Azure leads cloud evolution with Hybrid Solutions and Automation Runbooks, revolutionizing IT management practices for hybrid and SOC environments. This technical dive explores Azure's role in managing complex infrastructures.
The cloud computing has undergone significant evolution by 2024, with Azure leading the charge in providing robust solutions for managing complex, hybrid IT infrastructures. Azure Automation Runbooks have become an indispensable tool, particularly when integrated with the Hybrid Runbook Worker feature. This technical dive explores the functionality and strategic application of Runbooks in managing hybrid and SOC environments.
Hybrid Cloud Automation
The Hybrid Cloud Model
Hybrid environments have become the standard operating model for many organizations, blending on-premises data centers with cloud services for a flexible, scalable IT infrastructure. Azure Automation Runbooks facilitate the movement and management of resources between these environments.
Why is this important? We learned in the past that a lift and shift is not always the best practice and can be very expensive. You see organization shift to a hybrid cloud model. To monitor these environments from a single environment, which in 2024 will most likely be with cloud based solutions, the Azure Automation can provide a lot of benefits to manage on-premise resource within the cloud based monitoring and management tools.
Hybrid Runbook Workers
The Hybrid Runbook Worker feature allows engineers to execute automation tasks directly on the machines hosting the resources. This direct execution is essential for tasks that cannot be migrated to the cloud due to latency, sensitivity, or compliance reasons. This can integrate perfectly with your current network topologies, express route, vpn site-to-site tunnels to get even more security and performance.
Advantages for Hybrid Operations
- Proximity to On-Premises Resources: Directly manage resources that reside on local servers or within private data centers.
- Optimized Performance: Execute automation tasks with minimal delay, an essential factor for time-sensitive operations.
- Regulatory Compliance: Regulatory requirements by processing and storing sensitive data on-premises.
- Flexible Resource Management: Adjust automation strategies dynamically to accommodate fluctuating workloads.
- Cost reduction: Minimizing the toolbox on on-premises and cloud will reduce the administrating cost of your organization, since you have on environment tool set to keep up instead of both.
Hybrid Automation Solutions
Deploying Runbooks in hybrid environments requires a understanding of network configurations, security parameters, and access controls.
- Network Configuration: Engineers must ensure that the hybrid runbook worker VM is placed within a subnet that has the necessary connectivity to both the on-premises environment and Azure services.
- Security and Access: By restricting access to the runbook worker VM to authorized SOC team members, engineers can maintain tight security controls over their automated tasks.
- Runbook Design and Efficiency: The creation of runbooks should follow best practices that prioritize efficiency, maintainability, and scalability.
Create a Runbook in the Azure Portal
- Sign in to the Azure portal.
- Search for and select Automation Accounts.
- On the Automation Accounts page, select your Automation account from the list.
- From the Automation account, select Runbooks under Process Automation to open the list of runbooks.
- Click Create a runbook.
- Name the runbook.
- From the Runbook type drop-down, select its type. The runbook name must start with a letter and can contain letters, numbers, underscores, and dashes
- Select the Runtime version
- Enter applicable Description
- Click Create to create the runbook.
Create a Runbook with PowerShell
Use the New-AzAutomationRunbook cmdlet to create an empty runbook. Use the Type parameter to specify one of the runbook types defined for New-AzAutomationRunbook.
The following example shows how to create a new empty runbook.
$params = @{
AutomationAccountName = 'MyAutomationAccount'
Name = 'NewRunbook'
ResourceGroupName = 'MyResourceGroup'
Type = 'PowerShell'
}
New-AzAutomationRunbook @params
Import a Runbook
You can import a PowerShell or PowerShell Workflow (.ps1) script, a graphical runbook (.graphrunbook), or a Python 2 or Python 3 script (.py) to make your own runbook. You specify the type of runbook that is created during import, taking into account the following considerations.
- You can import a .ps1 file that doesn’t contain a workflow into either a PowerShell runbook or a PowerShell Workflow runbook. If you import it into a PowerShell Workflow runbook, it is converted to a workflow. In this case, comments are included in the runbook to describe the changes made.
- You can import only a .ps1 file containing a PowerShell Workflow into a PowerShell Workflow runbook. If the file contains multiple PowerShell workflows, the import fails. You have to save each workflow to its own file and import each separately.
