Introduction
This is a note on Linux Directory Structure & Users & Permissions.
Background
This is a note on Linux Directory Structure & Users & Permissions. Regardless of whether you are a new or an experienced Linux user, these subjects are easily forgotten and constantly revisited. In this note, I used a Linux Mint 18.3 Cinnamon 64-bit Virtual Machine (VM). You can get a Linux Mint VM by going through these steps. If you like other flavors of Linux, you can also get a CentOS VM.
Linux Directory Structure
The top-most directory in Linux is called the root directory or /. In a Linux system, you will normally see the following directories under the top-most root / directory.
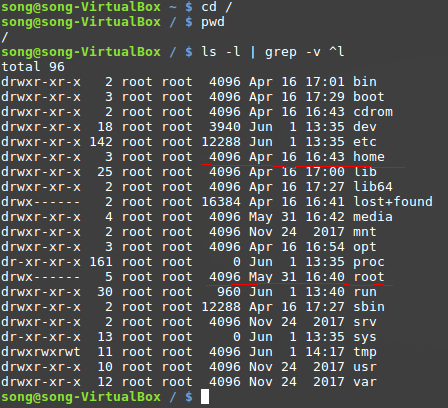
This structure is the so called Filesystem Hierarchy Standard. It is maintained by the Linux Foundation.
| / | Primary hierarchy root and root directory of the entire file system hierarchy. |
| /bin | Essential command binaries that need to be available in single user mode; for all users, e.g., cat, ls, cp. |
| /boot | Boot loader files, e.g., kernels, initrd. |
| /dev | Essential device files, e.g., /dev/null. |
| /etc | Host-specific system-wide configuration files.
There has been controversy over the meaning of the name itself. In early versions of the UNIX Implementation Document from Bell labs, /etc is referred to as the etcetera directory, as this directory historically held everything that did not belong elsewhere (however, the FHS restricts /etc to static configuration files and may not contain binaries). Since the publication of early documentation, the directory name has been re-explained in various ways. Recent interpretations include backronyms such as "Editable Text Configuration" or "Extended Tool Chest". |
| /etc/opt | Configuration files for add-on packages that are stored in /opt. |
| /etc/sgml | Configuration files, such as catalogs, for software that processes SGML. |
| /etc/X11 | Configuration files for the X Window System, version 11. |
| /etc/xml | Configuration files, such as catalogs, for software that processes XML. |
| /home | Users' home directories, containing saved files, personal settings, etc. |
| /lib | Libraries essential for the binaries in /bin and /sbin. |
| /lib<qual> | Alternate format essential libraries. Such directories are optional, but if they exist, they have some requirements. |
| /media | Mount points for removable media such as CD-ROMs (appeared in FHS-2.3 in 2004). |
| /mnt | Temporarily mounted filesystems. |
| /opt | Optional application software packages. |
| /proc | Virtual filesystem providing process and kernel information as files. In Linux, corresponds to a procfs mount. Generally automatically generated and populated by the system, on the fly. |
| /root | Home directory for the root user. |
| /run | Run-time variable data: Information about the running system since last boot, e.g., currently logged-in users and running daemons. Files under this directory must be either removed or truncated at the beginning of the boot process; but this is not necessary on systems that provide this directory as a temporary filesystem (tmpfs). |
| /sbin | Essential system binaries, e.g., fsck, init, route. |
| /srv | Site-specific data served by this system, such as data and scripts for web servers, data offered by FTP servers, and repositories for version control systems (appeared in FHS-2.3 in 2004). |
| /sys | Contains information about devices, drivers, and some kernel features. |
| /tmp | Temporary files (see also /var/tmp). Often not preserved between system reboots, and may be severely size restricted. |
| /usr | Secondary hierarchy for read-only user data; contains the majority of (multi-)user utilities and applications. |
| /usr/bin | Non-essential command binaries (not needed in single user mode); for all users. |
| /usr/include | Standard include files. |
| /usr/lib | Libraries for the binaries in /usr/bin and /usr/sbin. |
| /usr/lib<qual> | Alternate format libraries, e.g. /usr/lib32 for 32-bit libraries on a 64-bit machine (optional). |
| /usr/local | Tertiary hierarchy for local data, specific to this host. Typically has further subdirectories, e.g., bin, lib, share. |
| /usr/sbin | Non-essential system binaries, e.g., daemons for various network-services. |
| /usr/share | Architecture-independent (shared) data. |
| /usr/src | Source code, e.g., the kernel source code with its header files. |
| /usr/X11R6 | X Window System, Version 11, Release 6 (up to FHS-2.3, optional). |
| /var | Variable files—files whose content is expected to continually change during normal operation of the system—such as logs, spool files, and temporary e-mail files. |
| /var/cache | Application cache data. Such data are locally generated as a result of time-consuming I/O or calculation. The application must be able to regenerate or restore the data. The cached files can be deleted without loss of data. |
| /var/lib | State information. Persistent data modified by programs as they run, e.g., databases, packaging system metadata, etc. |
| /var/lock | Lock files. Files keeping track of resources currently in use. |
| /var/log | Log files. Various logs. |
| /var/mail | Mailbox files. In some distributions, these files may be located in the deprecated /var/spool/mail. |
| /var/opt | Variable data from add-on packages that are stored in /opt. |
| /var/run | Run-time variable data. This directory contains system information data describing the system since it was booted. In FHS 3.0, /var/run is replaced by /run; a system should either continue to provide a /var/run directory, or provide a symbolic link from /var/run to /run, for backwards compatibility. |
| /var/spool | Spool for tasks waiting to be processed, e.g., print queues and outgoing mail queue. |
| /var/spool/mail | Deprecated location for users' mailboxes. |
| /var/tmp | Temporary files to be preserved between reboots. |
Among these directories, the /root directory is the home directory of the user root. The home directories of the regular users are in the /home directory by default.

