Insecure Web Servers
This article is dedicated to a very important topic: Security of webservers.
- If you are a server administrator, you can find tips on how to secure your server.
- If your website is on a public webhosting, you can make a security check.
- If you are programming web applications, you can find tips about secure programming.
This article covers 3 main topics:
- How to remove threats by malicious users on shared environments (Hostings)
- How to protect efficiently against malware
- How to learn secure web programming and defeat hackers
Security Check with Shocking Results
On the one hand, there are the hackers which try to invade into a server from outside.
But another very important topic is nearly always neglected by server admins:
What if a user on a Domain Hosting Server uploads a malicious script via FTP to manipulate the sites of other users or even the server configuration itself?
Above, you can download a PHP script and an equivalent ASP script which you can run on your web server to check the security.
Both scripts do the same: They list directories and show the contents of text files.
Additionally, you can try to execute Shell commands. Read on for more details....
The PHP script runs on PHP 4 and PHP 5 and has been tested on Windows and Linux.
The ASP script has slightly less functionality because the ASP scripting language is ultra primitive.
A server which is configured correctly should show an "Access denied" error if you try to do this outside your own home directory.
But I tried these scripts on some public webhosting servers and the results are shocking:
On a Windows server, I could read and write C:\Windows and C:\Program Files.
On a Linux server, I could execute any Shell command and read and write nearly the entire harddisk.
The script output may look like this:
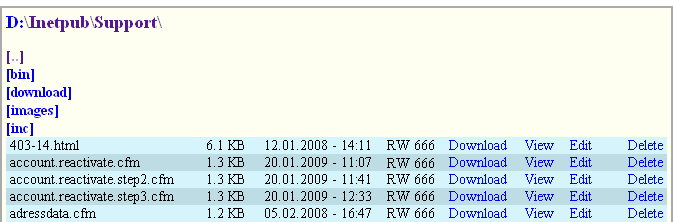
On both servers, I had read and write access to the homepages of other users and even to administrative sites as you see above.
I had full access to these folders without needing any FTP password.
If you see "RW" in a row, this means that the script has read and write permission for that file.
Do you want to host your private database on such an insecure host?
Even if a malicious person does not damage the files of other users: simply being able to READ files is a risk.
Threats by Being Able to Read Other User's Files
It is common practice to store the password for database access unencrypted in a config.php or config.asp file.
Even if a malicious user has only read access to the source files of your Joomla, Typo3, Drupal, Mambo, Wordpress or CRM installation, he will also have the passwords to access your database. This way, he can read the database and find the administrator password and take full control over your site.

Or maybe a malicious user searches in the Temp folder for session files which store all session variables unencrypted on disk.
A session file may look like this:

As you see: You should never store passwords in the session! (You should not even transmit them in plaintext to the server.)
Threats by Insecurely Configured Servers
Run this script on your server and if you find vulnerabilities, immediately write an email to the administration with a link to this article where I explain some ways to make the server more secure!
If the server is configured correctly, the script will neither be able to access other user's sites nor write into system directories.
How to check the security:
- The script first shows your home directory. Try to navigate to the parent directory with the link
[..]. This should not be possible:
opendir(nfs/c24/h15/mnt/67909/domains): failed to open dir: Permission denied - All drives that the script show are accessible:

This is OK as long as system directories don't grant write permission and as long as subdirectories with sensible content cannot be read. But you can also configure the server so that none of these will appear in the script output.
- If you can list the contents of a directory, this means that you have READ permission for that directory. Nevertheless on Linux, it may happen that you cannot access some of these files if they are links (marked with a "?") into a forbidden directory.
- If you can view the contents of a file, this means that you have READ permission for that file.
- If you can upload a file from your harddisk into the current directory, this means that you have WRITE permission. This should not be allowed for system directories:
move_uploaded_file(/usr/bin/test.gif): failed to open stream: Read-only file system
Don't forget to DELETE all test files that you have uploaded afterwards! - Finally check if you can execute Shell commands. For example
DIR C:\ or ls /home should not be allowed on a secure server.
You will be surprised by the results!
How to Secure PHP on Apache
Run phpinfo() and check the line open_basedir. With this setting, you can define the base directory for all users. After setting this value, they will no longer be able to open files outside this root folder or its subfolders (like for example C:\Windows).

