Here we create servers in a non-Azure environment, create both a Linux server and a Windows server, show how to install the Connected Machine agent on both servers, show how to connect both servers to to Azure Arc one the agent is installed and configured, and explore how the servers appear in Azure Arc once they are connected.
In the previous article, we introduced Azure Arc as a way of integrating resources from other environments into Microsoft Azure. In this article, we’ll integrate two different, external servers into Microsoft Azure to illustrate Arc’s flexibility with some use cases.
The first server is a VM set up with another cloud provider. In this case, it’s an Ubuntu 20.04-based image. It has a public IP address and is accessed via the cloud provider’s integrated console. Alternatively, we can connect to it via an SSH tunnel.
The other server we’ll use is a VM hosted on-premises. This VM runs Windows Server 2012 R2, as its operating system and uses a Plesk virtualization environment. Like the Ubuntu VM, it comes with a public IP address. Unlike the Ubuntu VM, however, we’ll be connecting to it via remote desktop protocol (RDP).
Let’s first add these in Azure. Make sure you fulfill the requirements presented in the previous article. Most importantly, be sure to have the HybridCompute and GuestConfiguration providers registered to your Azure subscription.
Adding a Linux-based Server in Azure Arc
The assumption for this tutorial is that you have already created a VM somewhere. For example, you could have gone through your cloud provider of choice to run a VM image, such as Ubuntu 20.04 (LTS), which we’ve shown below:
You have some freedom in your choice of operating system. The current list of officially supported operating systems is robust, though you should confirm that none of the exceptions apply to you.
The most important information you need is the hostname and public IP. Even in cases without a public IP, we can still add the server as long as it can be reached from the outside, via some proxy or jump host, for example.
The cloud provider we selected shows the VM like this:
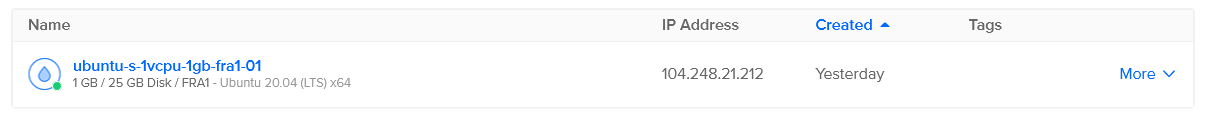
In this case, we can conveniently connect to the VM through a console integrated into the cloud provider’s portal.
Install the Azure Connected Machine Agent on a Server
At this point, we need to install the Connected Machine agent, for which Microsoft provides detailed instructions in its documentation.
Before we can install the agent on a Linux-based machine, we need to add the packages repository from Microsoft to the list of available repositories. Because we’ve selected Ubuntu as the operating system, we need to update our Advanced Package Tool (APT) to list and utilize the packages properly. For this, we launch the console Window on the other cloud provider’s portal:
First, download the package repository’s key to securely communicate with it by running the following command:
curl -sSL https://packages.microsoft.com/keys/microsoft.asc | sudo tee /etc/apt/trusted.gpg.d/microsoft.asc
Next, add the repository and update the information for local package repositories by running the following commands:
sudo apt-add-repository https://packages.microsoft.com/ubuntu/20.04/prod
sudo apt-get update
Then, install the Azure Connected Machine agent:
sudo apt-get install azcmagent
With the agent running, it’s time to go to the Azure Portal and add our server.
Add a Server to Azure Arc
Select Azure Arc in the Azure Portal. If you don’t see it in the menu yet, search for "Azure Arc" and select it from the search results. You should see an overview screen welcoming you to Azure Arc.
Select Servers to bring up the overview page, then select Add to add another server.
Azure gives us a little script snippet to add a server, which we’ll need to invoke on the server where the Connected Machine agent is running.
There are multiple options for generating the script. The most direct one gives us a script that can be invoked once. This method isn’t usually ideal because if we have a fleet of servers to onboard, we’ll need to click this option for every server. It’s certainly not the timesaver we’re looking for. In a case like this, the second option — creating a script for multiple servers — makes more sense.
But creating a script for multiple servers is a more involved process, and has a couple more prerequisites. Most importantly, a service principal must be available. The service principal is required to control your Azure subscription. It’s mostly to negotiate the integration of the new server, but it’s necessary to make the whole process automatic.
Finally, there are two more specialized options that make it quite convenient under certain edge case scenarios: when a server is already running the Update Management service, and
when servers have been running in the VMWare sphere environment. In the first case, Azure already knows about the servers, which makes integration rather easy. In the second case, the server can be integrated directly via a tool called Azure Migrate.
