↵
Theme
This article series will explain using Jenkins for CI and CD of an ASP.NET Core web application on the local development environment, publishing the web application to Azure Web App Service and configuring Jenkins on Azure for continuous integration and continuous deployment of the hosted application. GitHub will DevOps as a source control repository. We’ll create a pipeline using Jenkins that fetches the code from GitHub, builds the code, runs the tests and deploy the package. This will be a repetitive task on each commit to the code located on GitHub.
In the first article of the series, we learned about the concepts, terminology, technologies involved, installing Jenkins, creating ASP.NET Core application and continuous integration of ASP.NET Core application using Jenkins via two approaches, i.e., pipeline approach and freestyle project approach. In the second article, we published the ASP.NET Core application to Azure App Service and Configured Jenkins on Azure.
In this article, we’ll focus on Azure Active Directory and Service Principal and integrate Jenkins with Azure Service Principal before we move on to CI/CD of ASP.NET Core application on Azure using Jenkins Azure Pipeline.
Roadmap
Following is the roadmap we would be following to completely learn end to end development and configurations of Continuous Integration and Deployment (CI/CD) of ASP.NET Core Application on Azure Web App using Jenkins.
Prerequisites
Go through the first two articles of the series before starting this article.
Following are the prerequisites for developers to have on their machines before getting started:
- Visual Studio 2017/2019
- Dotnet 2.1 SDK installed
- Azure Subscription Free/Paid
- Java 1.5 or higher
- Git account
- Git for Windows
Azure Active Directory and Service Principal
The next step is to create an identity for our application as it needs access to our Azure web app. This identity will serve as a service principal that could be assigned certain permissions to operate on the app.
Create an Azure Active Directory and Service Principal
- In the Azure portal, click on Azure Active Directory and then on App Registration as shown below:
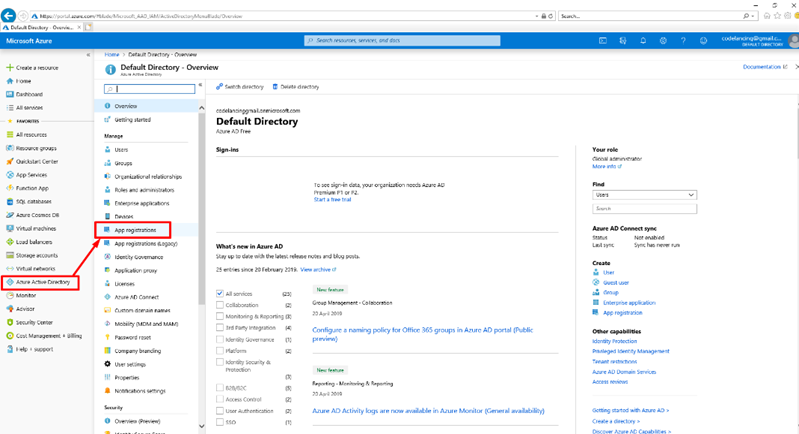
- Click on New Registration to create a new app registration.

- Provide a meaningful name. For example, I provided
jenkins_sp and select the first option for the supported account types, i.e., Account in this organizational directory only.

- Click on Register to create this new Azure AD and service principal.
- Navigate to the newly created application, i.e.,
Jenkins_sp.

Integrate the Application to a Role
To get access to the Azure resources, the application needs to be assigned to a role. For example, if in the Azure subscription, we assign the role to a resource group, then all the resources in that resource group will inherit that role and its permissions.
- Navigate to the Subscriptions in the Azure portal. Select the subscription. For example, I have only one subscription, and if I select that, all the resources in that subscription will inherit the role and permissions assigned.

- Once selected, the subscription page will open to the right.

- Select Access control (IAM).

- Select Add role assignment.

- In the Add role assignment form, select Role as Contributor, assign access to Azure AD user, group, or service principal. In the Select options, search by typing Jenkins and we see our
jeninks_sp, i.e., our service principal. Choose that and save.

- Click on the newly created app registration and on the overview page, copy the following values to a Notepad as they would be used while assigning a service principal to Jenkins.
- Application (client) ID
- Directory (tenant) ID
- Click on Certificates & secrets and add New client secret. Provide it a name and copy the value of the client secret created.

Now, we need to provide this service principal to the Jenkins running on the URL to have access over Azure resources on the selected subscription.
Integrate Jenkins with Azure Service Principal
- On the running Jenkins URL, navigate to Credentials -> System -> Global credentials and click on “Add Credentials”.

- Select Kind as Microsoft Azure Service Principal and fill in the following fields:
- Scope: Global
- Subscription ID: Your Azure subscription ID
- Client ID: The copied Application (client) ID from the service principal app
- Client Secret: The copied value of the secret certificate
- Tenant ID: The copied Directory (tenant) ID from the service principal app
- Azure Environment: Azure
Time to integrate Jenkins to the service principal created on the Azure portal.

Click on the verify service principal button to verify the details and connection. Once it says, Successfully verified…, click OK.

Conclusion
In this article, we focused on Azure Active Directory and Service Principal and integrating Jenkins with Azure Service Principal. In the next and last article of the series, we’ll see how to enable CI/CD of ASP.NET Core application on Azure using Jenkins Azure Pipeline.
History
- 27th November, 2019: Initial version