If you have the above directory structure and define www_root as the base directory, then the user web_214 will also be able to read and write the files of the user web_215. But this is what we want to prevent! So what can we do? Unfortunately there exists no setting in PHP.ini to prohibit that one user can access the data of another user. It would be so nice to have a PHP.ini setting which defines a root folder for all users whose direct subfolders cannot be accessed by scripts running in one of their neighbour folders. Such a setting sadly does not exist.
But there is an awkward way if PHP runs on Apache.
In phpinfo() you find two columns: The "Master Value" is the value defined in PHP.ini. The "Local Value" is the actual one which matters at the end.
Mostly the Master Value can be overridden in a script with the function ini_set(). But this does not apply to open_basedir because it is a value critical for security which can only be set by the administrator.
In the Apache configuration file httpd.conf you can specify a per-directory Local Value for open_basedir:

You can specify multiple directories separated by colon on Linux or separated by semicolon on Windows.
In the above example, the access of the web_214 site is restricted to his home directory /web_214/ and additionally it has permission to access /usr/bin/.
For Windows, httpd.conf could look like this (note the mixed use of slashes and backslashes!):
<Directory "C:/Program Files/Xampp/htdocs/web_214">
php_admin_value open_basedir "C:\Program Files\Xampp\htdocs\web_214;D:\Temp"
</Directory>
After setting this, try the security check script again! Now you will see an error when opening a file outside the basedir:
open_basedir restriction in effect. File(C:\Program Files\Xampp\htdocs\web_218) is not within the allowed path(s)
It works, but the disadvantage is that for every new user in the future, you have to reconfigure httpd.conf and restart Apache!
If you have a script which adds new users, you can do this automatically.
It is NOT possible to define any php_ADMIN_value in a .htaccess file. This would be fatal: A user could modify his own basedir permission in a file that he uploads via FTP!
IMPORTANT
Please note that the basedir restriction does NOT apply to the shell_exec() command!
You can still execute shell_exec("DIR C:\\")
The reason is that the basedir restriction is a PHP setting which is only applied to native PHP commands like fopen() but shell commands are executed by the operating system.
Other PHP Security Settings
disable_functions
With this PHP.ini setting, you should disable functions which are potentially dangerous.
But think thoroughly about what you are doing! Disabling functions means that some scripts will stop working!
Some functions are really dangerous and normally not needed for scripting. Others might be indispensable for some purposes.
So don't simply disable all functions that !MIGHT! eventually be dangerous. You will end up with a crippled useless server!
Think about this setting:
disable_functions = exec, shell_exec, system, passthru, popen, proc_open, pcntl_exec
safe_mode
Don't believe that safe_mode = On will be helpful! It disables some useful functions and does not solve the security problem described above. So don't even waste time thinking about it! Turn it OFF! Safe Mode is deprecated in PHP 5.3.0 and is removed in PHP 6.0.0.
How to Secure IIS
IIS uses a Windows account IUSR_SERVERNAME that defines the permissions for web applications.
You can restrict the NTFS permissions for this account so it can only access the web root directory.
But the problem will be the same as described above for Apache: The site A will have full access to the files of site B - but that is what we want to prevent!
Solution 1
You can do a simple trick: Rename the directories!

