Introduction
This article explains about how to enable a secure connection from BizTalk server to any other external system using HTTPS and TLS 1.0 protocol. It also mentions certain challenges we faced and how to overcome those issues. It takes an example of payment gateway to which the BizTalk Server interacted.
Background
The application interacts with external payment gateway server that transfers files securely to and fro. The details transferred are payment details which need security to prevent intrusion or hacking by any third party who have access to the network. The functionality of the BizTalk applications are as follows:
The business of the system is online insurance policy purchase. The policies are purchased by users using web portal. In Saudi, there are two types of payment options: SADAD (Global Payment Gateway - https://en.wikipedia.org/wiki/SADAD_Payment_System) and Credit Card. SADAD is a centralized payment authority in Saudi which is used for managing payments/transactions by the users without any bank account or credit cards.
When payment option is selected as SADAD, then a unique SADAD number is generated and it will be given to the user. The user can then use this unique number and then make a payment within stipulated number of days such or 3 or 10 days. The payment can be made in bank or online using the given SADAD number.
The insurance company had BizTalk integrations that used to manage transfer of data related to payment:
- Bill Upload - The bills will be uploaded to the central payment gateway using this application. This happens in real-time whenever any purchase of policies are happening using the web portal.
- Payment Notification - The central payment gateway will be giving notification to our company whenever payment has been completed by the user for the given
SADAD numbers. When the notification arrives, BizTalk updates the internal system that the payment is done and then enables to generates he policy.
Both of the above integrations use HTTPS and TLS 1.0 with security certificate. Initially, they used SSL and we upgraded to TLS from SSL.
Applications and Security Settings
The payment gateway and BizTalk server communicate using HTTPS/TLS using certificates. The certificate is embedded with the private key and should be obtained from the Certificate Authority. The generation of certificate is done using the following process.
- Create a Certificate Request from IIS in the BizTalk server which you want to connect to the payment server.
- In IIS, Expand the “ServerName” Select “Server Certificate”, and double click.
- Click on “Create Certificate Request” in the right side. Fill the Certificate needed Information, and click “Next”. Now the certificate request file is generated, and the private certificate is stored in the server.
- Send the "Certificate request file" to a certificate authority, to generate a certificate.
- Receive the certificate from the Certificate Authority and import it in our server.
- The certificate authority will send you back the certificate file with extension cer or crt. Change the file extension to cer.
- In IIS, Expand the “ServerName” Select “Server Certificate” Click on “Complete Certificate Request” in the right side. Type the full path of the certificate file received from the certificate authority, and type the “Friendly name” used while creating the certificate request file (The friendly name should match with the "Common Name" in the Certificate Request Form). Click OK. The certificate now is created.
- To assign the certificate to the web sites in the IIS:
- In IIS, Select the web site where the BizTalk application resides. Click on “Binding…” and Add new binding with HTTPS.
- Select HTTPS from the Type, select the newly imported certificate from the “SSL certificate”, and change the port if needed.
- Click “View” in “Directory Security”. A certificate page will open, you must see at the bottom of the page a key image followed by “You have a private key that corresponds to this certificate” statement. (If you do not see it, that means you do not have the private key).
Notes: For our project, the purpose of the certificate was to include the following:
- Ensure the identity of a remote computer
- Proves your identity to a remote computer
- Protects e-mail messages
- Allows secure communication on the internet
The certificates should also be added in the appropriate certificate stores such as Trusted Root, Intermediate Certificate Authorities and Personal using the MMC. After importing, verify that the certificate tree structure is visible as Root, Intermediate and Site Certificate.
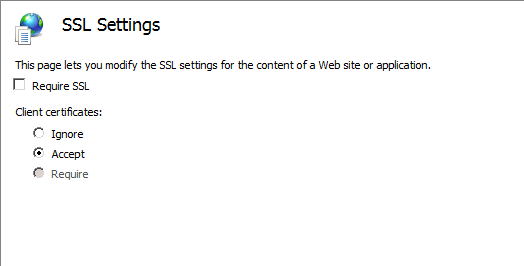
In the SSL Settings of each of the applications, in IIS, 'Use SSL' should be unchecked and the option 'Require Client Certificate' should be checked to allow authentication using client certificate.
Update the certificate thumbprint in BizTalk Send Port that is used to connect to the external server.

Disable the SSL protocols in the server and enable only the TLS, by modifying the following settings in the registry:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client]
"DisabledByDefault"=dword:00000001
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]
"Enabled"=dword:ffffffff
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]
"Enabled"=dword:ffffffff
After we changed the above settings, we tried invoking the interfaces, but got error like 'Forbidden Access'. So we went to the IIS log and checked the exact error code. It was 403 - Access Denied. Still checking the sub error code, we could see that it was 403.13, which means 'Client Certificate was revoked'.
Location of IIS Log: C:\inetpub\logs\LogFiles\W3SVC1
2016-02-04 07:24:17 <Target IP> POST /PaymentNotificationReceive/BTSHTTPReceive.dll
- 5755 - <Source IP> Mozilla/4.0+[en]+(WinNT;+I) 403 13 2148081683 18370
This means that the server was not able to confirm that the certificate was not found in Certificate Revocation List(CRL). Hence it will throw the error, when either the CRL URL mentioned in the certificate is not accessible or the client certificate was found in the CRL URL. In our case, the CRL URL was not accessible from the server system. Hence, we decided to disable this CRL check for this certificate.
This can be done by setting the following flag in the registry and do a restart of the server. After changing it and restarting, everything was working fine and our connection with the payment gateway was established successfully.
Registry Key to Disable CRL Check
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\HTTP\Parameters\SslBindingInfo\IP:Port]
"DefaultSslCertCheckMode"=dword:00000001
Command to show SSL certificates
netsh http show sslcert
Points of Interest
Certification Revocation List and how to disable the check in registry was a learning experience.
History
- 29th March, 2016: Initial version