Generate a Script
Let’s generate a script to add a single server:
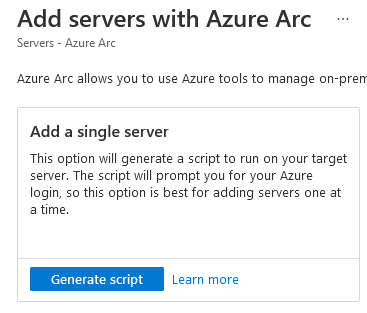
In the dialog, we’re first informed of the prerequisites for adding the server. In our case, we’ve already met them.
Now it’s time to get some details about the server, which we’ll use to generate the right script.
First, make sure to select the right operating system:
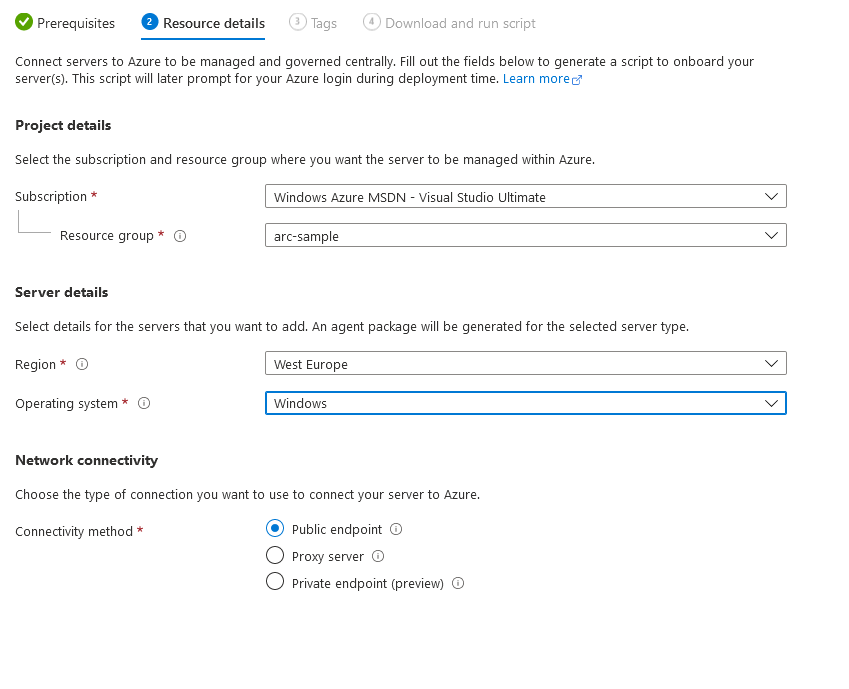
You also need to make sure that the connectivity method is correctly selected. In our case, we have a public IP address on the server. This means that a public endpoint exposed by the agent can be used.
The next section allows us to select some tags for the server. This is very handy if there are multiple servers to be added. It lets us filter them by data center, location, and many other details that we might find useful. In this series, we’ll only add two servers, so we might as well skip these tags for now.
Finally, we get a script that we can run. The script can either be downloaded or copied. We recommend copying it line by line, to understand what each line is doing before actually invoking it.
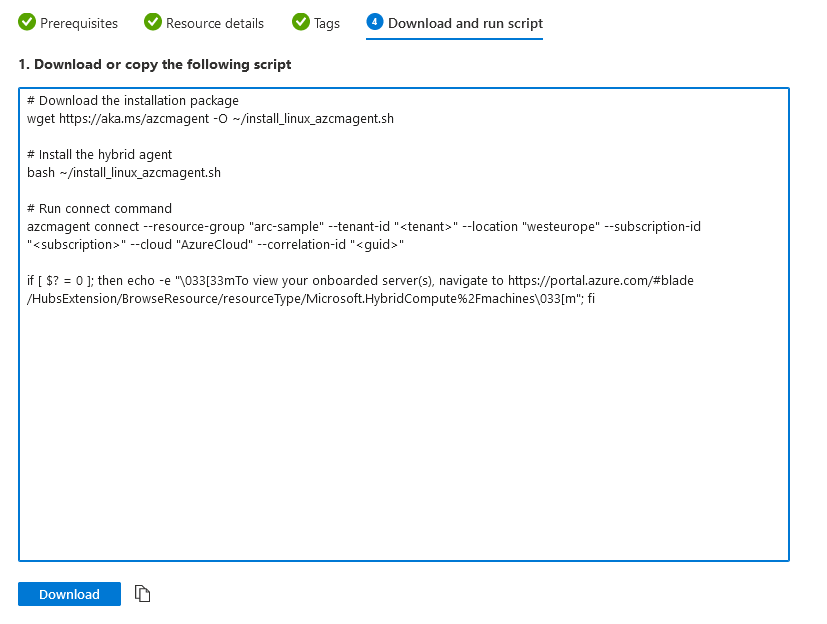
Examine the Script
Here’s the short script Azure Arc generates for us to add the server:
# Download the installation package
wget https:
# Install the hybrid agent
bash ~/install_linux_azcmagent.sh
# Run connect command
azcmagent connect --resource-group "arc-sample" --tenant-id "<tenant>" --location "westeurope" --subscription-id "<subscription>" --cloud "AzureCloud" --correlation-id "<guid>"
if [ $? = 0 ]; then echo "\033[33mTo view your onboarded server(s), navigate to https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.HybridCompute%2Fmachines\033[m"; fi
Now, let’s examine it piece by piece.
