Introduction
High availability and scalability are big challenges in the IT world. Assume you are going to provide your private registry as service and you are expecting high traffic to your registry, then you have to carefully design your infrastructure to support the above items. In this article, we are going to see how we can use the Docker Swarm to implement the high availability and scalability for your private registry.
Docker swarm is a collection docker running nodes and joined into a cluster. Swarm has two types of nodes, one is a manager and another one is a worker. The manager uses the varies strategies to distribute the tasks among worker and itself.
Docker swarm services provide automatic scaling, distribution of traffic and storing sensitive data such as password, TLS certificates in secrets.
This is the final part of my private Docker Registry series and the following list shows the outline of the series:
To configure your private registry as a service, we have the following three major steps:
- Configure the Swarm
- Generate Secrets
- Run Registry as a Service
Configure the Swarm
For your private registry, you are going to create two clusters, one for the manager and another for the worker, but you can create as much as you want.
Configure Virtual Switch in Hyper-V
Hyper-V comes with windows 10 so there is no need to install any additional hypervisor like VirtualBox or VMware workstation, etc. on Win 10 machines. But Hyper-V requires a virtual switch to create a cluster and it is required only when you are using the Hyper-V. Do the following steps to create a virtual switch in Hyper-V.
- Open the Hyper-V manager.
- Click on Virtual Switch manager on the right side menu:
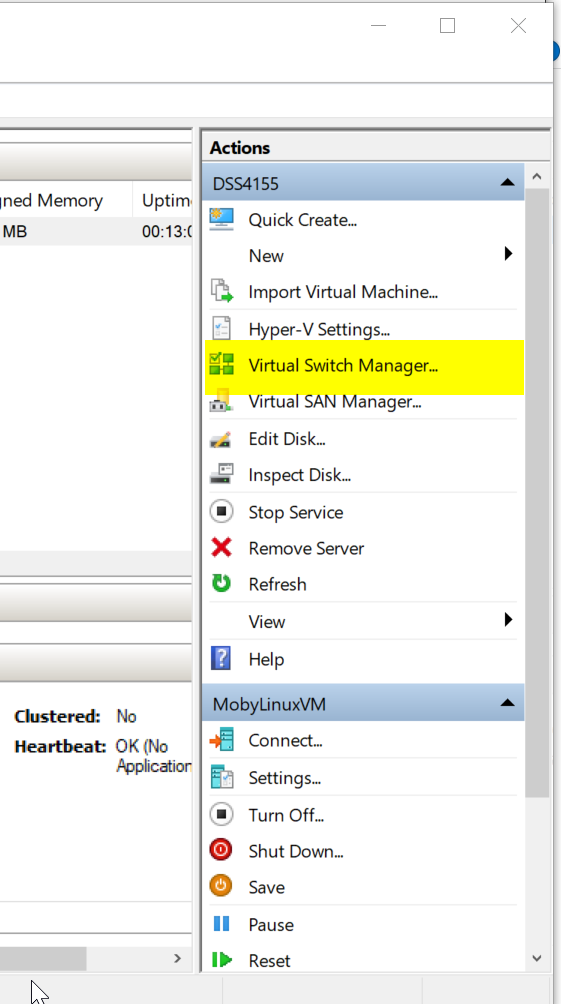
- Click on create Virtual Switch:

- Select External as type.
- Give it the name as
hyphub. - Select your host primary network adapter:

Create Swarm Nodes
- Open a PowerShell console (terminal in Linux).
- Create a manager node with the following command:
Windows 10:
docker-machine create -d hyperv --hyperv-virtual-switch "hyphub" hubmgr
Window 7/Linux:
docker-machine create -d virtualbox hubmgr

- Create a worker cluster with the following command:
Windows 10:
docker-machine create -d hyperv --hyperv-virtual-switch "hyphub" hubworker01
Window 7/Linux:
docker-machine create -d virtualbox hubworker01

- Check the status of newly created clusters:
Windows/Linux:
docker-machine ls
Configure Swarm
- Open a new PowerShell console in administrative mode (terminal in Linux).
- Type the following command to connect to the manager node:
Windows/Linux:
docker-machine ssh hubmgr

- Change the prompt terminal as Manager. You can change the prompt like this
PS1="Manager# ". - Type the following command to configure the swarm:
Windows/Linux:
docker swarm init

- Open a new PowerShell console in administrative mode (terminal in Linux).
- Type the following command to connect to the worker node:
Windows/Linux:
docker-machine ssh hubworker01
- Change the prompt terminal as
Worker. You can change the prompt like this PS1="Worker01# ". - Join to swarm with the following command:
Windows/Linux:
docker swarm join {join token} {manager ip}:{port}

- Once worker node successfully joins to the cluster, go back to the Manager console and check the node list with the following command:
Windows/Linux:
docker node list

- It shows two nodes, one is the manager and another one is the worker.
Generate Secrets
Docker swarm supports to store the sensitive information securely and shared across nodes in a cluster. In this section, we are going to see how to create and use the secrets for TLS certificate of your private registry (hub.docker.local).
- Open a new PowerShell console (terminal in Linux).
- Navigate to C:\localhub (remember we have created this folder in the first article of this series). For Linux, /home/localhub.
- We need to move our TLS files from the host machine to the manager node to add them into the secret bucket. Before moving the file, ensure manage has certs folder inside /home/docker. If it is not available, create it.
Windows:
docker-machine scp /C/localhub/certs/localhub.key docker@192.168.1.105:/home/docker/certs
docker-machine scp /C/localhub/certs/localhub.crt docker@192.168.1.105:/home/docker/certsy
- Go to manager console and navigate to /home/docker folder.
- Enter the following command to generate the secrets for TLS certificates:
Linux:
docker secret create localhub.crt certs/localhub.crt
docker secret create localhub.key certs/localhub.key

Run the Registry as a Service
Now we are ready to enable the registry service and do the following steps:
- Go to the Manager console.
- Type the following commands to add a label to the worker and it will help us to set the constraint to run the registry only on workers but it is optional:
Linux:
docker node update --label-add registry=true hubworker01
- Type the following commands, create service for registry:
Windows/Linux:
docker service create --name registry --secret localhub.crt --secret localhub.key
--constraint 'node.labels.registry==true' -e REGISTRY_HTTP_ADDR=0.0.0.0:443
-e REGISTRY_HTTP_TLS_CERTIFICATE=/run/secrets/localhub.crt
-e REGISTRY_HTTP_TLS_KEY=/run/secrets/localhub.key --publish published=443,target=443
--replicas 1 registry

- Repeat steps to pull and push an image from your private registry:
Windows/Linux:
docker pull alpine
docker tag alpine hub.docker.local/alpine
docker push hub.docker.local/alpine
docker rmi hub.docker.local/alpine
docker images
docker pull hub.docker.local/alpine
docker images
docker run hub.docker.local/alpine ls

Currently, we are using one replica because we have not set up the centralized storage so if you increase replicas count without configuring centralized storage, it will have an impact because the image will not sync between container. You need to setup bind-mounts for /mnt/registry with SSD or SND or storage drives or a directory from the manager node before increasing the replica. As a best practice, use more reliable and scalable storage model.
Conclusion
Throughout this series, we have learned how to create our own private docker registry to store the docker images, how to secure the registry and how to apply the high availability and scalability to the registry with help of Docker Swarm. Even though this series uses the private registry as an example, most of the concepts like storage customization, security, high availability, and scaling are common for other applications as well. Thanks for reading this article. I hope you found something useful. Please share your comments below.
