Here we introduce Azure Security Center and demonstrate how to add it to the cluster, show how to enable Azure Defender via security center, introduce Azure Sentinel and demonstrate how to add it to our cluster, and show examples of the kinds of security events Azure Sentinel can record for an Arc-Enabled Kubernetes cluster.
In the first article of this three-part series, we explored how to connect Azure Arc to a Kubernetes cluster hosted in the cloud and apply a policy. We can now manage our Kubernetes cluster (and any other clusters and servers we add later) from one handy location.
We’ll build on the previous article by adding security and monitoring to the external cluster that we’re now managing with Azure Arc.
Setting up Microsoft Defender for Cloud
Microsoft Defender for Cloud (formerly Azure Security Center and Azure Defender) is Azure’s dashboard for everything related to security. It works in tandem with Azure Monitor and its Log Analytics tool. Security Center uses Azure Policy to create a default security policy for its enrolled subscriptions.
Using Security Center, we can apply policies and turn on advanced security features to protect our resources. We can also act against any security threats we might encounter. There are two pricing tiers: the free tier with basic features, and Azure Defender (part of Microsoft Defender) with enhanced security.
The free security tier is enabled by default, providing access to security policies, assessments, and recommendations. However, it doesn’t apply any of the advice or protects our resources from threats. We need Microsoft Defender’s advanced features.
Microsoft Defender for Cloud offers features such as regulatory compliance, just-in-time (JIT) virtual machine (VM) access, adaptive application controls, and threat protection for infrastructure as a service (IaaS) and platform as a service (PaaS), helping us react to any threats.
Enabling Microsoft Defender
To enable Microsoft Defender for Cloud, we first login to the Azure portal and go to the Security Center.
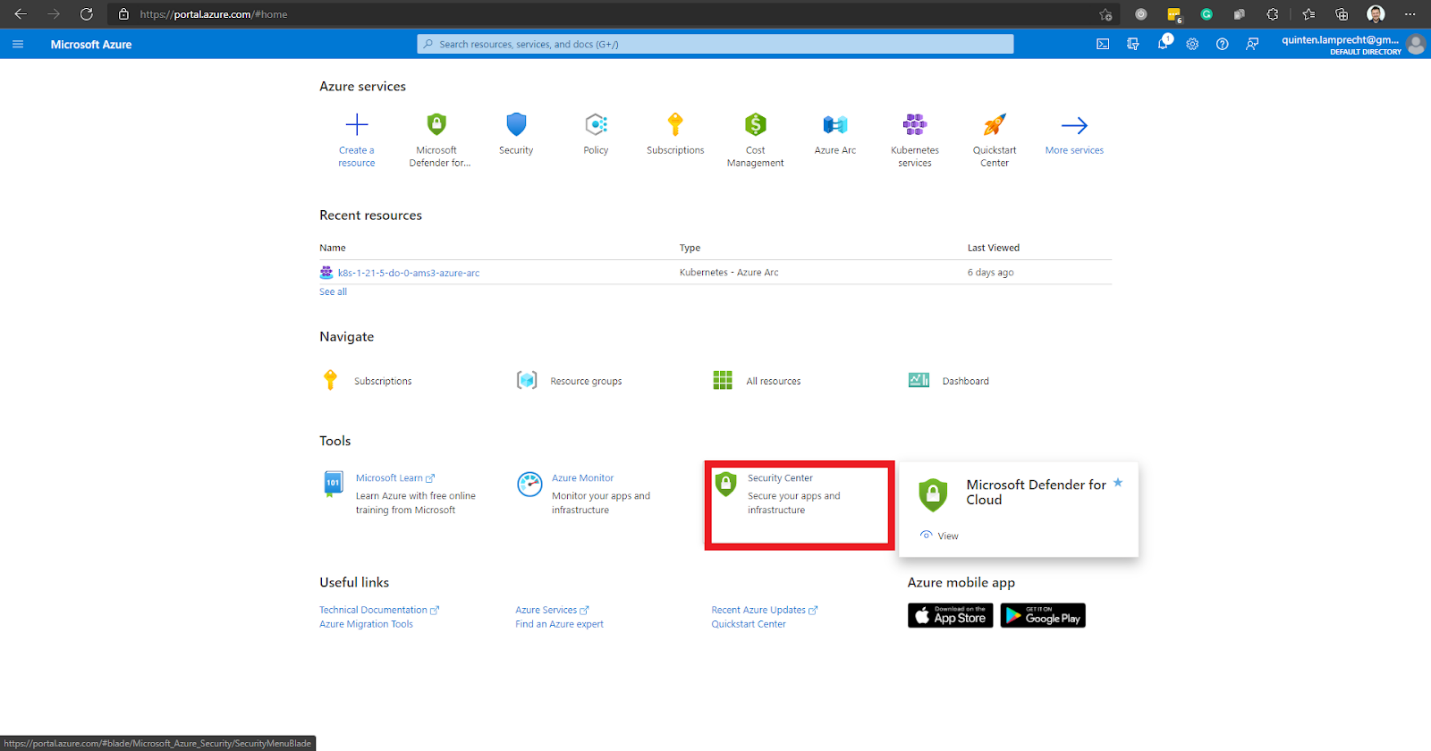
This option takes us to the Microsoft Defender for Cloud Overview page to select the desired Azure subscriptions.
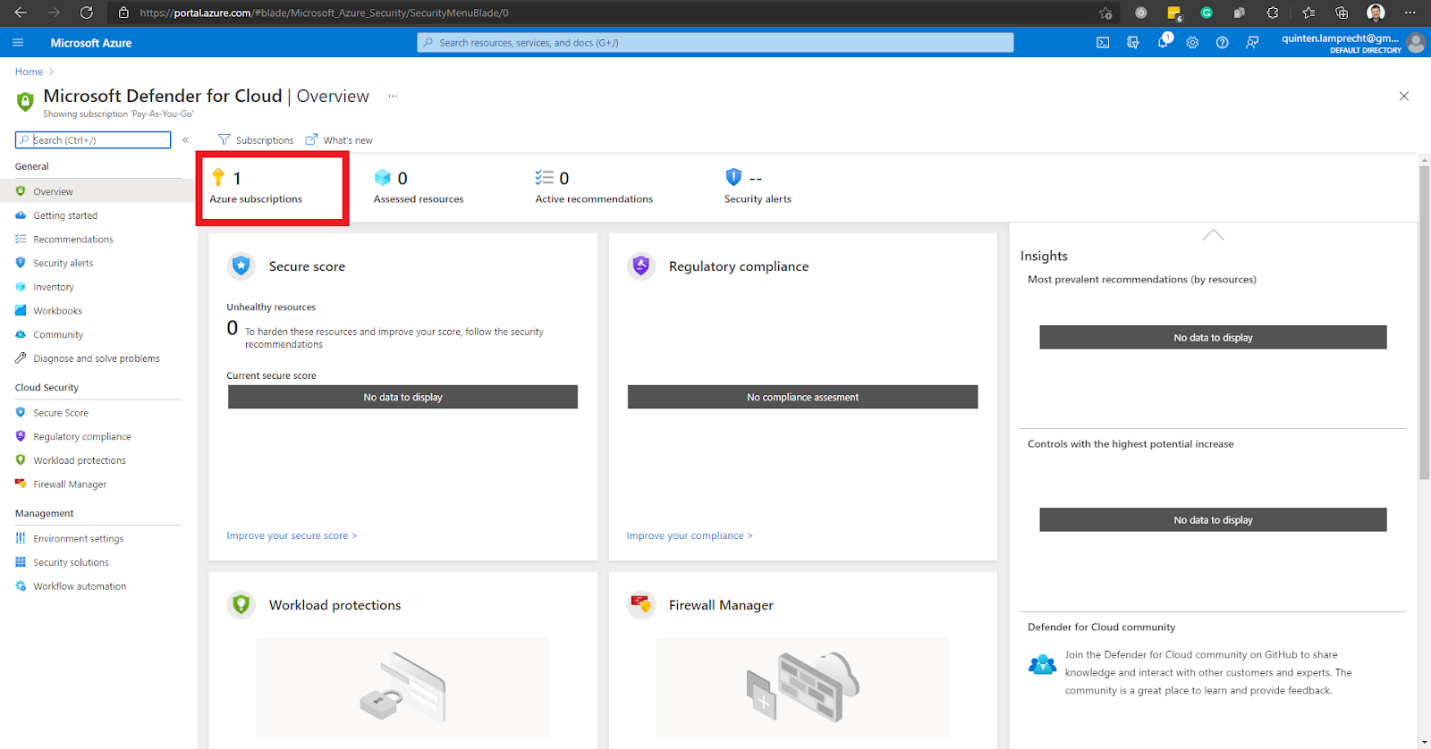
This action directs us to the Environment settings page. We expand our Tenant Root Group.