Now you remove the NTFS permissions of IUSR_SERVERNAME from all folders so it doesn't have any permission at all.
Then you give it permission to all the subfolders but NOT to the domains folder.
Why that?
Now the site petshop.uk theoretically can access the files of pizzarunner.com because it has the same permissions as all the others.
But as it neither knows the other folder names nor has permission to enumerate the subfolders of domains. It has no chance to manipulate another site's files.
Solution 2
The more complex way is using application pools which isolate the sites (IIS 6.0). Each pool must run under its own Windows user account.
The advantages are:
- For each pool, individual NTFS permissions can be defined.
- The web applications are isolated, so if one website crashes, the others keep running.
- A pool can be configured to allow a maximum amount of CPU usage.
- If one pool has a memory leak, it will not affect the others because each pool has its own resources.
Setting the anonymous login account: (website settings):

Setting the application pool account: (application pool settings):

Before starting, you must assure that the HTTP service is running in worker process isolation mode (default), otherwise pools are not available.
For each website you must:
- Create a new website
- Create a new pool and assign the website to this pool!
- Create two new Windows user accounts (e.g.
POOL_PETSHOP and LOGON_PETSHOP for the site petshop.uk) - Set "Password never expires"
- Restrict both user's NTFS permissions to the www home directory
- Add the pool user account to the group
IIS_WPG (Worker Process Group) which gives it the required permissions like for example starting an application pool. But do NOT modify the permissions of the group IIS_WPG itself!! - Add the Logon user account to the Guest group.
- Configure the settings according to the above screenshots.
Drawbacks
Obviously the disadvantage of application pools is that each time you add a new website, you have to repeat all these steps which is extremely awkward.
If your server only requires PHP, the easiest solution would be to turn off IIS and install Apache.
Otherwise, you may want to write a VBS script or a C# application which automates this complex process.
Here are some tips to ease the administration via VBS script:
- Create a new website:
IIsWeb.vbs /create D:\InetPub "Petshop" /b 80
- Create a virtual directory inside a website:
IIsVdir.vbs /create "Petshop"/OnlinePay D:\InetPub\Petshop\OnlinePay
- Set permissions for a folder:
Cacls.exe D:\InetPub\Petshop\ /E /G LOGON_PETSHOP:F
- Web applications run under a MetaPath like "W3SVC/553851221/Root/AppName" The magic number is calculated from the name of the website (Microsoft likes it complicated!)
Register a web application to run under .NET Framework 2:
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\Aspnet_Regiis.exe -sn MetaPath
- Assign a web application to a pool:
Const POOLED_PROCESS = 2
Dim IIsWebVDirObj
Set IIsWebVDirObj = GetObject("IIS://localhost/" & sMetaPath)
IIsWebVDirObj.AppCreate3 POOLED_PROCESS, "PoolName", true
IIsWebVDirObj.SetInfo
If you want to write an application (EXE) which calls external scripts like IIsWeb.vbs, download my CaptureConsole.DLL which allows to call any script or console program from an application written in C++, C#, Visual Basic, Delphi, Java,... and get the outputs stdout and stderr which the console application or script has printed.
CGI, ColdFusion, Java, COM...
Obviously it is not enough to secure your server only against malicious scripts written in PHP and ASP. These are only examples.
Don't think that the work is done when the PHP and ASP scripts you have downloaded here are successfully restricted to the home directory!
Via CreateObject("RegisteredName") ASP scripts can load any kind of COM objects that are installed on the server. Some of them may be dangerous or may have security holes. The best would be to completely turn off ASP support. Who needs this ugly primitive scripting language of the stone age?
If you write a similar script like mine for example for Java or ColdFusion, send it to me in an email! If it is a cleanly written code (please don't send me spaghetti code), I will publish it here on CodeProject together with my scripts.
Threats by Naive Programmers
There are multiple errors that a web developer can make which result in an insecure website.
For example, if you program a blog and allow users to upload images, this may be a severe vulnerability if the code is written by a beginner. Also there are several errors which a programmer can make on the Login page, on the "Password Lost" page, etc.
Read more about this important topic at the end of this article!