The first command downloads the script and saves it in the home directory of the current user:
wget https:
Then, the script is invoked to install the hybrid agent:
bash ~/install_linux_azcmagent.sh
Finally, the azcmagent tool is invoked to connect to the selected resource group (for example, "arc-sample" in the previous screenshot) using our subscription ID. It's important to note the correlation ID, which only works once.
# Run connect command
azcmagent connect --resource-group "arc-sample" --tenant-id "<tenant>" --location "westeurope" --subscription-id "<subscription>" --cloud "AzureCloud" --correlation-id "<guid>"
if [ $? = 0 ]; then echo "\033[33mTo view your onboarded server(s), navigate to https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.HybridCompute%2Fmachines\033[m"; fi
Run the Script
The script is run by copy and pasting it to a terminal of your server. While running the azcmagent connect command, you need to log in to the Azure Portal to confirm the connection. This is done through a URL — usually, something like Microsoft’s device login page, using a code shown in the command line.
If you logged in successfully, you’ll see a message pointing you to the Azure Portal, where the server already appears on the list:
Examine the Ubuntu VM in the Azure Portal
The overview page for our Ubuntu VM in the Azure Portal looks like this:
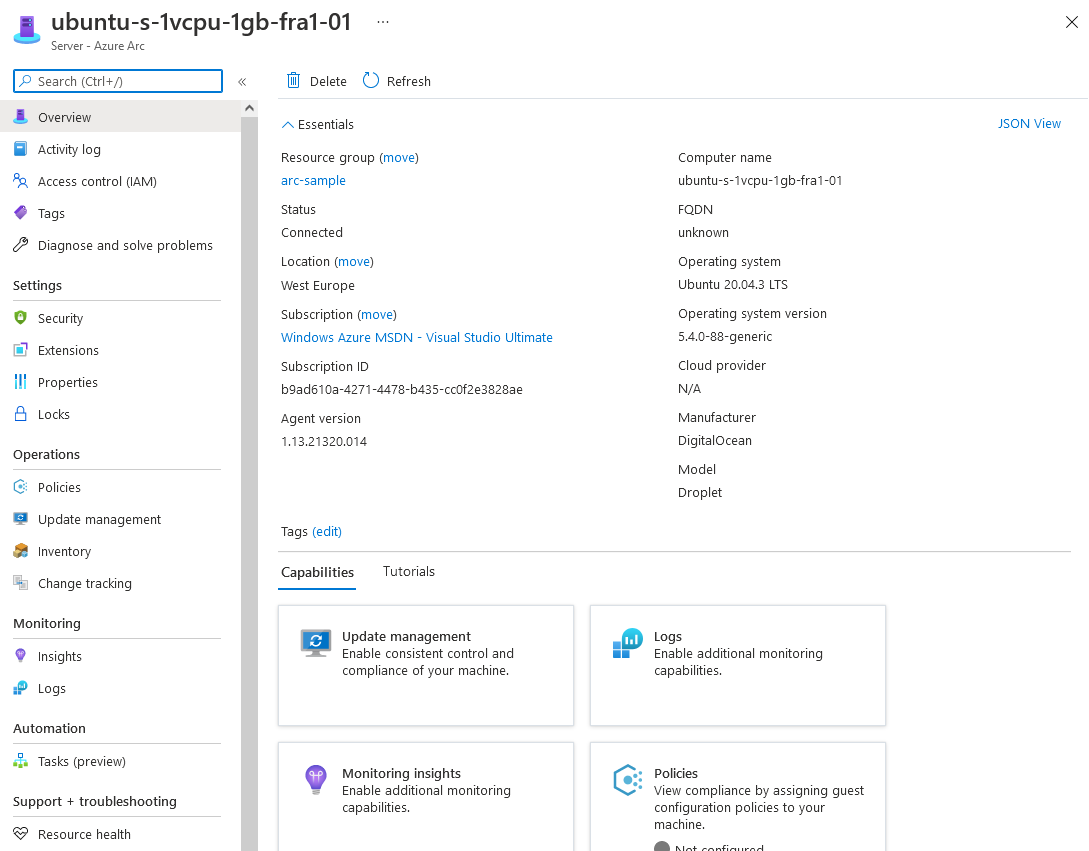
We see a couple of pieces of information already populating the Essentials section.
