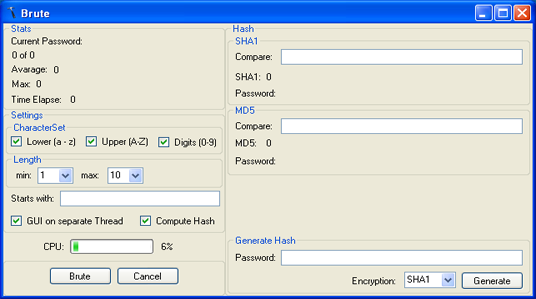
Introduction
This is my attempt to create a brute force algorithm that can use any hash or encryption standard.
Background
Bruteforcing has been around for some time now, but it is mostly found in a pre-built application that performs only one function. My attempt to bruteforcing started when I forgot a password to an archived rar file. I decided to create a bruteforce algorithm that can be used in a plug-and-play manner. At the moment, the basic hashing algorithms (MD5 & SHA) are supported but nothing stops you from using it to brute a Microsoft SQL password (* using pwdencrypt and pwdcompare).
Using the Code
Using the method is straight forward. Set up your character and password array and call the brute() or bruteUI() method.
string[] passwordArray;
string[] lower = { "a", "b", "c", "d", "e", "f", "g", "h", "i", "j", "k", "l", "m",
"n", "o", "p", "q", "r", "s", "t", "u", "v", "w", "x", "y", "z" };
string[] upper = { "A", "B", "C", "D", "E", "F", "G", "H", "I", "J", "K", "L", "M",
"N", "O", "P", "Q", "R", "S", "T", "U", "V", "W", "X", "Y", "Z" };
string[] digits = { "0", "1", "2", "3", "4", "5", "6", "7", "8", "9" };
private void setupCharArray()
{
if (ckhLower.Checked)
{
characterArray.AddRange(lower);
}
if (chkUpper.Checked)
{
characterArray.AddRange(upper);
}
if (chkDigits.Checked)
{
characterArray.AddRange(digits);
}
}
private void backgroundWorker1_DoWork(object sender, DoWorkEventArgs e)
{
brute();
}
Points of Interest
An MD5 and SHA Hash class make it easy to choose a hash type. While your PC is bruting away, a CPU monitor shows you the load on the system.
History
- 15th May, 2009: Initial post
This is my first attempt to Bruteforcing and like I said it is expandable to many other hash types and encryption standards.