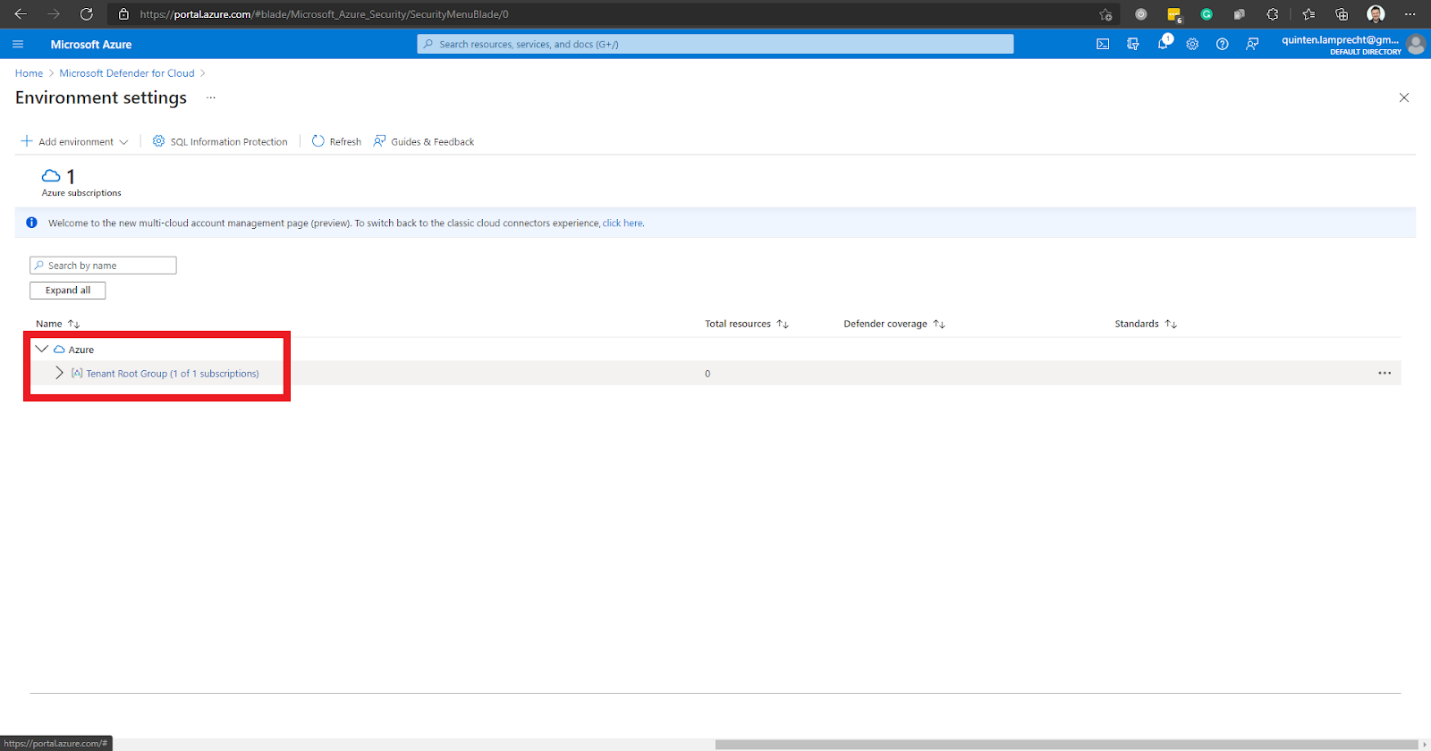
Azure then lists the subscriptions assigned to our account. We select the subscription where we wish to enable Microsoft Defender. In this case, it’s the Pay-As-You-Go subscription.
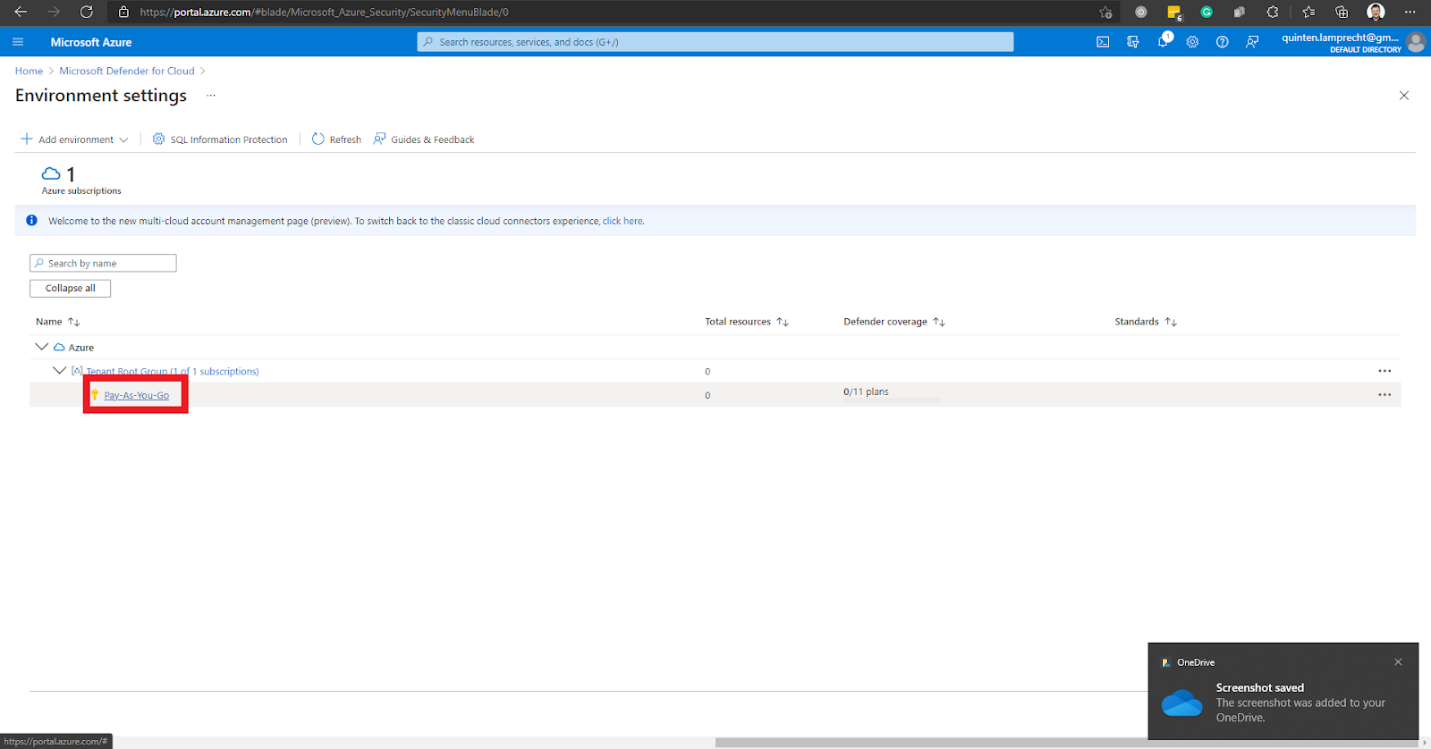
The first option, Enhanced security off, is the default. We select the option Enable all Microsoft Defender for Cloud plans.