The important point is that one insecure website on a public hosting is a threat for the entire server!
Also installing Open Source projects like e.g. PHP-Nuke may be a risk because several security vulnerabilities have been found in the past.
Threats by Trojans, Backdoors and Botnets
The internet is full of insecure servers.
Criminal gangs use these servers as Command and Control Servers (C&C Servers) to control their Botnets.
Botnets
A Botnet is a network of bots. (like P2P)
A Botnet server group may contain between 20 and 20.000 cracked machines linked together.
 The Bots (robots) of theses networks are Trojans / Backdoors which run on the PCs of ordinary people.
The Bots (robots) of theses networks are Trojans / Backdoors which run on the PCs of ordinary people.
These infected computers are called "Zombies".
A Bot may be used to send Spam, steal email addresses or bank and credit card accounts or execute Denial of Service (DOS) attacks.
A Botnet is controlled by a Botmaster, a person who sends encrypted commands to all his bots like for example: "DOS attack IP address X.Y.Z" or he sends a spam template to be mass mailed by his bots. Via a special command, the Bot Master can even instruct all the bots to update themselves to a new software version or deliver a new list of servers. Bots which run on an ordinary infected PC send stolen passwords, bank accounts, TAN numbers or email addresses to the C&C server where the Bot Master collects them.
Some Facts
Sounds like science fiction or paranoia?
To show that I'm not talking about peanuts, here are some facts:
The Dutch police found a 1.4 million node botnet.
It has been estimated that up to one quarter of all personal computers connected to the internet may be part of a botnet.
The Kraken Botnet has grown to over 400,000 bots and sends 9 billion spam messages per day.
The Kraken Botnet is apparently virtually undetectable to conventional anti-virus software.
90% of the spam comes from botnets.
Bank Fraud
Via Trojans with built in Key Loggers or directly reading browser content or via Form Injection cyber criminals spy out the passwords you use to log in into your bank account. The bot sends the spied data to his C&C Server. Cyber criminals (for example in the Ukraine) then transfer money from your bank account to the account of a so called "Dropper". This is a person who receives the money and then delivers it to his "boss" (the one who controls the botnet) and the dropper is paid with a certain percentage of the stolen money. The police may afterwards catch the "dropper" but does not know who organizes this "business". If the transfer is made into a corrupt country, the police may even be part of this "business". It's a mafia! So you will never get back your stolen money.
Read more: McColo - Who was behind it?
Koobface Attacks Facebook
The Koobface bot installs itself into Internet Explorer and parses the content of Facebook and MySpace sites and transmits the collected data to its C&C server. When the user is logged into Facebook, the worm uses the current cookie to capture the session and connects to Facebook without needing credentials. The worm reads the user's Facebook profile and the list of friends which it sends to his C&C server. The worm then receives a message from his C&C server to be send to the Facebook contacts invisibly in the background. Facebook requires a captcha image to be resolved which Koobface sends to his C&C server. The server is able to resolve these captcha images within a few seconds. (How it manages that can be read here.) Then the worm sends to the contacts something like: "Look at this video! http://geocities.com/....". When the other person goes to this URL which is a Phishing site, the page tells that a new version of Flash player must be installed to see the video. But the downloaded file "flash_update.exe" is infected and installs Koobface on the computer of the other person and converts it into a Zombie.
Kraken Registers Domains
The Kraken/Bobax Bot connects to its C&C servers via subdomains which it registers on dyndns.org, dynserv.com, yi.org and others. The dynamically constructed host name is followed by a random resource name built from English syllables and an extension like asp, php, shtm, pl, cgi. The bot sends encrypted data with a random mime type to its C&C server. Kraken constantly registers new subdomains. This randomness makes it impossible to block traffic to its servers.
Rustock Spams via Hotmail
The Rustock bot injects itself into WinLogon.exe and connects to Hotmail to send spam. It receives commands from his C&C server like: "Wait 15 minutes then download a spam template, harvest email addresses on the local computer and start 60 threads which send the spam". Rustock installs a Rootkit diver which allows it to operate invisibly on the system.