- Do not import a .ps1 file containing a PowerShell Workflow into a PowerShell runbook, as the PowerShell script engine can’t recognize it.
- Only import a .graphrunbook file into a new graphical runbook.
Import a Runbook With Powershell
Use the Import-AzAutomationRunbook cmdlet to import a script file as a draft runbook. If the runbook already exists, the import fails unless you use the Force parameter with the cmdlet.
The following example shows how to import a script file into a runbook.
$params = @{
AutomationAccountName = 'MyAutomationAccount'
Name = 'Sample_TestRunbook'
ResourceGroupName = 'MyResourceGroup'
Type = 'PowerShell'
Path = 'C:\Runbooks\Sample_TestRunbook.ps1'
}
Import-AzAutomationRunbook @params
Publish a Runbook
When you create or import a new runbook, you have to publish it before you can run it. Each runbook in Azure Automation has a Draft version and a Published version. Only the Published version is available to be run, and only the Draft version can be edited. The Published version is unaffected by any changes to the Draft version. When the Draft version should be made available, you publish it, overwriting the current Published version with the Draft version.
Publish a Runbook in the Azure Portal
- In the Azure portal, search for and select Automation Accounts.
- On the Automation Accounts page, select your Automation account from the list.
- Open the runbook in your Automation account.
- Click Edit.
- Click Publish and then select Yes in response to the verification message.
Publish a Runbook using PowerShell
Use the Publish-AzAutomationRunbook cmdlet to publish your runbook.
$accountName = "MyAutomationAccount"
$runbookName = "Sample_TestRunbook"
$rgName = "MyResourceGroup"
$publishParams = @{
AutomationAccountName = $accountName
ResourceGroupName = $rgName
Name = $runbookName
}
Publish-AzAutomationRunbook @publishParams
Schedule a Runbook in the Azure Portal
When your runbook has been published, you can schedule it for operation:
- In the Azure portal, search for and select Automation Accounts.
- On the Automation Accounts page, select your Automation account from the list.
- Select the runbook from your list of runbooks.
- Select Schedules under Resources.
- Select Add a schedule.
- In the Schedule Runbook pane, select Link a schedule to your runbook.
- Choose Create a new schedule in the Schedule pane.
- Enter a name, description, and other parameters in the New schedule pane.
- Once the schedule is created, highlight it and click OK. It should now be linked to your runbook.
- Look for an email in your mailbox to notify you of the runbook status.
Restore Deleted Runbook
You can recover a deleted runbook through PowerShell scripts. To recover a runbook, ensure that the following conditions are met:
- The runbooks to be restored were deleted in the past 29 days.
- The Automation account for that runbook exist.
- The Automation Contributor role permission is granted to the System-assigned managed identity of the Automation account.
PowerShell Script
- Execute the PowerShell script as a job in your Automation account to restore the deleted runbooks.
- Download the PowerShell script from GitHub. Alternatively, you can import the PowerShell script named Restore Automation runbook from Runbook Gallery. Provide the name of the runbook that is to be restored and run it as a job in Azure Automation to restore the deleted runbooks.
- Download the script from GitHub or import the PowerShell script named List Deleted Automation Runbook from Runbook Gallery, to identify the names of the runbooks that were deleted in last 29 days.
I want to guide you through the utilization of one of Azure Automation’s most recent updates – the General Availability of PowerShell 7.2 runbooks. With the support for the long-term stable version of PowerShell, your automation practices are about to get a major upgrade.
The transition to PowerShell 7.2 is keeping up with the latest trends. Given that PowerShell 7.1 is no longer supported, it’s imperative for the continuity and security of your scripts to adopt PowerShell 7.2 for your runbooks. This move isn’t just recommended—it’s essential for any professional looking to maintain and future-proof their automation infrastructure.
Automation for SOC Teams
A Customer Use Case
In the cybersecurity domain, SOC teams rely on automation to manage digital evidence and respond to incidents. Azure Automation Runbooks provide a structured and secure method for SOC teams to automate these critical tasks.
Consider to use new technologies as the use of benefits of managed XDR solutions like Azure Sentinel to manage your on-premise and cloud resources. Make a list of benefits and costs, and make a choice based on your organisations needs and target-architecture to provide a future proof solution.