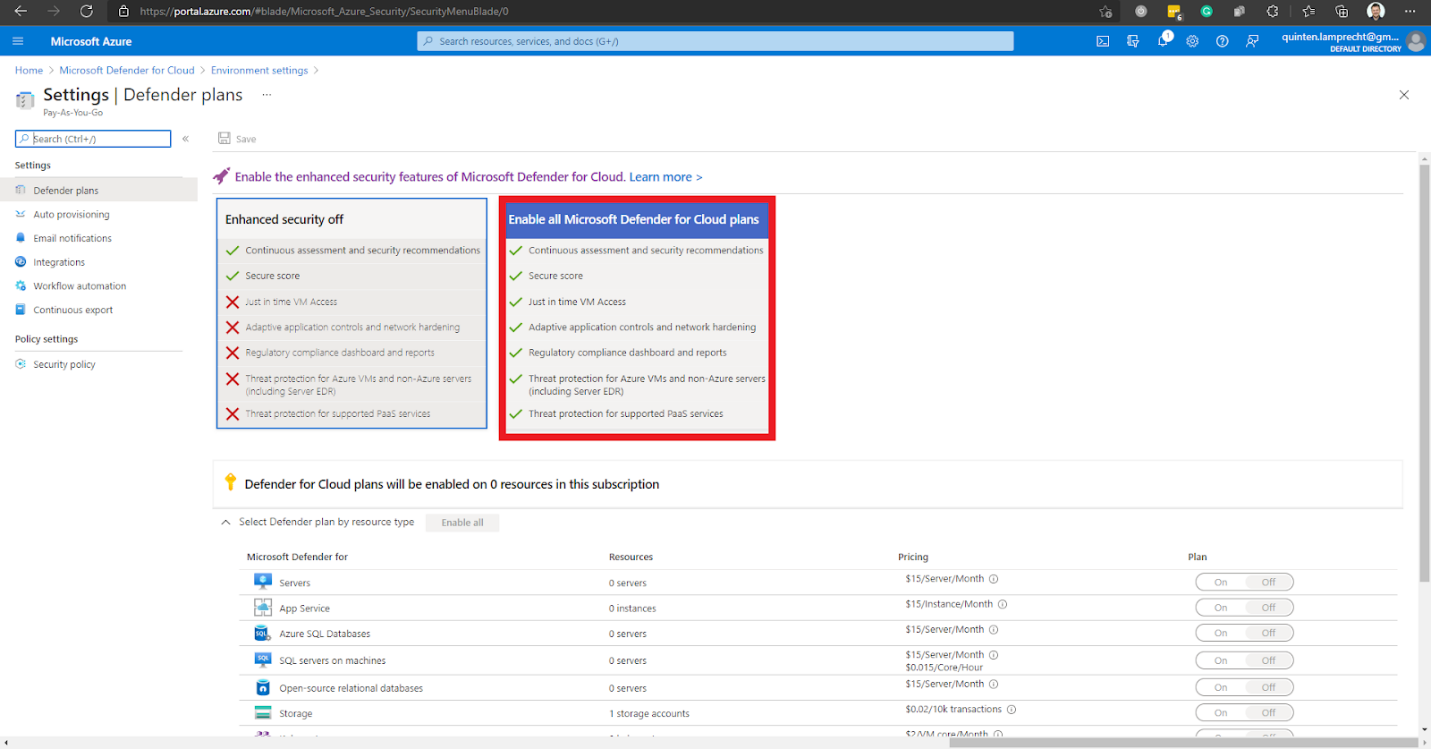
This action enables the toggle list where we can specify which resource types the Microsoft Defender plan needs to protect. By default, all resource types are On.
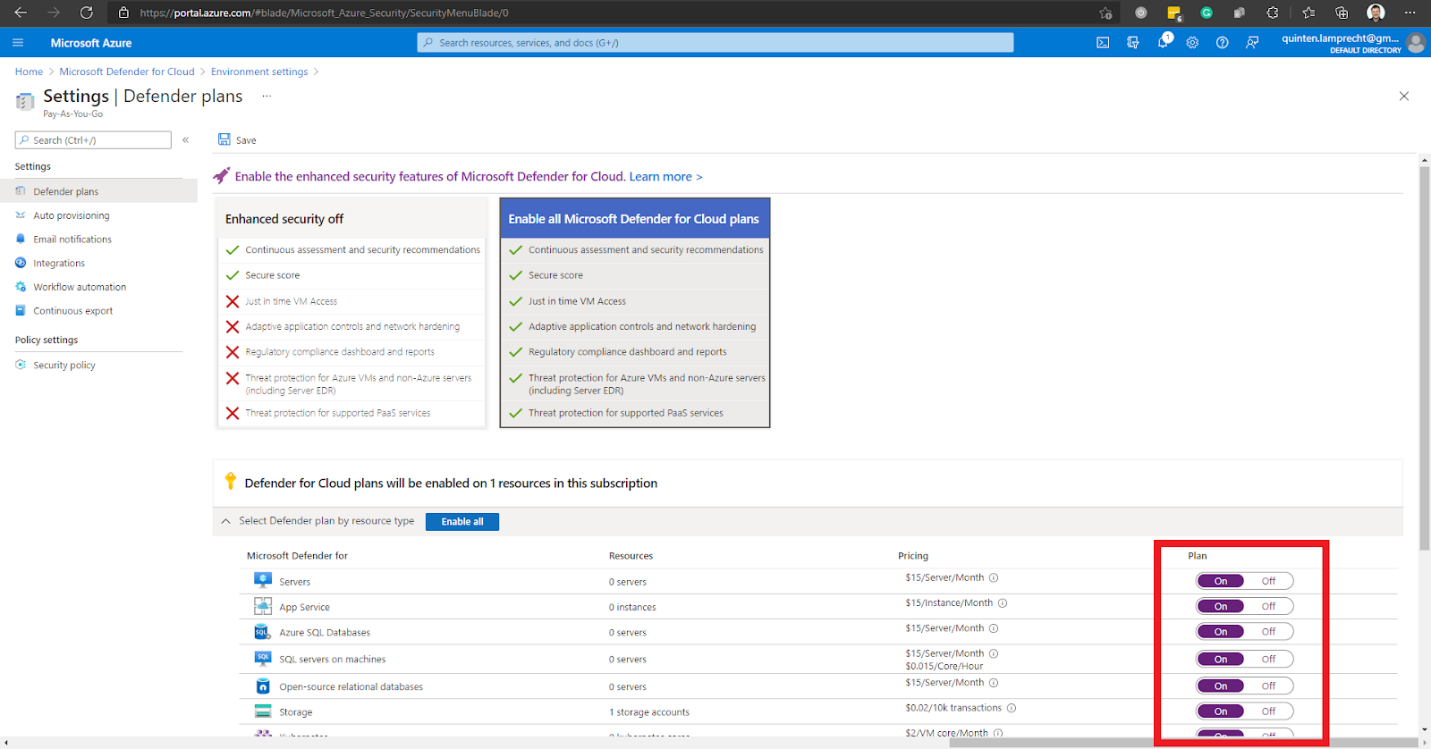
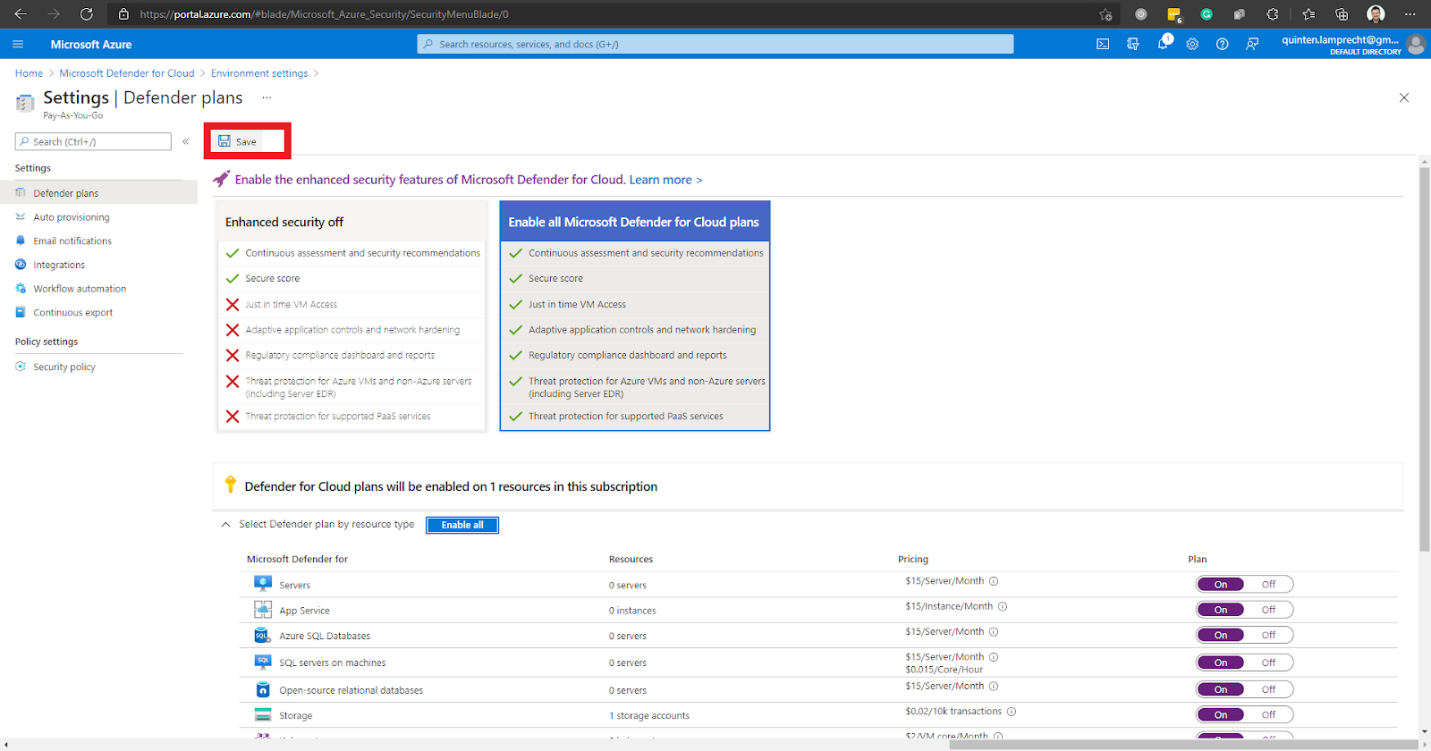
After selecting the resource types to enable, we click Save in the top left section of the current page to save our settings.