At this time, I am the only user with the user name song. The following are the directories under my home directory.

The Linux Users
Add a Linux User
Adding and deleting a user should be an easy task, but it is made difficult over the history. According to this note, we have at least two ways to add a user, namely adduser and useradd and they behave differently in different Linux distributions.
- Debian/Ubuntu - On Debian or Ubuntu systems, useradd is a command itself, and you can create users and define options to them using this command, and adduser is a perl script, that uses useradd to create the account, asking you the password, Full-name, phone, etc.
- Fedora or CentOS systems - adduser is just a symbolic link to useradd
- Gentoo systems - the same as in CentOS or Fedora, adduser is just a symbolic link to useradd
It seems that the useradd command is more consistent across the platforms, so I will use useradd in this note. To add a user in Linux, you can use the following command:
sudo useradd test-user-1
You can assign or make changes to a user's password by the following command:
sudo passwd test-user-1
If a user is currently logged-in, the user can change his/her own password without giving the username and without sudo.
passwd
You can also add additional information to the user, such as the full name by the following command:
sudo usermod -c "Test User 1" test-user-1
According to the useradd man page, the home directory of the user should be automatically added. But in my Linux Mint VM, it is not added. I need to add it manually.
sudo mkdir /home/test-user-1
sudo chown test-user-1:test-user-1 /home/test-user-1
After creating the home directory, the user can then smoothly login to the system by the given password.

Read the User Information
The user information is kept in the /etc/passwd file that regular users have read access to it by default.

You can read this file to find out the Linux users.

But the getent command is more commonly used to read the information in the /etc/passwd file. You can find the same information about the user song by the following command:
getent passwd song
Linux User Password
The user's password is kept in the /etc/shadow file that regular users do not have any permission to by default.

If you can sudo, you can take a look at it.

The password is kept as a salted hash that in theory is very difficult to decipher. You can get the same information by the getent command.
sudo getent shadow song
Delete a Linux User
You can delete a Linux user by the following command:
sudo userdel -r test-user-1
The -r option instructs userdel to also delete the user's home directory.

The Linux Groups
Add a Linux Group
If you can sudo, you can create a user group by groupadd.
sudo groupadd test-group-1
According to the man page, groupadd allows you to use the -p option to give the group a password. But from a lot of discussions, it is discouraged. The group information is kept in the /etc/group that a regular user has read access to it by default.

You can read the information about the Linux groups.

You can also use getent to get the same information.
getent group test-group-1
Delete a Linux Group
You can delete a user group by groupdel.
sudo groupdel test-group-1
According to the "groupdel" man page, the deletion may fail due to the following reasons:
- You may not remove the primary group of any existing user. You must remove the user before you remove the group.
- You should manually check all file systems to ensure that no files remain owned by this group.
Linux Group & User Associations
A Linux group can have multiple users and a Linux user can be assigned to multiple groups. If you have followed this note, you may have already deleted the test-user-1. If so, let us recreate it.
The Primary Group
To find all the groups a user belongs to, you can use the groups command. When a new user is created, a group of the same name is created. This user is added to the group by default and it is the user's primary group.

