Introduction
This project is intended for Windows wireless network developers, and assumes the reader is familiar with the concept of packet injection, 802.11 frames, and IP protocols. The network driver in this package provides a means for developers to create 802.11 packets in user space and send them on the 802.11 layer. The package contains a network driver and an open source command line application. The command line application demonstrates how to use the Packet11 service via DeviceIoControl.
Background
Typically, packet injection is used to test wireless security or break WEP keys (airplay) with "software controlled packets". Although software controlled packets can be used maliciously, they can also provide a better user experience. Mesh networking and virtual access points are two potential and beneficial applications of managing wireless packets. Packet11 is the first step to providing software controlled packets for wireless testing and routing.
To the best of my knowledge, there are no other 802.11 packet injectors for Windows without special adapters (AirPCap). Packets constructed in the 802.11 layer are native to the wireless miniport. Linux has been able to modify native WiFi packets for ages and extend WiFi technology, i.e., MadWiFi. Having more control over native WiFi packets will also extend WiFi capabilities in Windows. Since Windows Vista, Network Driver Interface Specification (NDIS) 6 has given third party Windows developers a better opportunity to manage and extend WiFi adapter capabilities. However, creating and modifying packets in the 802.11 layer is undocumented for Windows.
Requirements
- Windows Vista or later
- Wireless adapter*
*I tested Packet11 on Atheros USB WiFi, Intel PCI WiFi and Rosewill adapters. All were able to send my custom packets. I recommend having a second wireless adapter in monitor mode to look at the packets as they are sent in the air.
Using the Code
I have implemented a new technique since this article was posted that allows a filter driver to originate 802.11 packets without modifying OS generated packets. Now, applications can create and send 802.11 packets using DeviceIoControl. Obviously, in order to use this function, the Packet11 driver must be installed before using this function. I have provided commands to install and uninstall the driver. The readme gives more details on this. Once the driver is installed, we can create and test a custom 802.11 packet.
To demonstrate, I used a probe request type to illustrate one possibility.
void * CreatePacket(
DOT11_MGMT_SUBTYPE subtype,
PUCHAR Source,
PUCHAR Dest,
PUCHAR Bssid,
ULONG packetsize
)
{
PDOT11_MGMT_HEADER pMgmtHeader = NULL;
PDOT11_PROBE_REQUEST pProbeRequest = NULL;
PDOT11_INFO_ELEMENT pInfoElement = NULL;
PDOT11_BASIC_RATE pBasicRate = NULL;
PDOT11_EXT_RATE pExtRate = NULL;
PVOID DataBuffer = NULL;
if(Source == NULL || Dest == NULL || Bssid == NULL){
printf("CreatePacket ==> null mac address \n");
return DataBuffer;
}
DataBuffer = malloc(packetsize);
pMgmtHeader = (PDOT11_MGMT_HEADER)(PUCHAR)DataBuffer;
pMgmtHeader->FrameControl.Version = 0;
pMgmtHeader->FrameControl.Type = DOT11_FRAME_TYPE_MANAGEMENT;
pMgmtHeader->FrameControl.Subtype = subtype;
pMgmtHeader->FrameControl.ToDS = 0;
pMgmtHeader->FrameControl.FromDS = 0;
pMgmtHeader->FrameControl.MoreFrag = 0;
pMgmtHeader->FrameControl.Retry = 0;
pMgmtHeader->FrameControl.PwrMgt = 0;
pMgmtHeader->FrameControl.MoreData = 0;
pMgmtHeader->FrameControl.WEP = 0;
pMgmtHeader->FrameControl.Order = 0;
pMgmtHeader->DurationID = 314;
memcpy(pMgmtHeader->DA, Dest, MAC_ADDR_LEN);
memcpy(pMgmtHeader->SA, Source, MAC_ADDR_LEN);
memcpy(pMgmtHeader->BSSID, Bssid, MAC_ADDR_LEN);
pMgmtHeader->SequenceControl.FragmentNumber = 0;
pMgmtHeader->SequenceControl.SequenceNumber = 0;
switch (subtype)
{
case DOT11_MGMT_SUBTYPE_PROBE_REQUEST: packetsize = sizeof(DOT11_MGMT_HEADER ) +
sizeof(DOT11_MGMT_SUBTYPE_PROBE_REQUEST) + 1;
pProbeRequest = (PDOT11_PROBE_REQUEST)
((PUCHAR)pMgmtHeader + sizeof(DOT11_MGMT_HEADER ));
pProbeRequest->ssid.ElementID = 0; pProbeRequest->ssid.Length = 0;
pProbeRequest->rateframe.ieheader.ElementID = 1; pProbeRequest->rateframe.ieheader.Length = 1; pProbeRequest->rateframe.rate[0] =
(USHORT)0x82;
break;
default:
break;
}
return pMgmtHeader;
}
The probe request packet is sent with DeviceIoControl.
DeviceHandle = OpenHandle(pPacketuioDevice);
IORequest(DeviceHandle , IOCTL_PACKET11_GET_MAC, NULL, 0, Source, MAC_ADDR_LEN);
PacketLength = sizeof(DOT11_MGMT_HEADER ) + sizeof(DOT11_PROBE_REQUEST) + 1;
pMgmtFrame = CreatePacket(DOT11_MGMT_SUBTYPE_PROBE_REQUEST,Source,
BroadCast,BroadCast, PacketLength);
IORequest(DeviceHandle , IOCTL_PACKET11_INSERT_PACKET,
(PUCHAR)pMgmtFrame, PacketLength, NULL, 0);
CloseHandle(DeviceHandle);
When the driver receives the request, it checks the frame type, the source mac address, and the number of packets sent. For now, the frame type must be management. Data frames will be supported in later versions. The source address must match the adapter's mac address to prevent mac spoofing. The final control makes sure no more than two packets are sent in one second intervals. If the user packet passes these checks, the packet is created and sent to the miniport for further processing. Some adapters will send the packet without being associated as long as a channel is set. Some chipsets will only send the user packet while associated. I assume the rules set by the manufacturer while in initialization or operational mode determine if the packet will be sent.
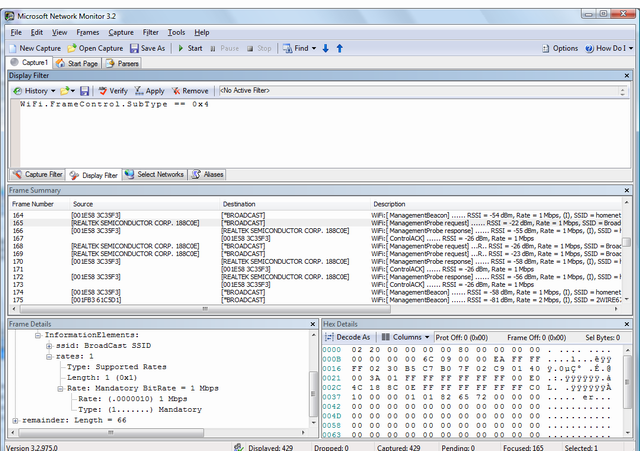
Side note: Network Monitor 3.2 is an example of the NDIS 6 technology. It can capture 802.11 packets in the air within the range of the adapter.
The highlighted packet above shows that the probe request matches the one defined with packettest.
Related Links
People
Thanks to Thomas Divine for pointing me in the right direction.
History
- Version 1.5 - Beta release - 2/12/2009
- Version 1.0 - Initial release - 8/20/2008
This is an ongoing project. More updates will come in the future.
