicates that this exposure will allow the attacker to distinguish between valid and invalid request attempts. After spending some time researching for the solution, I found this article "How Web site administrators can troubleshoot an "HTTP 500 - Internal Server Error" error message on IIS 4.0 or on IIS 5.0"". I have error logging mechanism, email notification, etc. in the custom error page, the easiest solution is to add the following line on top of the custom error page.
Listing 1
Response.Clear()
Response.Status ="200 OK"
The first line will erase any buffered HTML output and ensure that the page is displaying a clean error page. The second line specifies the value of the status line returned by the server. Load the page that throws HTTP 500 - Internal Server Error again, and we should see the result similar to figure 2.
Figure 2

If your website is being audited and you come across this sort of situation, this could be one of the solutions. Hope someone will find this information useful.
References