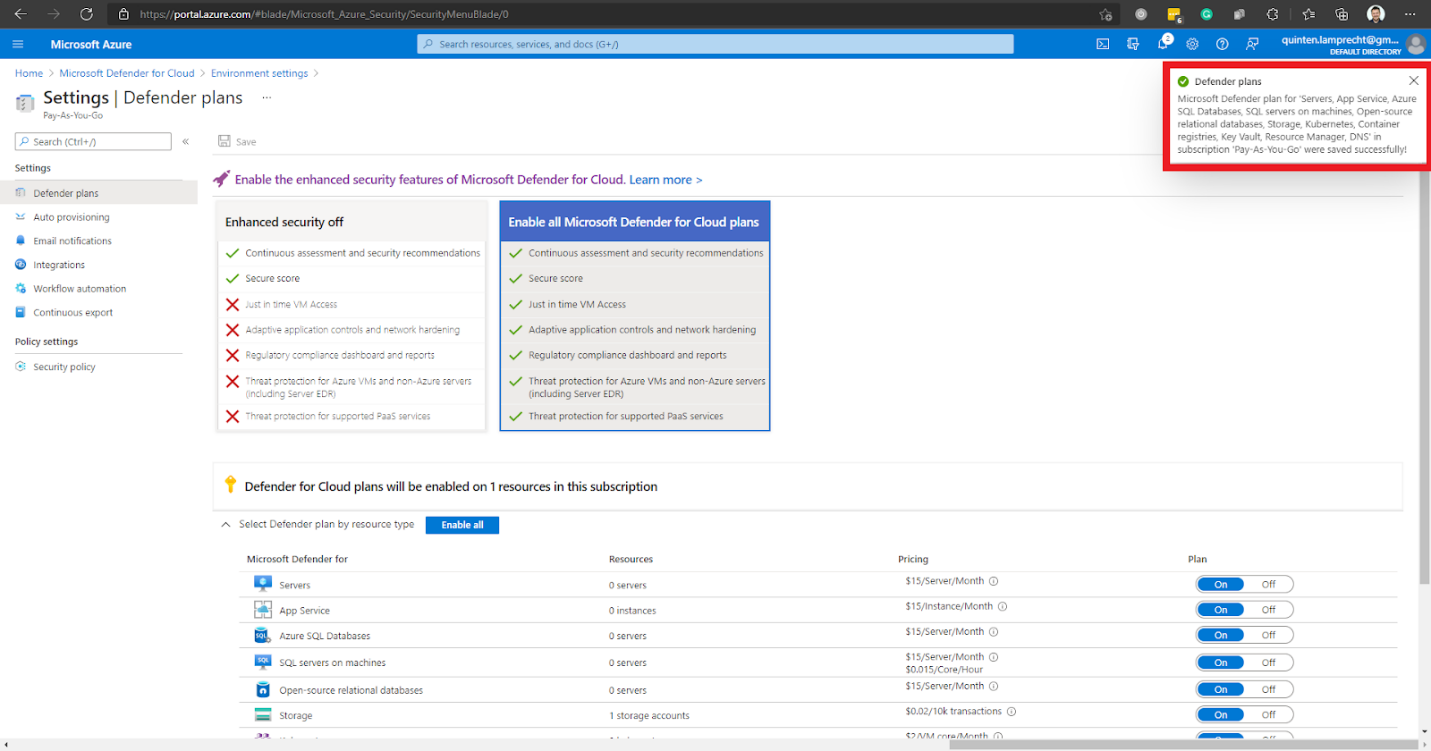
We then receive a notification stating that we have saved Microsoft Defender plans successfully.
Now that we have enabled Microsoft Defender, we can extend these security features to our Azure Arc-enabled Kubernetes cluster.
Installing the Microsoft Defender for Kubernetes Cluster Extension
We must have a few prerequisites in place before installing Microsoft Defender.
We need to ensure a connection between the Kubernetes cluster and Azure Arc. We must also have installed the connectedk8s and k8s-extension. Read the previous article in this series for how to achieve this.
az extension add --name connectedk8s
az extension add --name k8s-extension
We must also configure port 443 on the following endpoints for outbound access.
For clusters on Azure Government cloud:
- *.ods.opinsights.azure.us
- *.oms.opinsights.azure.us
- Login.microsoftonline.us
For clusters on other Azure cloud deployments:
- *.ods.opinsights.azure.com
- *.oms.opinsights.azure.com
- Login.microsoftonline.com
We’ll be deploying the Microsoft Defender extension to our Azure Arc-enabled cluster using Azure CLI. We must be logged in to Azure and set the account to our subscription where we want to deploy the Microsoft Defender extension. That is the subscription linked to the Kubernetes cluster.
