Introduction
Hiding sensitive response headers may not be the most important security measure that you can take, but it is one extra layer of security according to defense in depth security principle. By default, ASP.NET applications reveal too much information about its platform and version, and this information makes an application vulnerable to zero-day bugs. Suppose a new bug will be discovered tomorrow in one of the components that we are using in our application, if our app readily discloses its version and platform, then a hacker can use this information and find an easy exploit for it or a bot can search the internet for the sites with that insecure component. So it's best to obscure the components and framework versions and the whole platform that we are using if possible. This adds one more layer of security to our site and the less info disclosed about a site, the more secure we are.
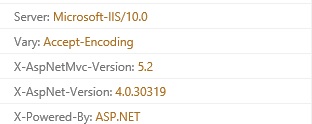
In this post, I'm going to show you how to hide all of your ASP.NET MVC response headers from Server to MVC version and so on. Some of them like X-AspNetMvc-Version and X-AspNet-Version are pretty easy to hide, but some of them like Server require a little more work.
Remove the X-AspNetMvc-Version and X-AspNet-Version Header
There is more than one way to remove the X-AspNetMvc-Version header, you can either remove it through MvcHandler in Application_Start() like so:
protected void Application_Start()
{
MvcHandler.DisableMvcResponseHeader = true;
}
or you can disable it by removing it in Application_PreSendRequestHeaders():
protected void Application_PreSendRequestHeaders()
{
Response.Headers.Remove("X-AspNetMvc-Version");
Response.Headers.Remove("X-AspNet-Version");
}
We can also remove the X-AspNet-Version with the previous method, but we can't remove the Server header. If we use this method, the Server header disappears for pages header but when someone clicks on static files like CSS or JS, he/she still can see the Server header, to truly get rid of Server header, we need to write an HttpModule for it.
Remove the X-Powered-By Header
We can't remove the X-Powered-By header in Application_PreSendRequestHeaders(), to remove it we need to add a customHeaders in Web.config like so:
<system.webserver>
<httpprotocol>
<customheaders>
<remove name="X-Powered-By">
</remove>
</customheaders>
</httpprotocol>
</system.webserver>
Remove the Server Header
In the previous section, I told you that you can't simply remove the Server header in Application_PreSendRequestHeaders() and if you do, the Server header will be partly removed but not completely, and if you click on a static file like CSS or JS file in your developer tool, you can see the Server header. In order to remove the Server header properly, we need to write a class for it and add it as a modules in system.webServer section in web config, just add this class somewhere in your project:
public class RemoveServerResponseHeader : IHttpModule
{
public void Init(HttpApplication context)
{
context.PreSendRequestHeaders += OnPreSendRequestHeaders;
}
public void Dispose() { }
void OnPreSendRequestHeaders(object sender, EventArgs e)
{
HttpContext.Current.Response.Headers.Remove("Server");
}
}
And then add this class as a modules in system.webServer part of your Web.config file, like so:
<system.webserver>
<modules>
<add name="CustomHeaderModule" type="VectorShop.Helpers.RemoveServerResponseHeader">
</add>
</modules>
</system.webserver>
That's pretty much it. Now, when I inspect my response headers for any type of file, I don't see any header that can reveal what platform I'm using.
But an attacker can still find out you're using ASP.NET MVC by inspecting your output HTML by looking for something like anti forgery token or your cookies for specific cookie names or if you use Webform by looking for view states, but that's far better than revealing not only your platform but the specific version that you're using. CodeProject