Understanding the Rustock rootkit driver is like solving a puzzle. The code is packed in many layers like an onion. The first decoder unpacks code with a myriad of fake instructions, blocks of code that do nothing, random jumps from one place to another – a huge maze to obfuscate and hide the truly malicious code. The spaghetti code has several traps to crash debuggers. Each layer allocates a buffer into which it decrypts the next layer - it's like unpacking a nested doll.
Love Bots
These operate on sites for singles where they chat with multiple persons at the same time. They intelligently analyze the answers so the chat partner will not notice that he/she is flirting with a robot. They can switch to a romantic lover or a sexually addicted conversationalist. The purpose is to invite the victim to enter another webpage where e.g. a script tries to install malware through an Active-X security hole.
Conclusion
These are only some examples. There are other bots which attack PayPal, Twitter, MySpace, or download and install Scareware.....
As you see clearly: malware today has other dimensions than in 2002 where people had temporary and slow modem connections and worms written by script kiddies spread via email attachments. Today the infrastructure allows organized criminals to earn money with their bots which are written by !very skilled! programmers. The first generation of viruses in the 90's was made to damage computers. The new generations of bots want to take control invisibly in the background!
An Insecure Server is a Threat Not Only for the Users it Hosts
You see how important it is to make your server secure.
If your server has been converted into a Command and Control Server, it is a risk for the entire internet and helps cyber criminals to do their dirty business.
Maybe your server is already a part of a botnet, who knows...?
Can you swear that it is not infected?
Do you still trust virus scanners?
Linux
And if you think that on your Linux server, this can not happen: You are wrong! Many C&C servers are written in PHP.
As Linux is used on more and more servers, the risk of infection is increasing and cannot be ignored.
For example, the Linux trojan OSX/Hovdy-A has been designed to open firewalls.
The operating system which is free of bugs and security holes simply does not exist. Also Apache has flaws.
And even without a security hole, a Linux server can be compromised if weak passwords are used.
Or if the shell_exec command is not disabled on a public hosting, any user can abuse it.
And last but not least: If a user installs buggy software like PHP Nuke, this may be an entrance for hackers.
Often the core of a botnet is a Linux IRC server. And even if a Linux server - without itself being infected - is only used by the botnet to provide malware for download to infect Windows computers, it also supports cyber criminality.
On all Linux servers which I tested with my script, I had more access to the harddisk than I should have - even on renowned big hosting companies with plenty of users.
Many Linux administrators feel unvulnerable. This attitude alone is dangerous (and arrogant)!
An administrator should always follow the principle: Trust is good, control is better.
Security Patches
It is indispensable to always have your server patched with the latest security patches.
A good example is the worm Conficker (Downadup) which between January and May 2009 infected 10 millions of computers worldwide - many of them were servers. It installed itself automatically via network making use of a security hole in the RPC service.
But the interesting point is this: Microsoft released the security patch KB958644 long before: already in October 2008.
How was it possible that this worm could infect so many computers?
Clearly because the majority of these computers was not patched!
Virus Scanner
It is important to install a Virus Scanner on your server.
But you should never rely on a Virus Scanner!
In March 2009, a friend of mine had the Conficker worm on his computer which is quite intelligent. I tried five different well known virus scanners to remove it. After hours of scanning, they all told me that the computer was !clean! A sixth one found the worm, but was unable to remove it. Finally Microsoft's Malicious Software Removal Tool removed the infected DLL.
This clearly shows that you can NOT rely on a Virus Scanner.
If you have a suspicious file, you can upload it to VirusTotal.
The advantage of this free service is that it scans your file with about 30 virus scanners at the same time:

The Autorun worm in this screenshot is quite old and so it is detected by nearly all scanners.
But if the malware is very new, you will notice that there are many scanners which do not detect it.
The reason is that the virus scanners use signatures (fingerprints) which must be generated by the employees of the Antivirus company and this may take some weeks. But new malware is produced much faster.

Another point is that bots can be remotely updated to a new version. So when the Antivirus software starts to recognize a malware, the botmaster has already released a new version and updated all his bots! The Antivirus industry is always limping after. This is the reason why botnets like Kraken are virtually undetectable to conventional anti-virus software.
Additionally some worms successfully disable antivirus software.
Lots of bots use Rootkits to hide themselves on the operating system.
Or (like Conficker) they block the infected DLL in which they are running by opening it without sharing Read permission (FILE_SHARE_READ) to other processes. So a virus scanner cannot read and analyze the file contents.
And there are cyber criminals which re-compile and re-pack their malware every few minutes with little variations and release the new mutation into the wild making it nearly impossible for Antivirus companies to generate fingerprints which are able to detect all these hundreds of versions of the malware.
The problem is very similar to the AIDS virus which permanently changes its surface structure and so plays a trick to the immune system which looks for certain surface proteins. The AIDS virus is virtually undetectable to the immune system.

A very interesting alternative to a signature based Virus scanner is ThreatExpert.
You can upload a suspicious file to the ThreatExpert Online Submission.
They will EXECUTE your file immediately and analyze all actions the malware is doing.
After running the file for some minutes they publish the results and send you an email with a link to your personal report.
You see:
- the Registry keys that the file has created,
- what system files it has manipulated,
- what system settings it has manipulated,
- to which C&C servers it has connected and
- which additional files it has downloaded and installed.
This is a snippet of a report of a file "My little baby.mp3.exe" which was received via Windows Messenger.
In a cyber cafe a trojan automatically sent a text message to all Messenger Contacts of the person who has chatted on an infected computer: "Hello, listen this song! I like it very much." together with the file with the extension *.MP3.EXE

Often a malware does not exist for very long time on your PC. It may download other executables, start them and exit as you see in the above sample.
Maybe the file you found is not active anymore. Maybe it was only a "Dropper" which has already downloaded 5 other executables like trojans, keyloggers, worms, browser plugins and spam bots.
So if you find a suspicious file, disconnect your computer from the internet while you try to clean it to prevent further infections!
ATTENTION:
Do not expect to see malware in Taskmanager!
The first worms in the year 2003 were that primitive. But today malware is more intelligent and injects a DLL into a system process or installs a rootkit driver which hides the malicious file completely.
If you don't see anything suspicious in Taskmanager this does not mean that your computer is not infected!
ATTENTION:
This sample also shows that public computers like in a cyber cafe, university or in a library are a high risk. Most of them are infected and if you enter any password it is very probable that your password will be logged and abused. NEVER do online banking on a public computer or on a friend's computer!!

If you are sick of downloading megabytes of daily updates for your virus scanner which does not even protect you well, you will ask yourself:
Isn't there anything that can prevent in real time that a malware can do a malicious action like installing a driver or hooking into another program?
The answer is: YES. There is!
Install ThreatFire which is a very intelligent addition to your Virus Scanner and free for personal use!
ThreatFire detects malicious behavior, such as capturing keystrokes or stealing data, instead of only looking for already known threats like normal antivirus software does. It protects against spyware, adware, keyloggers, viruses, worms, trojans, rootkits, buffer overflows, and other malware.