az login
az account set --subscription <your-subscription-id>
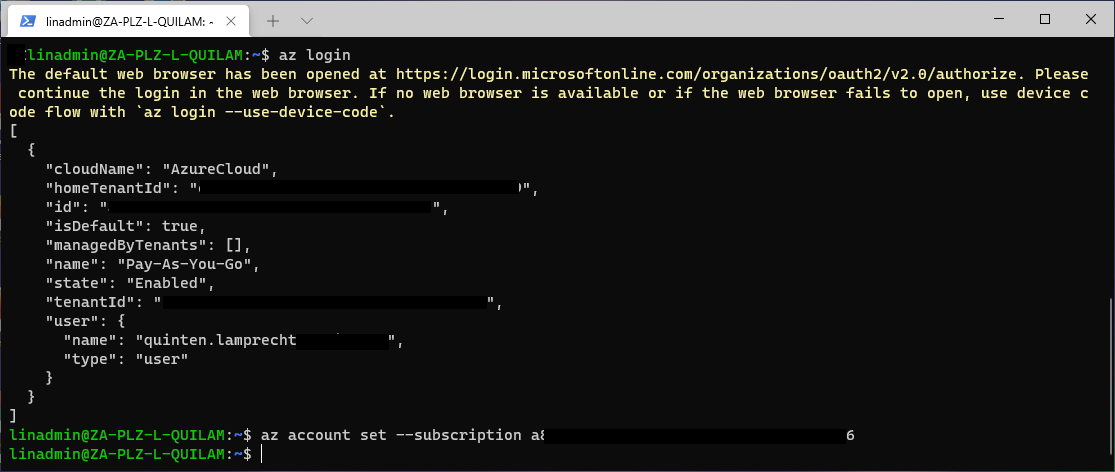
We then run the following command to deploy the extension on top of our Azure Arc-enabled Kubernetes cluster:
az k8s-extension create --name microsoft.azuredefender.kubernetes --cluster-type connectedClusters --cluster-name k8s-1-21-5-do-0-ams3-azure-arc --resource-group AzureArc --extension-type microsoft.azuredefender.kubernetes
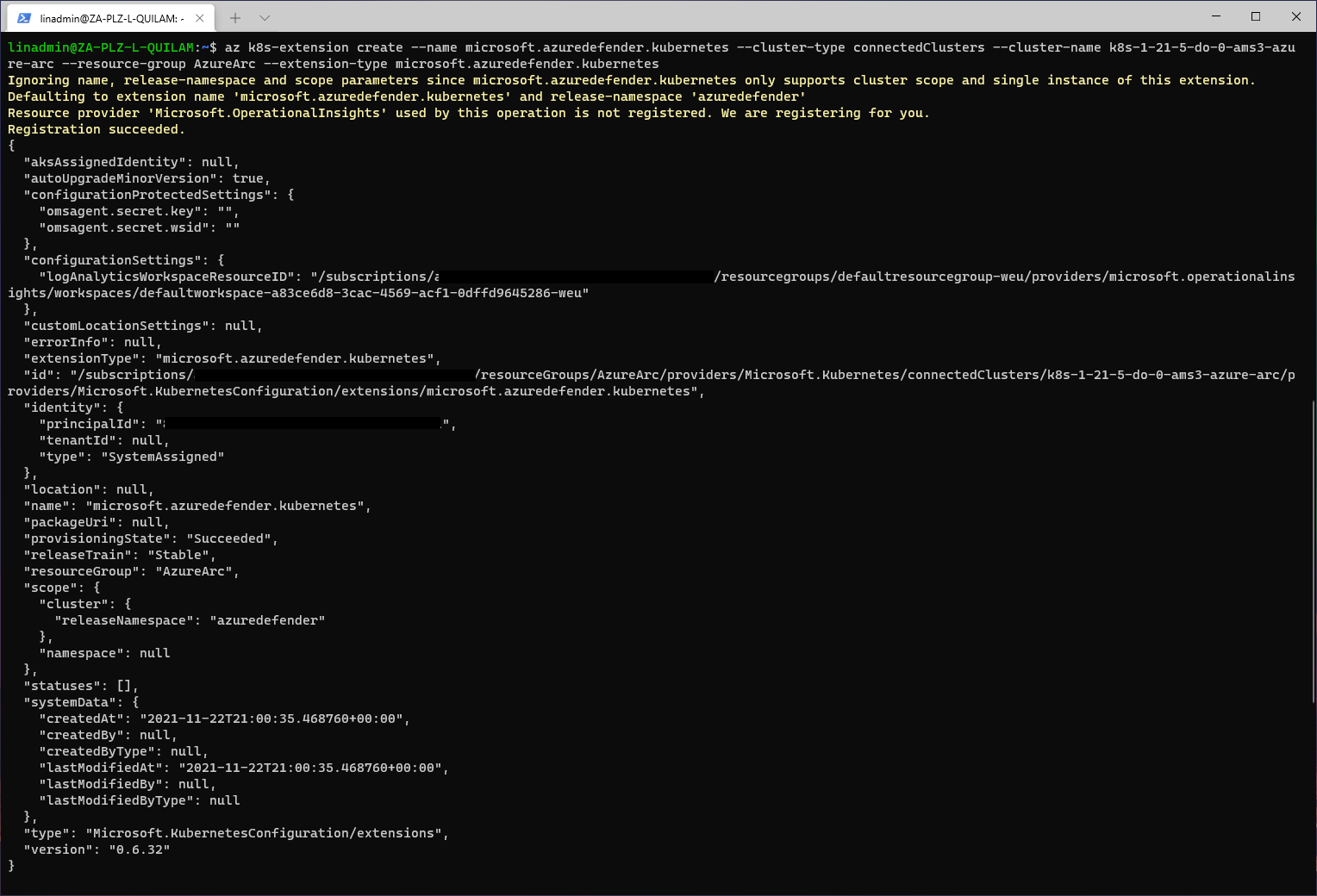
Our deployment was successful, but we can validate it to make sure by running this command:
kubectl get pods -n azuredefender
We can confirm that our azuredefender pods are running using this command:
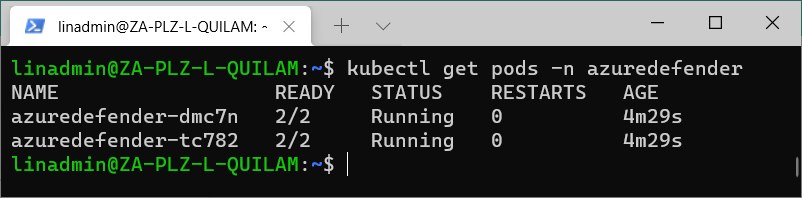
Alternatively, we can confirm the deployment on the Azure portal. We go to Microsoft Defender for Cloud’s Recommendations page and open the Enable Microsoft Defender for Cloud security control. We select the recommendation named Azure Arc-enabled Kubernetes clusters should have Microsoft Defender for Cloud's extension installed.
We ensure our Arc-enabled Kubernetes cluster appears under Healthy resources.
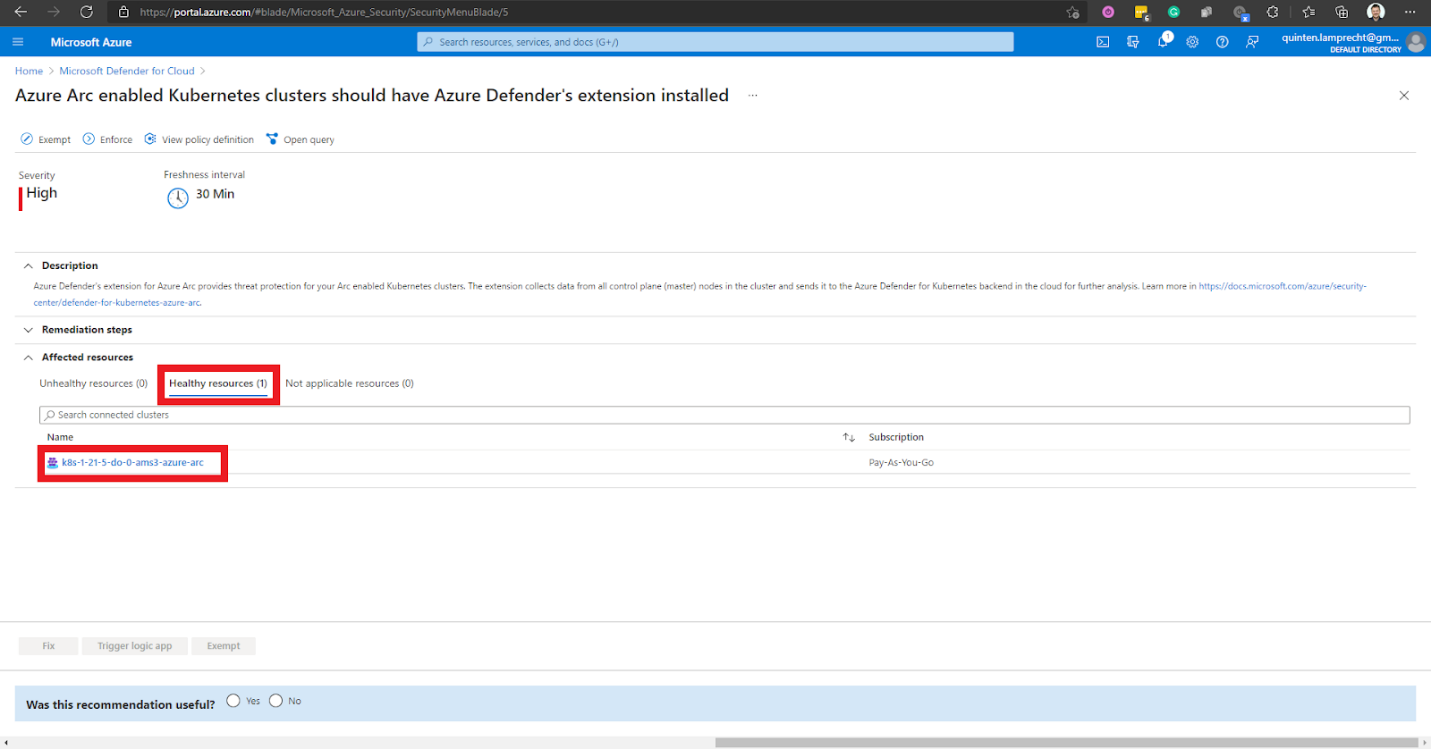
We can now access security features for our Kubernetes cluster.