When this user creates a directory or a file, the group owner of the directory or the file is the user's primary group.

The information of a user's primary group is kept in the /etc/passwd file.

You can find the 1001 after the user's id matches the group id for the test-user-1 group.
The Secondary Groups
Besides the primary group, a user can be assigned to multiple secondary groups. Let us first create two empty user groups.

You can the usermod command to assign a user to a secondary group.
sudo usermod -a -G test-group-1 test-user-1

To list all the groups that a user belongs to, you can also use the id command, which gives the IDs besides the group names.

The list of the users in a secondary group is kept in the /etc/group file. At this time, the test-group-1 has only test-user-1 as its secondary group number.

You can remove a user from a secondary group by the gpasswd command.
sudo gpasswd -d test-user-1 test-group-1

Update A User's Primary Group
It is uncommon that you need to update a user's primary group. But if want to do it, you can use the usermod with the -g option.
sudo usermod -g test-group-1 test-user-1

As we know, the primary group is associated with the user in the /etc/passwd file, the secondary groups are associated with the user in the /etc/group file.
- If group A is associated with the user in both files, it is treated as the user's primary group. If we change the user's primary group to B, the group A will remain as a secondary group of the user.
- If group A is associated with the user in /etc/passwd file only, it is the user's primary group. If we change the user's primary group to B, the group A will no longer be associated to the user.
Linux Directory & File Permissions
With the Linux directory structure and users in mind, it becomes easy to look at the file and directory permissions. Most of the information in this section is from this note and you may want to take a look at it directly.

The Mode section tells us the permissions to the files and the directories for the user(owner), the group owner and other users.

According to this note, the read, write, and execute permissions on a file and a directory are interpreted differently.
For a file, the permissions are interpreted as the following:
- READ - Read permission allows a user to view the contents of the file.
- WRITE - Write permission allows a user to modify and delete the file.
- EXECUTE - Execute permission allows a user to execute a file (the user must also have read permission). As such, execute permissions must be set for executable programs and shell scripts before a user can run them.
For a directory, the permissions are interpreted as the following:
- READ - Read permission allows a user to view the names of the file in the directory.
- WRITE - Write permission allows a user to delete the directory, modify its contents (create, delete, and rename files in it), and modify the contents of files that the user can read.
- EXECUTE - Execute permission allows a user to access, or traverse, into (i.e.,
cd) and access metadata about files in the directory (the information that is listed in an ls -l).
The "chown" & User & Group Ownership
We can use the chown command to change the owner and the group owner of a file or a directory. According to the discussions here, the chown requires sudo.

If you want to change the owner only, you can use the following command:
sudo chown test-user-1 a-file
If you want to change the group owner only, you can use the following command:
sudo chown :test-group-1 a-file
The "chmod" & Permissions
The chmod can be used to set the permissions to a file or a directory. The following command will set the other users to have all the permissions to the file.
chmod o=rxw a-file

Where o represents other users. If you want to set the permissions to the owner and the group, you can use u and g, where u represents the owner user and g represents the group.

You can also use + or - to modify the permissions. The following command will remove the execute permission of the other users.
chmod o-x a-file

In Linux, there is a numerical representation for the permissions:
- 1 = Execute permission
- 2 = Write permissions
- 4 = Read permissions
Besides the 1/2/4, 3 = "Execute + Write", 5 = "Execute + Read", 6 = "Write + Read", and 7 = "Execute + Write + Read".
chmod 357 a-file

After setting the permissions to 357, the permissions on the file are the following:
- USER (OWNER) - Write & Execute
- GROUP - Read & Execute
- OTHER USERS - Read & Write & Execute
From my observation, only the owner can run chmod. The group owners and other users need sudo to run chmod.
The SUDOERS
In Linux we can have users who can obtain the root privilege by providing their own passwords. These users can perform the kind of work more than the regular users. These privileges are defined in the /etc/sudoers file. For example, in my Linux Mint VM, I am a SUDOER.

When I create the VM, I am added to the user group sudo. The sudo group is granted all the permissions in the sudoers file.

In my CentOS VM, it simply added the user song directly to the sudoers file.

It is discouraged to modify the sudoers file directly. If you need to make changes to the sudoers file, It is recommended to use the visudo command.
Points of Interest
- This is a note on Linux Directory Structure & Users & Permissions.
- I hope you like my posts and I hope this note can help you one way or the other.
History
- 31st May, 2018: First revision