Other messages will pop up when:
- a program tries to directly access raw disk sectors.
- a program tries to inject data into another program.
- a program tries to inject a thread into another program.
- a program tries to install a network interface.
- a program tries to monitor another process.
- a program tries to modify the startpage of Internet Explorer.
- a program tries to copy itself to different places on your computer.
- a program tries to modify user permissions.
- a program tries to turn off Antivirus software.
- a program tries to remove a functionality from Control Panel.
- a program tries to hide a process from Task Manager.
- a program tries to take a snapshot from the screen or a window.
- a program tries to change the exception list of the firewall.
- a program tries to modify the hosts file.
- a program tries to create an Autorun entry.
- a program tries to install a Keylogger.
- a program tries to camouflage itself in a PIF or CMD file.
- .......and many, many more.......
Let's ask Microsoft why this kind of protection is not built in into Windows!
What we know from Microsoft since the first days is nothing than PSEUDO security like the thousand confusing "security" settings in Internet Explorer or the ridiculous User Account Control (UAC) in Vista which pops up when you want to adjust your Windows clock but stays silent if a malicious program installs a rootkit driver.
The only reason why there is so much malware "in the wild" is that Windows grants unlimited permissions to a process once an EXE has been double clicked. As you cannot know if a downloaded program is "good" or "bad" and also cannot trust antivirus software, the only chance you have is to execute it - Good Luck! It's like lottery.
An intelligent operating system should offer to execute a suspicious application in a sandbox where it can do no harm. But we will never experience that such a feature is integrated by Microsoft: not in Windows 8 and not in Windows 13.
ThreatFire even protects you if a worm like Conficker installs itself through a security hole via network automatically and invisibly in the background without the need to ever having double clicked any EXE file.

ThreatFire is a very good protection for future infections. But what to do if your computer is already infected?
If you have read the above article, you will have understood that a Virusscanner that is installed and running on the infected Windows is not very helpful, because:
- The Trojans update themselves faster through their C&C Servers than the Antivirus industry is able to detect them. The Antivirus companies need some days to add the new fingerprints of all the new malware to their databases. When your Antivirus software is downloading another update, your Trojan has already downloaded a new version which is not yet detectable. So the Tojan is always faster and stays undetected.
Today's Botnet Trojans work exactly like the AIDS virus: While the immune system needs quite a long time to produce sufficient antibodies, in the mean time the AIDS virus has already changed his surface proteins that the immune system requires to detect and eliminate it. - Some Trojans hide themselves using Rootkits and not all Antivirus Software is able to detect them.
- Some Trojans hold the infected file open without giving sharing permissions to other processes, so a Virusscanner cannot analyze the file without killing the process that holds the file opened. But the process into which the malicious DLL has been loaded may be a system process like "Services.exe" or "Smss.exe" that cannot easily be killed. So when a Trojan injects a DLL into a system process and holds his file open, the majority of Antivirus software are not able to scan this file.
- Some Trojans simply kill or disable all Antivirus software that they find running.
Due to all these problems, you will understand that a computer that is ALREADY infected cannot be cleaned by an Antivirus program running on the same computer.
So, how to disinfect a computer?
- Completely disconnect the infected computer from the internet for AT LEAST ONE WEEK. Disconnect the network cable and disable all network adaptes! (LAN + WLAN) !This is the most important part of all the procedure! You must stop the Trojan from downloading new versions from the internet.
- After at least one week has passed, you will have a Trojan on your harddisk that has probably already been added to the fingerprint databases of the antivirus software.
- Now boot the infected computer with the F-Secure Rescue CD. This gratis CD contains a Linux with Antivirus Software.
- When the Linux has bootet, the CD will tell you that it wants to connect to the F-Secure server. Now and !not before this moment! you connect the network cable.
- The F-Secure Rescue CD will now download the latest virus definition database. This takes about 10 minutes.
- Then you can scanning all your harddisks - and don't forget to also scan your USB sticks! When this CD scans your harddisk, there will be no rootkit active and no file held open by any process. This Linux can see all your files - as they really are - without any hiding techniques or access denials.
- To close security holes and avoid reinfection, install at least all Windows Updates that are marked as critical.
- As many Trojans spread themselves via USB sticks, it is VERY important to disable the Autorun Feature to avoid that just plugging in a USB stick will reinfect the computer:
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]<br />"NoDriveTypeAutoRun"=dword:000000FF