Setting up Azure Monitor
In this section, we'll enable monitoring of our Azure Arc-enabled Kubernetes cluster using Azure Monitor (also called Microsoft Monitor). After we have set up Azure Monitor, we’ll be able to view the memory and CPU use metrics from controllers, nodes, and containers. We can also retrieve logs directly from our Azure Arc-enabled cluster using Container Insights.
Prerequisites for Enabling Azure Monitor
- Connectedk8s and k8s-extension extensions installed
- A Log Analytics workspace.
- Contributor role assignment on the Azure subscription
- Contributor and Reader role assignments on the Log Analytics workspace
- Outbound access from the projected cluster to Microsoft monitoring endpoints
Enabling Azure Monitor
To onboard our Azure Arc-enabled Kubernetes cluster, we log into our Azure portal and go directly to our cluster. From within our cluster, we can select an option in the Monitoring section.
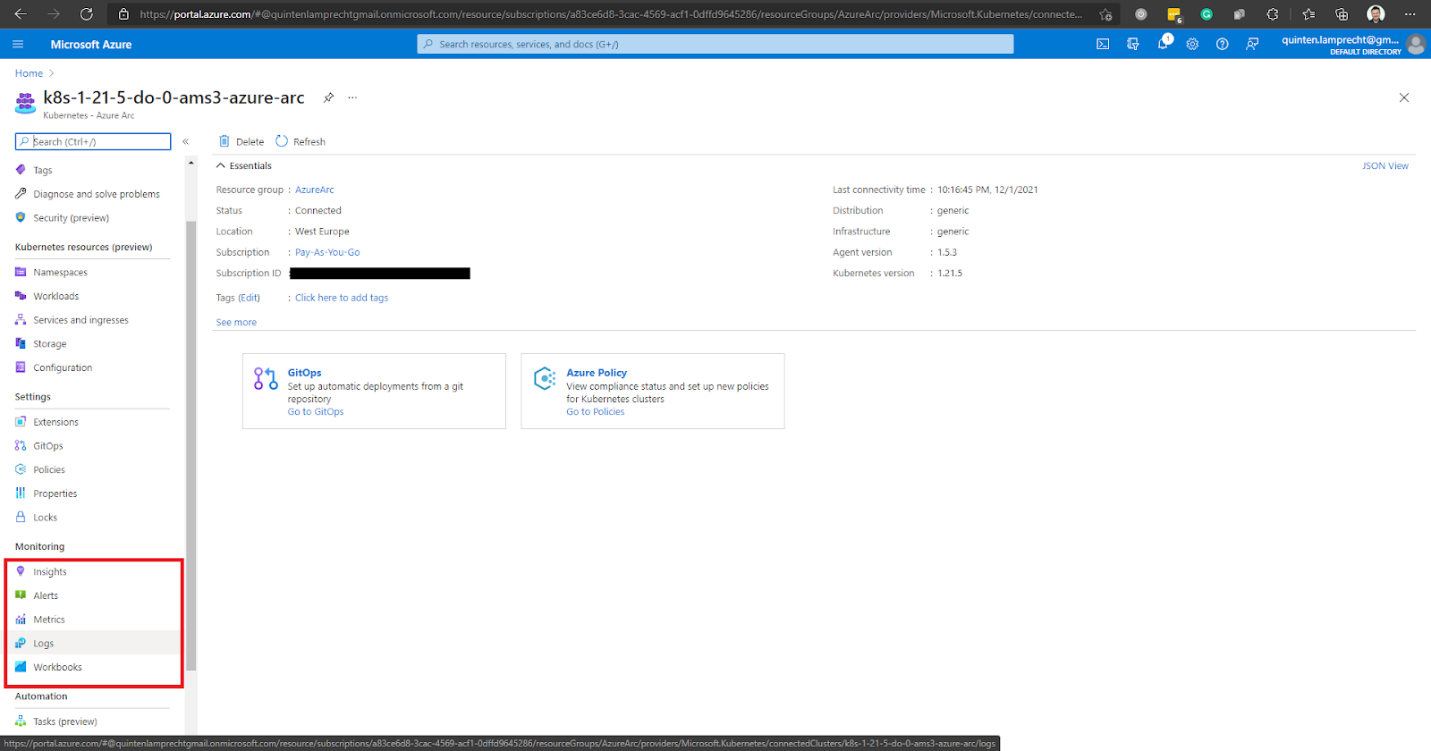
Since we have not yet onboarded our cluster to Azure Monitor, Azure redirects us to the Onboarding page. From there, we select Configure azure monitor.
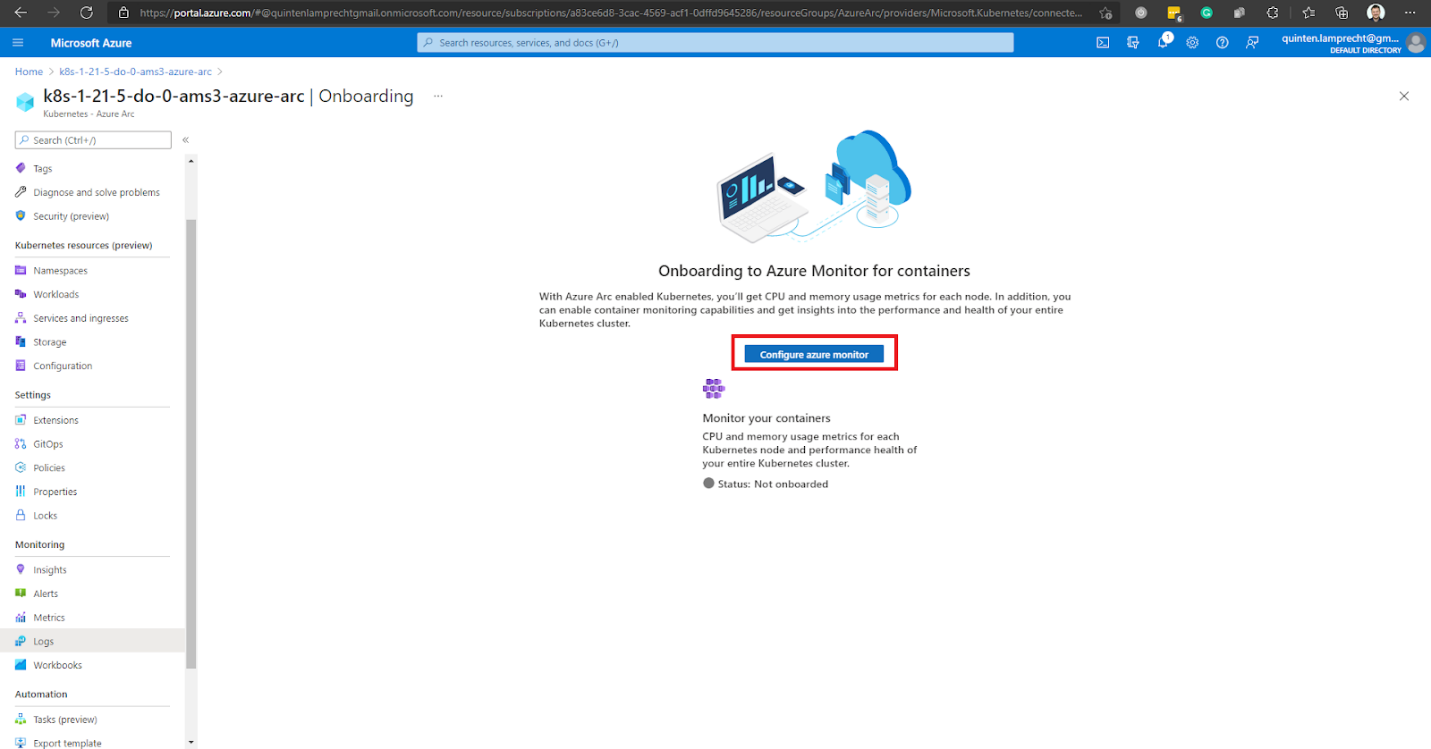
The Configure Azure Monitor for Kubernetes window prompts us to select a Log analytics workspace to use. We choose it from all the available workspaces listed, then click Configure. If you do not have a Log Analytics workspace, create one.
