Intel® Developer Zone offers tools and how-to information for cross-platform app development, platform and technology information, code samples, and peer expertise to help developers innovate and succeed. Join our communities for Android, Internet of Things, Intel® RealSense™ Technology, and Windows to download tools, access dev kits, share ideas with like-minded developers, and participate in hackathon’s, contests, roadshows, and local events.
Contents
Conclusion
About the Author
References
High Performance and Security Software-Based Encryption by Intel® Advanced Encryption Standard New Instructions and Intel® Secure Key7
To protect the safety of sensitive information or the runtime code security, cryptographic algorithms and Address Space Layout Randomization (ASLR) related technologies are widely used at the application level and OS level.
Intel® Secure Key
When generating a key pair or to create a random address space, a true random number generator is better than a pseudorandom number generator. Intel® Secure Key provides an Intel® x86 instruction RDRAND to implement a high-quality random number generator.
The RDRAND instruction is an innovative hardware approach to high-quality, high-performance entropy and random number generation. It follows the cascade construction RNG (random number generator) model, using a processor resident entropy source to repeatedly seed a hardware-implemented CSPRNG (cryptographically secure pseudorandom number generator). Then the RDRAND instruction can generate the random number that is compliant to NIST SP 800-90A and can be treated as a true random number generator for the most common cases.
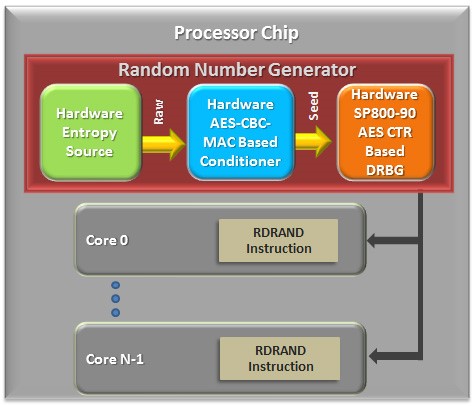
Figure 1. RDRAND instruction gets the number from an internal hardware random number generator.
There are many ways to use RDRAND:
- Utilizing the RDRAND instruction in assembly code directly or inline assembly in C/C++.
– rdrand %edx
– unsigned long therand, err;
asm volatile("rdrand %0 ; setc %1"
: "=r" (*therand), "=qm" (err));
- Library from Intel (librdrand)
- Written in C / C++
- Supports Windows*, Linux*, OS X*
- Libraries from a third party
Intel® Advanced Encryption Standard New Instructions
Intel® Advanced Encryption Standard New Instructions (Intel® AES-NI) is one of the most popular symmetric encryption algorithms. It is widely used to encrypt the data in memory, local storage and network communication packets to keep privacy safe from memory/file dump and network sniffer attacks.

Figure 2. Encrypt the communication channel using AES.
To increase the safety margin, it is recommended that encryption should use multiple rounds of AES which is equal to increasing the length of the AES encryption key. In 2010, Intel introduced a new set of instructions (Intel AES-NI) that offers full hardware support for Intel AES Encryption and Decryption to increase the performance and lower the memory requirement. Currently almost all of Intel’s desktop or mobile processors support Intel AES-NI. The diagram below shows the significant performance increase compared to pure software implementation.
HW: Intel® Platform, Bay Trail FFRD8 PR1 OS: Android* 4.4, OpenSSL* native C API
| MODE (CBC/256)
| File size
| AES-NI Enabled
| AES-NI Disabled
|
| Encrypt
| 351 MB
| 2.89 Sec
| 14.59 Sec
|
|
| 56 MB
| 0.48 Sec
| 2.63 Sec
|
| Decrypt
| 351 MB
| 1.76 Sec
| 19.78 Sec
|
|
| 56 MB
| 0.29 Sec
| 3.16 Sec
|
- Encrypt: nearly 5x performance improvement
- Decrypt: nearly 11x performance improvement
- Reduced about 40% power consumption
|
Figure 3. The performance comparison on the Intel® Atom™ processor Z3770 (code-named Baytrail) mobile platform.
Today most of mainstream operation systems provide native support to Intel AES-NI. When an app is calling cryptography API provided by the OS level such as Windows CNG API and Android* Javax.crypto java class, the low-level driver will use Intel AES-NI automatically to accelerate the performance. Meanwhile, many third-party libraries, like OpenSSL* 1.0.1, Intel® Integrated Performance Primitives crypto library, Crypto++ etc., are optimized to take advantage of Intel AES-NI.
Vitality Check by Intel® RealSense™ Camera Depth Sensor
Facially-based login features are widely used in people’s daily life. People use their faces to unlock their Android phone and personal computer devices. Since the camera used by the face recognition application is a traditional 2D optical camera, it cannot distinguish whether the picture it shoots is from a real face or a photo. So a hacker could also log in to the device using a paper with the printed user’s face.
The Intel® RealSense™ camera is a depth-camera solution that enables exciting new user experiences8. One of its key features is to digitally capture 3D objects and people. It can also be used as vitality detection in some biometric factor recognition scenes to improve security. When the optical camera captures the user’s face, the depth camera can also simultaneously get the depth information of the face. This facial geometry information can be easily used to determine whether the captured picture is a person or a flat piece of paper.

Figure 4. 3D face geometry from the depth camera from the Intel® RealSense™ camera F200.

Figure 5. Printed paper has a flat geometry from the depth camera from the Intel® RealSense™ camera F200.
Conclusion
In general, biometric authentication is different from password authentication. As biometrics are irrevocable, this new authentication approach requires more strict safety protection.
Intel offers various hardware-based security techniques inside Intel processor-based desktop and mobile platforms. These techniques can help biometrics recognition solution providers offer more secure biometric authentication scheme without adding hardware costs.

Figure 6. The yellow areas show how to improve the security of a biometrics recognition app on Intel® platforms.
About the Author
Jianjun Gu is a senior application engineer in the Intel Software and Solutions Group (SSG), Developer Relations Division, Mobile Enterprise Enabling team. He focuses on the security and manageability of enterprise application.
Zhihao Yu is an application engineer in Intel Software and Solutions Group (SSG), Developer Relationship Division, responsible for Intel® TEE technologies enabling and supporting secure payment solution based on Intel® platforms.
Liang Zhang is an application engineer in Intel Software and Solutions Group (SSG), Developer Relationship Division, responsible for supporting enterprise apps and Internet of Things developers based on Intel® platforms.
References
- TEE System Architecture v1.0: http://www.globalplatform.org/specificationsdevice.asp
- Intel® Software Guard Extensions (Intel® SGX), ISCA 2015 tutorial slides for Intel® SGX: https://software.intel.com/sites/default/files/332680-002.pdf
- Using Innovative Instructions to Create Trustworthy Software Solutions: https://software.intel.com/en-us/articles/using-innovative-instructions-to-create-trustworthy-software-solutions
- Intel® 64 and IA-32 Architectures Software Developer Manuals: http://www.intel.com/content/www/us/en/processors/architectures-software-developer-manuals.html
- Ravi Sahita and Uday Savagaonkar. "Towards a Virtualization-enabled Framework for Information Traceability (VFIT)." In Insider Attack and Cyber Security Volume 39 of the series Advances in Information Security, pp 113-132, Springer, 2008.
- Intel® Identity Protection Technology (Intel® IPT): http://ipt.intel.com/Home
- INTRODUCTION TO INTEL® AES-NI AND INTEL® SECURE KEY INSTRUCTIONS: https://software.intel.com/en-us/node/256280
- Intel® RealSense™ technology: http://www.intel.com/content/www/us/en/architecture-and-technology/realsense-overview.html