The Role of Hybrid Runbook Worker VM in SOC Tasks
For SOC teams, the hybrid runbook worker VM is configured to run specific runbooks such as the Copy-VmDigitalEvidence. This enables SOC teams to automate the collection and preservation of digital evidence from virtual machines, a task that is critical for forensic analysis and incident response.
Detailed Configuration for SOC Workflows
- Network and Access: The worker VM must be configured with network rules that allow it to access the necessary Azure storage accounts while maintaining strict access controls to SOC team members for maintenance activities.
- Isolation and Managed Identity: The virtual network for the SOC VM should be isolated from the central network to prevent unauthorized access, utilizing Azure’s managed identities for secure and streamlined access to Azure resources.
Runbooks for SOC Engineering
SOC engineers must design runbooks that can handle the demands of cybersecurity tasks, which often require rapid execution and strict adherence to compliance protocols.
Diagrammatic Overview of Azure Automation for SOC
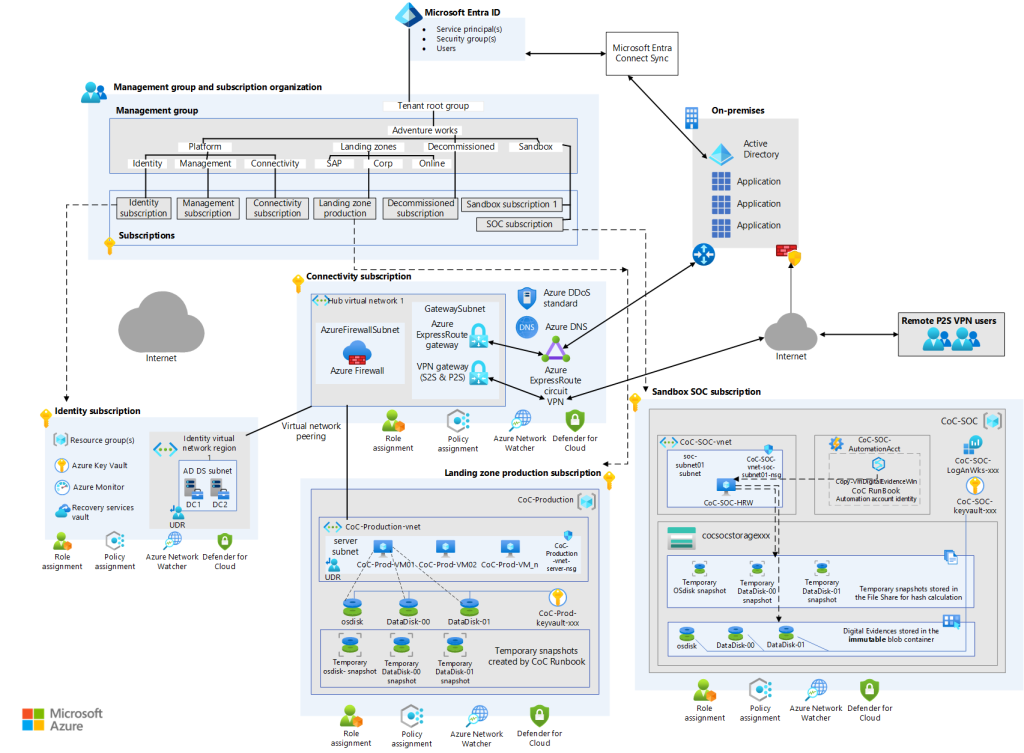
Diagram: The architecture showcases the integration of Azure Automation Runbooks with the Hybrid Runbook Worker VM in a SOC environment.
Diagram Explanation
- Connectivity Subscription: It outlines the networking components like Azure Firewall, VPN gateway, and Azure DDoS protection, ensuring secure and resilient connectivity.
- Identity Subscription: Here, we see the infrastructure supporting identity management, including Azure Key Vault and Azure AD, which are critical for managing credentials and access policies.
- Landing Zone Production Subscription: This section illustrates the core production environment where the primary workloads reside.
- Sandbox SOC Subscription: It represents the isolated environment dedicated to SOC operations, containing the Hybrid Runbook Worker VM and the associated storage accounts for evidence handling.
Automating Security Workflows
SOC teams are tasked with monitoring security alerts. Azure Automation runbooks can be programmed to respond to these alerts automatically.