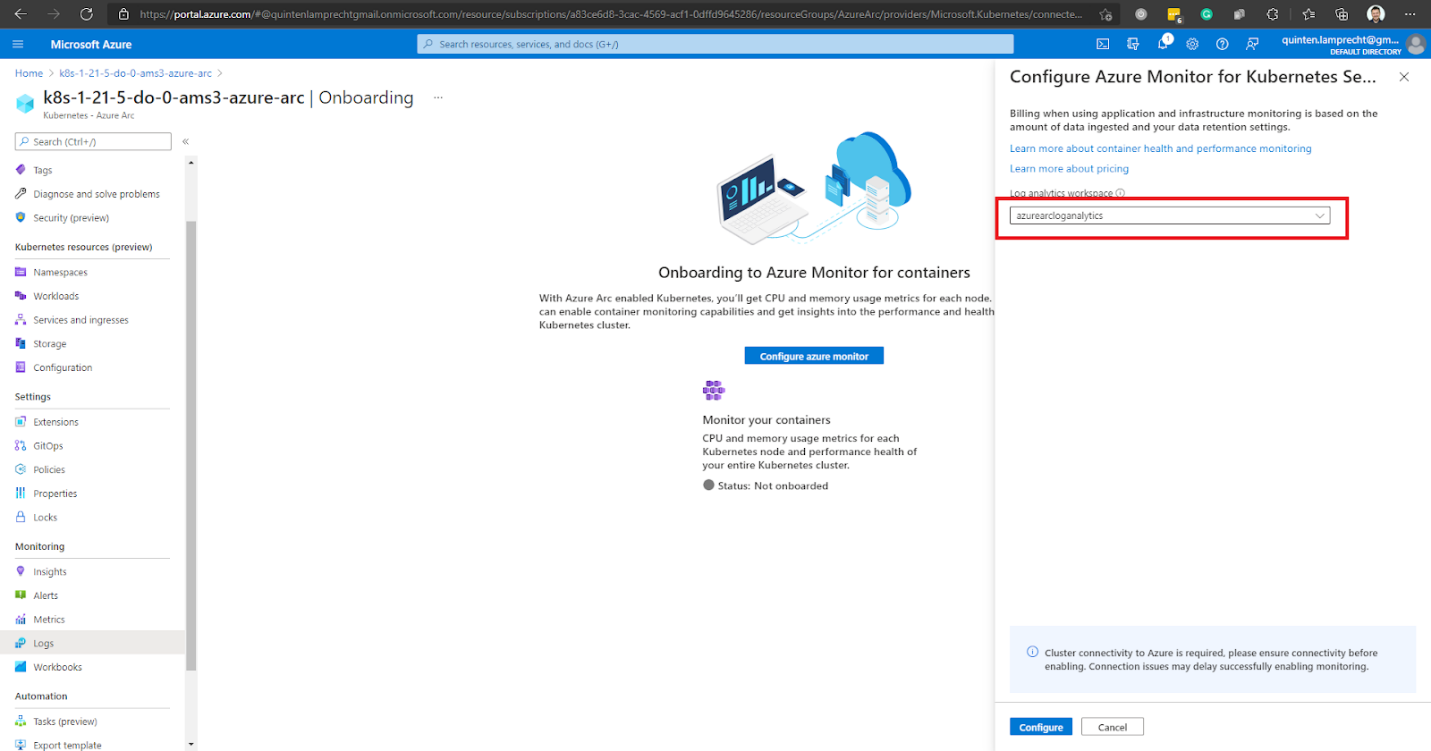
The onboarding may take a few seconds to complete. Azure will notify us when it’s ready.
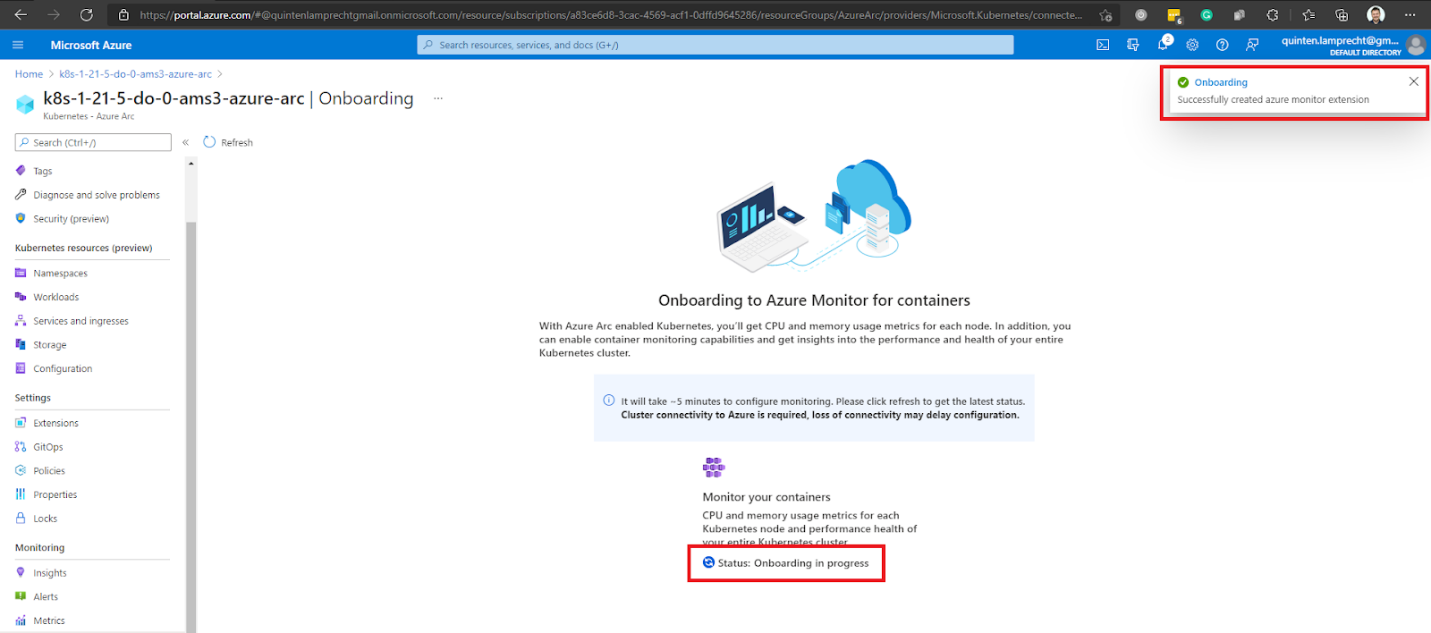
We can access the monitoring options in our Azure Arc-enabled Kubernetes cluster’s navigation pane when the onboarding is complete. For example, Insights displays all the information about our cluster.