The information listed includes these details:
- Operating system name, type, and version
- Computer name, fully qualified domain name (FQDN), manufacturer, and model
- Domain name (if joined to an Active Directory domain)
- Connected Machine agent version
- Active Directory and DNS fully qualified domain name (FQDN)
- UUID (BIOS ID)
- Connected Machine agent heartbeat
- Connected Machine agent version
- Public key for managed identity
- Policy compliance status and details (if using guest configuration policies)
- SQL Server installed (Boolean value)
- Cluster resource ID (for Azure Stack HCI nodes)
- Hardware manufacturer
- Hardware model
- Cloud provider
- Amazon Web Services (AWS) account ID, instance ID, and region (if running in AWS)
Now, let’s accomplish the same result with a Windows machine.
Adding a Windows-based Server in Azure Arc
The process of adding a Windows-based server in Azure Arc is almost the same as adding a Linux-based server. However, it differs in a few key details — most notably that we’ll be connecting via RDP.
Install the Azure Connected Machine Agent
As in the case of the Linux VM we set up, start this process by installing the Connected Machine agent.
Connect to the Windows VM via RDP and open a web browser. In the browser, navigate to "https://aka.ms/AzureConnectedMachineAgent" to begin downloading the MSI file.
Install the agent like you would any standard Windows software. Open the downloaded MSI file and follow the instructions.
The following screenshot shows how the script looks if you select Windows as your operating system:
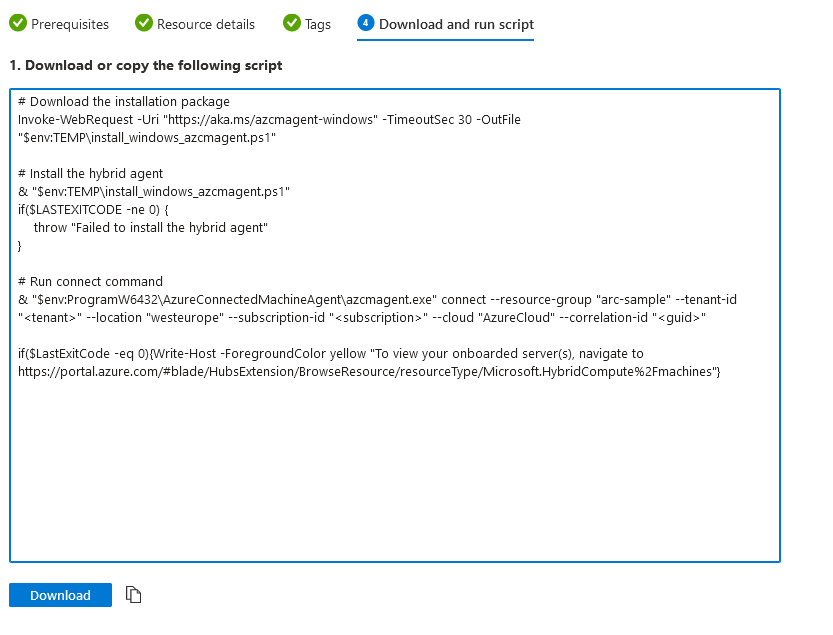
Here, we see the script is now using PowerShell to run its commands.
Inspect the Script
The script generated for our Windows machine looks a little different, but the structure is similar.
