The document introduces Microsoft Azure's private subnet feature for heightened security, detailing its setup and integration with Azure Bicep for efficient network management.
Introduction
Microsoft Azure continues to evolve its cloud services, prioritizing security and flexibility for its users. The latest addition is the ability to create private subnets, an important feature for any organization concerned with network security and efficient management. In this blog post, we will explore this new feature, its benefits, and how to implement it in various scenarios.
Understanding the New Feature
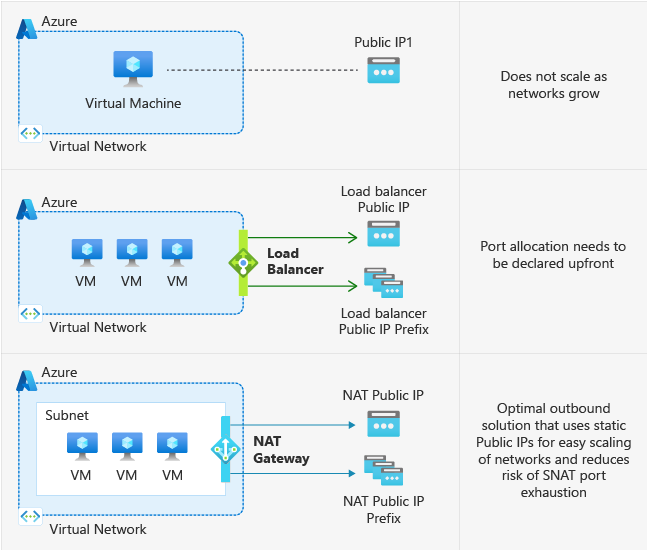
Traditionally, when virtual machines (VMs) are created in Azure without any explicit outbound connectivity, they are assigned a default outbound public IP address. These implicit IPs, subject to change and not associated with a subscription, present challenges in troubleshooting and do not align with Azure’s “secure by default” model. This model ensures robust security without requiring additional steps from the customer.
Depreciation of Implicit Connectivity
Azure announced the depreciation of this type of implicit connectivity, scheduled for September 2025. This shift underlines the importance for Azure users to adapt to more secure and controlled network configurations, like the private subnet feature.
Setting Up Private Subnets
Creating a private subnet in Azure is straightforward. When setting up a new subnet, you can prevent insecure implicit connectivity by setting the “default outbound access” parameter to false. This allows you to choose a preferred method for explicit outbound connectivity.
Deep Dive into Implementation Scenarios
Let’s explore how to implement private subnets in various Azure configurations:
1. Subnet Associated with a NAT Gateway
Creating a subnet within a NAT gateway provides controlled access to the internet. Here’s how to do it:
- In the Azure portal, create a new Virtual Network and Subnet.
- Go to the ‘Subnet’ section and disable the ‘default outbound access’.
- Create a NAT gateway and associate it with your subnet.
- Configure the NAT rules as per your requirements.
2. Standard Load Balancer with Outbound Rules
For a subnet in the backend pool of a standard load balancer:
- Create a standard load balancer.
- Add the subnet to the backend pool.
- Define outbound rules to control the traffic flow.
3. Basic Public Load Balancer
Integrating with a basic public load balancer:
- Set up a basic load balancer.
- Add the private subnet to its backend pool.
- Ensure outbound rules are configured for traffic management.
4. Virtual Machines with Explicit Public IPs
To associate public IPs explicitly with VMs in a private subnet:
- Create VMs in your private subnet.
- Allocate public IP addresses and associate them with your VMs explicitly.
Additional Resources and Documentation
For more detailed information on private subnets and default outbound access in Azure, refer to Azure’s official documentation. This documentation provides comprehensive guides and examples for different network configurations.
Integrating Azure Bicep for Network Interface Configuration
When configuring private subnets in Azure, leveraging the power of Infrastructure as Code (IaC) can streamline and enhance the process. Azure Bicep, a declarative language for Azure resource deployment, offers a robust and efficient way to define and deploy network resources, including network interfaces.
Example: Defining a Subnet with Azure Bicep
This example shows a basic Bicep script to define a subnet within a virtual network. The script sets up a subnet with specific properties, aligning with Azure’s best practices for network security.
resource myVnet 'Microsoft.Network/virtualNetworks@2020-11-01' = {
name: 'myVirtualNetwork'
location: resourceGroup().location
properties: {
addressSpace: {
addressPrefixes: [
'10.0.0.0/16'
]
}
subnets: [
{
name: 'mySubnet'
properties: {
addressPrefix: '10.0.0.0/24'
delegations: []
privateEndpointNetworkPolicies: 'Enabled'
privateLinkServiceNetworkPolicies: 'Enabled'
serviceEndpoints: []
serviceEndpointPolicies: []
disableOutboundSnat: true
}
}
]
}
}
Note: This is a basic example for illustrative purposes. For a complete and practical implementation, always refer to the official Azure Bicep documentation and the most up-to-date templates.
Example: Creating a Network Interface with Azure Bicep
Below is a conceptual example of how you might use Azure Bicep to create a network interface. This script defines a basic network interface, linking it to a specified virtual network and subnet.
resource networkInterface 'Microsoft.Network/networkInterfaces@2020-11-01' = {
name: 'myNetworkInterface'
location: resourceGroup().location
properties: {
ipConfigurations: [
{
name: 'ipconfig1'
properties: {
subnet: {
id: resourceId('Microsoft.Network/virtualNetworks/subnets', 'myVirtualNetwork', 'mySubnet')
}
privateIPAllocationMethod: 'Dynamic'
}
}
]
}
}
Note: This code is a simplified example. For actual implementation, you should refer to the Azure Bicep network interface module for comprehensive templates and guidelines.
Benefits of Using Azure Bicep for Network Configurations
- Automation and Efficiency: Azure Bicep simplifies the deployment of network resources, making the process more efficient and less error-prone.
- Version Control and Reusability: Bicep templates can be version-controlled and reused, ensuring consistency across deployments.
- Integration with Azure Ecosystem: Bicep is designed to work seamlessly with other Azure services and tools, providing a cohesive experience for Azure network management.
By integrating Azure Bicep into your network deployment strategy, especially when configuring private subnets, you can achieve greater control, scalability, and security in your Azure environment.
Conclusion
Azure’s new private subnet feature marks a significant step towards enhanced network security and management. By understanding and implementing this feature, Azure users can ensure their virtual networks are secure and compliant with the latest cloud networking standards. We encourage our readers to share their experiences and questions in the comments section below.