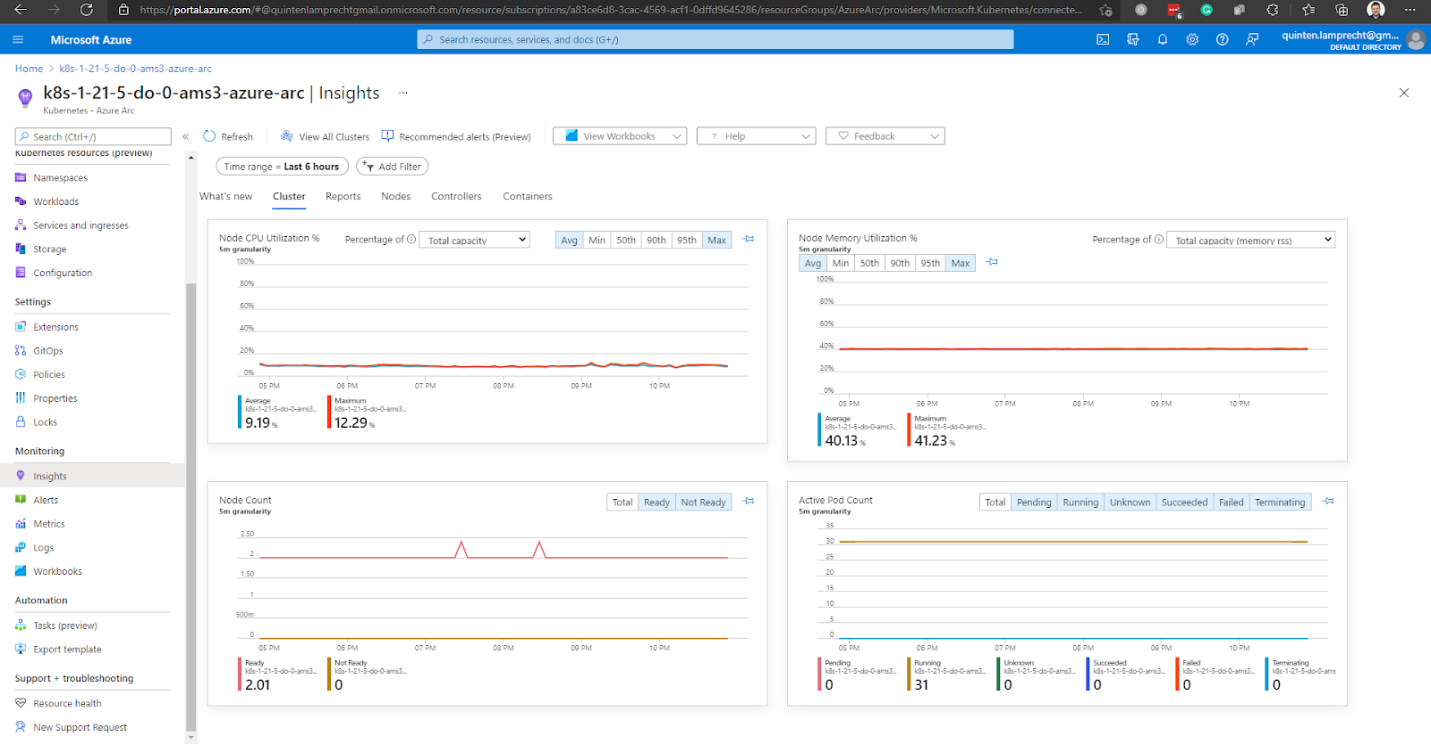
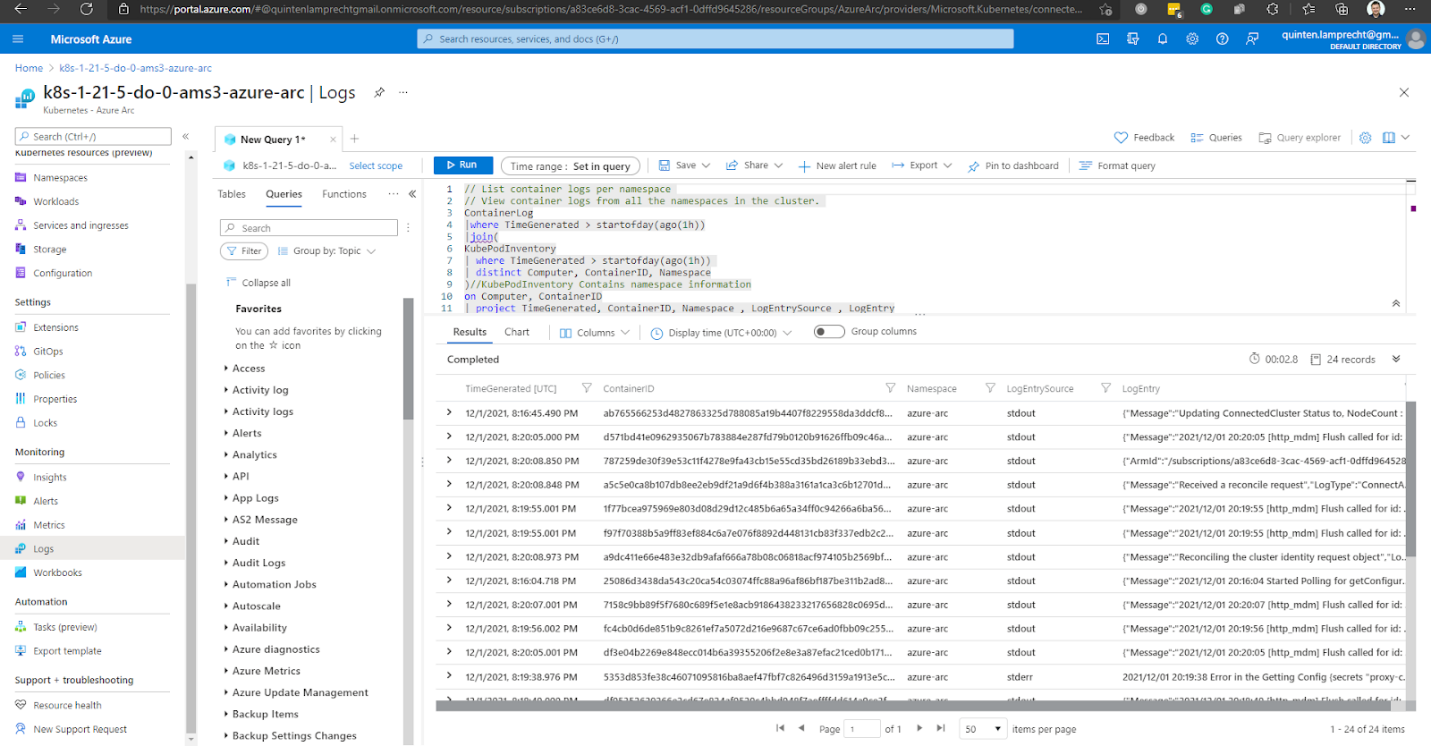
Or, we can explore and query the Logs.
Azure Monitor’s functions:
- Monitor performance of Kubernetes clusters and their nodes
- Identify containers running on nodes and their average processor and memory use
- Identify the container’s location within a controller or pod
- Understand the cluster’s behavior under average and heaviest loads
- Integrate with tools like Prometheus and Grafana to view application workload metrics they collect from nodes and Kubernetes using queries
Next Steps
In this tutorial, we installed the Microsoft Defender extension to our Azure Arc-enabled Kubernetes cluster and discussed why we should enable Microsoft Defender. We have also added Azure Monitor to our cluster and explored its functions and insights.
Sign up to try Azure Arc for yourself or at your organization, or continue to the third (and final) article of this series to learn how to deploy containers to your Kubernetes clusters using Azure Arc.
To learn more about how to get started with Azure Arc-enabled Kubernetes or how Azure Arc-enabled Kubernetes allows you to attach and configure Kubernetes clusters running anywhere, check out our resource page on Azure Arc Enabled Kubernetes.