Nessus is a vulnerability scanner. It scans one or more computers remotely via network:
- It does a port scan and tries various exploits on the open ports
- It searches for misconfiguration, (e.g. open mail relay, database)
- It checks for missing security patches
- It searches for trojans and backdoors that are listening on a port
- It tries to provoke buffer overflows
- It searches default passwords and blank passwords
- It tries DOS attacks sending mangled packets
- It can remotely detect the version of installed antivirus software
- It can check for improper network segmentation
- The scanner can be scheduled to scan the company network every night
- and many many more....
Nessus uses a 250 MB database and 30.000 NASL test scripts which include individual tests for aix, apache, backdoors, centos, debian, dns, fedora, firefox, firewalls, freedb, ftp, gentoo, iis, itunes, macosx , mandriva, mandrake, mysql, netware, openssh, oracle, p2p, php, realplayer, redhat, rpc, safari, samba, services, skype, slackware, smtp, solaris, suse, trendmicro, ubuntu, vmware, webspere, windows, xerox, and many many more.....
For each security flaw that it finds, it prints very detailed information.

ATTENTION
Some Nessus's tests may cause vulnerable services or operating systems to crash!
See Demo Video | Download Nessus Installer | Request Activation key for non-professional use (free).
Are You Able to Write Secure Web Applications?
You are programming websites in PHP, ASP, ASPX, Java, Perl, CGI, CFM,...?
If you never invested time to learn how hackers attack a website, your code will be simply naive. A naive code does not assume a malicious user connecting to the site. As a naive programmer, you can not even in your dreams imagine with how much intelligence and creativity the hackers will attack you and how much time they invest and what powerful tools they use to hack your site!
IMPORTANT
Even if you are programming websites since many years but never learned how to defeat hackers, you are definitely unable to write secure code!
If you cannot answer the following questions, your code will be full of vulnerabilities:
- How should posted data be sanitized?
- What is the risk when storing cookies on the client computer?
- What attacks do hackers try on the Login page?
- What mechanisms are discouraged for the recovery of a "forgotten password"?
- What threats may arise on a badly programmed "change password" page?
- What is XSS?
- How do hackers try to bypass role based permissions?
- What do you have to be aware of when storing data in hidden input fields?
- What is "SQL injection" and how can it be defended?
- What is "second order SQL injection"?
- What is "XPath injection"?
- What is "Header injection" used for?
- What is "IFrame injection"?
- What are "Path traversal" vulnerabilities?
- How can a hacker get access by using a network sniffer?
- How can Email forms be abused to send Spam?
- Why is the lack of strong password policies a risk for the entire website?
- What is a session fixation attack?
- What is very important when using Ajax?
- What are integer vulnerabilities?
- How can buffer overflows be produced by a hacker?
- How can you avoid sending the plain text password via network?
- What considerations must be made about the web server's cache?
- What does "Replay" mean and how to defend it?
- How do you protect sensitive files not to be downloaded by a hacker?
- What risks must be defeated on pages where users can upload files?
- How should exceptions be handled and displayed to the user?
- What should be written into a Logfile and what should not?
- What tools will hackers use to attack your site?

You find the answers to these questions and more in the "Hacker's Handbook" (740 pages). This book is written by very experienced authors who analyzed many websites for security risks. They often found severe vulnerabilities even on internet banking websites.
OWASP
If you cannot buy this book for any reason, you can find very similar information for free on the OWASP website. This project is dedicated to programmers to improve security.
There you can download A Guide to Building Secure Web Applications, a PDF with 290 pages.

But that's not all: Besides a huge amount of information, you can download the OWASP Live-CD which is a CD that boots Linux with a lot of hacker tools already installed (many of them are Firefox plugins). One application on this CD is "Web Goat". This is an insecure webserver written in Java which can also be downloaded separately. It comes with a manual that teaches you how to hack Web Goat. In several lessons, you learn to use different hacker tools and compromise Web Goat.
With this knowledge, you can then start to write secure web applications.....
