Introduction
In this article, I will show you how to configure the client and service to use Mutual SSL authentication in WCF. If you're not familiar with the concept of Mutual SSL Authentication, I
recommend you to read the article named An Introduction to Mutual SSL
Authentication and then continue with this article.
Background
Windows Communication Foundation (WCF) is a framework for building service-oriented applications. Address,
Binding, and Contract
(ABC) are the fundamentals building blocks of all WCF applications. Binding controls three aspects of message communication:
- The suite of WS-* protocols, including WS-Security, WS-ReliableMessaging, and so on.
- The message encoding, such as XML 1.0, Message Transmission Optimization Mechanism (MTOM), and binary.
- The transport protocol, including HTTP, TCP, Named Pipe, and Microsoft Message Queuing (MSMQ).
Thus, Binding is the place to configure Mutual SSL Authentication. However, Mutual SSL Authentication is a transport level security and it can only provide
"point-to-point" security between two endpoints (service and client). If there are intermediary systems between the client and the server, each
intermediate point must forward the message over a new secured connection.
With regard to this fact, only those bindings that support transport security can be configured to use Mutual SSL authentication. The following list shows the standard
bindings that support transport level security:
- BasicHttpBinding
- WSHttpBinding
- WS2007HttpBinding
- NetTcpBinding
- NetNamedPipeBinding
- NetMsmqBinding
- NetPeerTcpBinding
- MsmqIntegrationBinding
Configuration
Mutual SSL Authentication configuration in WCF is a two step process:
- Enable application to use transport security and use certificate as its credential in Bindings.
- Specify a valid certificate in Behaviors, which will be requested in the process of mutual authentication.
Binding configuration
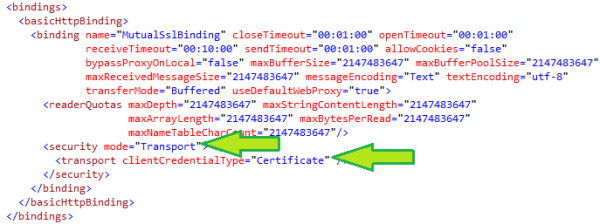
Enabling an application to use transport security and use certificate as its credential in WCF is as easy as specifying the following settings to the
<binding> section in both the client and service application configuration file:
- Specify "
Transport" as the security mode. - Specify "
Certificate" as the clientCredentialType.
And the settings are applicable for all bindings, regardless of whether it is BasicHttpBinding, NetTcpBinding, or any other qualified Binding which supports
transport level security.
The following diagram shows how to apply the settings in basicHttpBinding and netTcpBinding:
BasicHttpBinding
NetTcpBinding

Behavior configuration
To configure the client and service applications to present their certificate in the process of mutual authentication, they need an endpoint and service behavior which specify the
client certificate and service certificate, respectively.
Client configuration (EchoClient)
- Endpoint Behavior is highlighted in the green color box.
- Client Certificate is highlighted in the blue color box.

Service configuration (EchoService)
- Service Behavior is highlighted in the green color box.
- Service Certificate is highlighted in the blue color box.

Using the samples
I've created two demo projects, available from the link at the top of this article, which use the Mutual SSL Authentication in BasicHttpBinding and NetTcpBinding. In order to run the
demo projects, you need to change the following settings in both the client and service projects:
- Change the host and domain name (demopc.mydomain.com) in the client and service endpoint addresses according to your environment setup.
- Optionally change the port (56111) in the client and service endpoint addresses if it has been occupied.
- Specify a valid client and service certificate which are available from your workstation certificate store.
History
- 16th March, 2012: Initial version.
