Introduction
Securing BizTalk WCF Receive Locations.
I would like to create a BizTalk WCF Receive Location, that utilizes SSL and requires that clients use a certificate for authentication. I also want to authorize the access to certain client certificates; so that not every client that uses a certificate issued by a trusted issuer, has access to the service.
Steps Involved:
These steps would be targeted towards BizTalk Server 2013R2 / IIS 8.5
-
-
-
-
Test the https URL. -- With this step your service is configured to use SSL. If you want to use windows authentication instead of client certificate authentication to authenticate and authorize access, go to step 11.
-
-
-
-
-
-
-
-
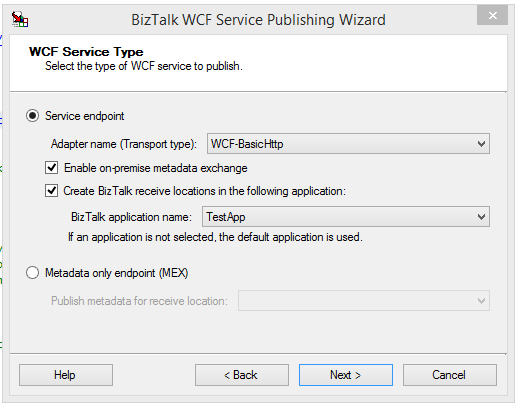
Using Visual studio, publish your schema as a WCF Service.
-
Enable Metadata exchange.
-
Create BizTalk Receive location.
-
-
-
Open Internet Information Services Manager.
-
Click on the server name in the connections column on the left and double click on the server certificates.

-
In the Actions Panel click on Create Self-Signed certificate.
-
Provide the details as in the below screenshot.
-
Click OK and you can see your certificate in the Server certificate panel. The Server certificate that we want to bind to our service is ready.<o:p>

- In IIS, Click on the Website your service is published to (Default website in my case).
- Click on Bindings in the Actions Panel.
- Click on 'Add' in the Site Bindings pop up.
- In the 'Add Site Binding' pop up, select https in Type drop down. Select the certificate created in previous step in the SSL Certificate drop down.
- Click OK.

- Click on your service/App under default website, double click on SSL Settings.
- Check the Require SSL check box. Choose Ignore radio button in the client certificates and click on apply in the Actions panel.

- Go to BizTalk Admin console and open the WCF Receive location created in the step 1.
- Click on Configure, go to security Tab, choose Transport from the Security mode drop down, leave the transport security credential to none and click OK.

- Back in the IIS; go to your application's virtual directory and open the Web.config file.
- In the behavior tag, change httpsHelpPageEnabled and httpsGetEnabled to true.
- Restart your website.
With this step your WCF Service is configured to use SSL. We will now test and then configure Client certificate authentication.
Note : Use full name of your machine instead of localhost in the url. Using localhost in url raises this error -- <o:p>
The security certificate for host <<full name of your machine>> does not match the name of the page you are viewing. In IIS server certificates, Check the "Issued To" part of the certificate you created in Step2. That should match full name of your machine. <o:p>
- Go to IIS, Click on your service/App under default website, double click on SSL Settings.
- Under Client certificates click Require and click on apply in the Actions panel.
- Anonymous Authentication must be enabled.

- Go to BizTalk admin console; in the WCF Receive location adapter settings, security tab, Change the transport client credential type to 'Certificate'.
- With this step the WCF Service is configured to use Client certificate authentication. But any client certificate issued by a trusted issuer can be used to access this service, provided the issuers root certificate is installed in your machine's "Trusted Root Certification Authorities".
- In the next steps we will setup authorization.
In this step we will first create a root certificate and then create a client certificate signed by that root certificate.
- Open Visual studio command prompt in Admin mode and browse to the location where you want to save the certificate files. (default path is c:\windows\system32 or c:\windows\sysWow64).
- Create a root cert: makecert -n "CN=TestRootCA" -r -sv TestRootCA.pvk TestRootCA.cer
- This prompts for a password creation; create the password. Install this certificate in the "Trusted Root Certification Authorities" of Local Computer on both the Client and Server machines.
- Create a client cert from the TestRootCA we just created.
- makecert -sk Clientcert -iv TestRootCA.pvk -n "CN=Clientcert_Test" -ic TestRootCA.cer -sr currentuser -ss my -sky signature -pe
- This client cert will be created in the Personal store of current user.
- E xport the client cert along with private key.
- Import it to the Current User Personal store of the client machine. You should have already imported the TestRootCA cert.
- Now that we have a client certificate, browse the service from IE using the client cert you just imported. You will be able to browse the service using any client cert that has a linked root cert on the server.
Note: If you get 403.16 - Forbidden. Your client certificate is either not trusted or invalid error, refer link
Add a new DWORD to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL Value name: ClientAuthTrustMode Value type: REG_DWORD Value data: 2
With this step we have configured and tested the https WCF service with client certificate authentication. Now we will configure authorization, so that only authorized client certificates can be used to access the service.
- Go to Control Panel, programs and features. Click 'Turn Windows Features on or off'.
- In the windows features pop up, navigate to Internet information services, world wide web services, Security.
- Check if features 'IIS Client Certificate mapping Authentication' and 'URL Authorization' are checked. If not, check them and click OK to install these features.

- Go to IIS, click on the website your service is published to (default web site) .
- Double click configuration editor.

- In the Configuration editor, Section drop down select 'IIS Client Certificate Mapping Authentication' under System.Webserver/security/authentication.
- Set the enabled flag to True.
- Click the ellipsis of manyToOneMappings field.

- Click on Add in the Collection Editor window.
- Enter values for description and name. Fill the UserName and password fields, use an account that has access to that machine. Providing wrong password in this box will give an authentication denied error when you call the service.
- Click on ellipsis in the rules field.

- In the popup window, click Add and enter the values as in below pic. matchCriteria is the CN value that you provided while creating the client certificate in step 6. Close these two windows and click Apply on the Configuration editor window.

- With this step you have mapped the client certificate you created in step 6 to a windows account. You can still call the service with any client certificate. If you use the mapped certificate the call will be authenticated. If you use a different client certificate the call will be anonymous.
- Next we authorize access to the account you just used in the previous step, so that the service cannot be called with any other certificate.
- Select your WCF Service in IIS and double click on 'Authorization rules'.

- Edit the existing rule and choose Specified users. Provide the account you used in the previous step and click OK.
- Last and Important step. Go to your Application pool in IIS and change the managed pipeline mode to classic.

- Restart you web server and call your service using different client certs. You will get Authorization error if you use any certificate other that the one you mapped in previous step.
- Following steps are for configuring windows authentication instead of client certificate on a SSL Service.
- Make sure Windows Authentication feature is installed. Check Programs and features.
- Go to Control Panel, programs and features. Click 'Turn Windows Features on or off'.
- In the windows features pop up, navigate to Internet information services, world wide web services, Security.
- Check if feature 'Windows Authentication' is checked. If not, check it and click OK to install these features.
- In IIS Select, select your service and double click authentication. Disable Anonymous and enable windows authentication.
- Select your service and Click SSL Settings, make sure Client certificate is set to ignore.
- Select your service and double click Authorization Rules.
- Edit the existing rule and choose Specified users. Provide the account you want to use to access the service and click OK.

- In BizTalk Admin console, go to adapter configuration, Security tab and update Transport client credential type to Windows.
- Last and Important step. Go to your Application pool in IIS and change the managed pipeline mode to classic.
- Restart your website and test.