- Alert Response: Runbooks can be triggered by security alerts from Azure Monitor. For example, if an alert is raised about a potential breach, a runbook can immediately begin the process of isolating affected systems or accounts.
- Threat Hunting: Runbooks can automate the search for patterns of malicious activity across the network and endpoints. They can aggregate data from logs, analyze patterns, and flag anomalies for further investigation.
- Automated Patching: Keeping systems up-to-date is vital for security. Runbooks can automate the deployment of patches to on-premises and cloud environments, ensuring that all systems are updated quickly in response to vulnerability announcements.
Incident Response
When a security incident occurs, time is of the essence. Runbooks can be part of an orchestrated response to incidents, reducing the time to remediate.
- Forensic Collection: Runbooks can gather data from systems for forensic analysis, packaging logs, system snapshots, and other relevant information for SOC analysts to review.
- Containment Actions: To prevent the spread of an attack, runbooks can execute containment measures such as blocking IPs, disabling accounts, or disconnecting machines from the network.
- Communication: Runbooks can also automate communication, sending notifications to stakeholders and updating incident response tickets with the latest information.
My Advice: Azure Automation Runbooks with Azure Sentinel
We’ve delved into the intricacies of crafting a runbook, exploring its benefits and Microsoft’s best practices. You might wonder, why is this important? My goal is to demystify the fundamentals and offer you practical advice for leveraging these tools straight out of the gate. I aim to demonstrate the robust capabilities of Microsoft Azure Cloud — capabilities that extend their reach even into your on-premise environment. Through this, you’ll gain a deeper appreciation of how Azure can streamline and enhance your operational management.
My advise implement Azure Sentinel, serves as a cloud-native SIEM (Security Information and Event Management) system that provides security analytics and threat intelligence across the enterprise. By combining it with Azure Automation, you can streamline your security operations and automate responses to threats detected by Sentinel.
Automated Threat Detection and Response
- Azure Sentinel Detection: Sentinel continuously collects data from various sources, including on-premises environments, using connectors. It applies advanced analytics and AI to detect potential security threats.
- Alerts and Playbooks: Once a threat is identified, Sentinel generates an alert. For each alert type, you can configure an Azure Automation runbook as a playbook in Sentinel. This playbook is automatically triggered to respond to the alert. (out-of-the-box without touch of development or creating your own runbooks, based on Microsoft best practices)
- Runbook Execution: The triggered runbook, hosted in Azure Automation, can perform a wide range of remediation tasks such as disabling user accounts, isolating compromised machines, or gathering evidence for further investigation.
Compliance and Security Posture Management
- Security Posture Assessment: Azure Automation runbooks can continuously assess the security posture of on-premises environments and log the findings in Sentinel.
- Compliance Reporting: Runbooks can generate compliance reports based on the data collected and feed them into Sentinel, where they can be reviewed and acted upon.
- Automated Remediation: For identified compliance gaps, Sentinel can trigger runbooks to automatically remediate issues where possible, or create incidents for manual intervention.
Forensics and Incident Response
- Forensic Data Collection: When Sentinel detects a high-severity incident, it can trigger a runbook to collect forensic data from the affected on-premises system, such as system and application logs, memory dumps, and snapshots. (also from on-premise!)
- Incident Management: Runbooks can integrate with incident management workflows within Sentinel, updating incidents with actions taken, evidence collected, and providing a detailed response timeline.
- Evidence Preservation: Runbooks ensure that evidence collected is securely stored in a manner that preserves its integrity for future analysis or legal proceedings.
SOC Operations and Automation
- Workflow Automation: Sentinel’s playbooks, powered by Azure Automation runbooks, can automate entire SOC workflows, orchestrating complex multi-step processes that span across cloud and on-premises environments.
- Secure Access Management: Runbooks can manage access control by updating firewall rules or network security groups in response to an incident, directly from within the Sentinel platform.
- Custom Playbook Actions: SOC teams can create custom runbooks for unique scenarios specific to their organization’s infrastructure, which can be triggered from Sentinel as part of the playbook actions.
By integrating Azure Sentinel with Azure Automation, SOC teams can create a highly responsive and automated environment to manage security across their entire digital estate (yes, also on-premise). This enhances the security response capabilities but also significantly reduces the manual workload on SOC analysts, allowing them to focus on strategic security initiatives. Allows the team to use the Microsoft managed solutions and best practices even faster.