# Download the installation package
Invoke-WebRequest -Uri "https://aka.ms/azcmagent-windows" -TimeoutSec 30 -OutFile "$env:TEMP\install_windows_azcmagent.ps1"
& "$env:TEMP\install_windows_azcmagent.ps1"
if($LASTEXITCODE -ne 0) {
throw "Failed to install the hybrid agent"
}
#Install the hybrid agent
& "$env:ProgramW6432\AzureConnectedMachineAgent\azcmagent.exe" connect --resource-group "arc-sample" --tenant-id "<tenant>" --location "westeurope" --subscription-id "<subscription>" --cloud "AzureCloud" --correlation-id "<guid>"
#Run connect command
if($LastExitCode -eq 0){Write-Host -ForegroundColor yellow "To view your onboarded server(s), navigate to https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.HybridCompute%2Fmachines"}
As we did with the Linux VM, let’s inspect the script line by line.
We start by downloading the installation package and moving it to the temporary folder:
Invoke-WebRequest -Uri "https://aka.ms/azcmagent-windows" -TimeoutSec 30 -OutFile "$env:TEMP\install_windows_azcmagent.ps1"
Then, the installation script is run from the temporary folder:
& "$env:TEMP\install_windows_azcmagent.ps1"
if($LASTEXITCODE -ne 0) {
throw "Failed to install the hybrid agent"
}
Finally, the connect subcommand from the azcmagent.exe tool is invoked to establish the connection.
At this point, we need to open the device login page again to confirm the connection to our Azure account and subscription.
& "$env:ProgramW6432\AzureConnectedMachineAgent\azcmagent.exe" connect --resource-group "arc-sample" --tenant-id "<tenant>" --location "westeurope" --subscription-id "<subscription>" --cloud "AzureCloud" --correlation-id "<guid>"
if($LastExitCode -eq 0){Write-Host -ForegroundColor yellow "To view your onboarded server(s), navigate to https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.HybridCompute%2Fmachines"}
Depending on the age of your VM, you may need to actually allow TLS 1.2 before running the generated script. In our case, this is necessary because it’s a Windows Server 2012 R2 instance. In PowerShell, we need to run the following:
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
Now, we can run the commands. As before, you should watch for the devicelogin message. Here’s how that might look like:
To sign in, use a web browser to open the page https://microsoft.com/devicelogin and enter the code CFVTXMCHY to authenticate.
Once authenticated, you’ll see a message that looks similar to the following:
time="2021-12-02T14:46:22+01:00" level=info msg="The resource was successfully onboarded in Azure" VM Id=37eb5b6d-3720-408f-89c0-afabcab94cf3
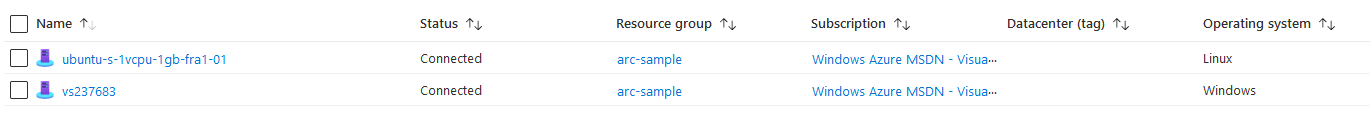
We now have two servers onboard. The list of servers grows more populated.
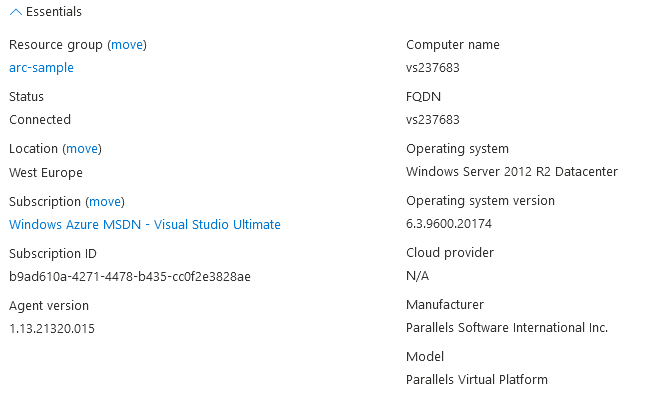
Here, Azure Arc displays the same information fields as it did for our Ubuntu VM — just with different values, of course.
Conclusion
Adding new servers in Azure Arc is straightforward when we use the script generated for us. The most important things to keep in mind are your VM’s operating systems and connection method prerequisites. Having fulfilled these, it should be a simple matter of running the script Azure Arc generates for us to onboard servers from varied cloud providers, running Linux or Windows. Continue to the third and final article of this series to see how to set up security, Sentinel, and runbooks.
To learn more about Azure Arc enabled servers, check out Azure Arc-enabled servers Overview.
