Lots of folks, have read about XSS and said to me so what, what’s the worst that’s going to happen? Might site might get defaced or, some cookies might get stolen (but I don’t use cookie data). I am relatively safe and I don’t need to worry about XSS vulnerabilities because no real damage can come from said vulnerabilities. To close off everything I’ve said about XSS and move onto a new security topic I thought it only fitting that I prove everyone who’s ever said XSS isn’t a serious vulnerability wrong.
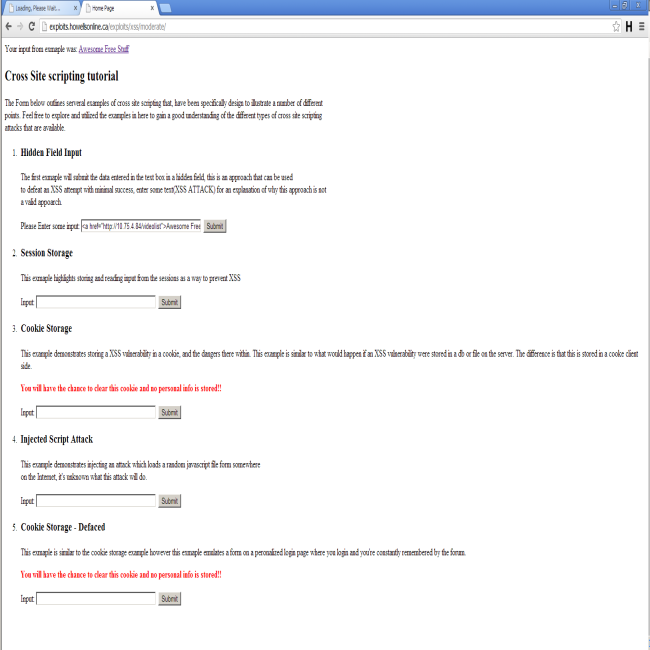
I am going to revisit my moderate XSS page that I created which can be found here. I am just going to easily exploit
a well know XSS vulnerability on the page. In the first text box I am going to type: <a href="http://10.75.4.84/videolist">Awesome Free Stuff </a>.
This could be an XSS vulnerability that is entered into your site through any means that I’ve already discussed and beaten to death. It could be a reflected or stored XSS attack. When the victim visits the page. They see a normal looking website, with a link stating click here to get free, stuff everyone likes free stuff right? So this is what the victim sees.
Being a trusting victim and not understanding much about the Internet as the majority of users don’t. They click on the link to get their awesome free stuff. Immediately when the access the link they’re presented with a security popup, that looks like this.

No cause for concern yet right? Being the unsuspecting victim I know about Adobe and know that they’re relatively safe and a well known company therefore I should be safe enough to run whatever Adobe wants to give me. So as the unsuspecting victim I think this is cool and I run it.
You’ve just become a victim and given an attacker access to my system
But wait a minute how is that possible you say?
Well lets look at what has gone on. When an attacker was able to successfully exploit an XSS vulnerability on a victim website (in in this exploits.howellonline.ca/xss/moderate their exploit payload included this:
http://10.75.4.84/videolist.
Which actually links back to a malicious server that the attacker is running. So lets have a look at what is happening on that server. The attacker had set up a reverse listener that established a connection to the victims computer as soon as they clicked accept. In the image I’ve taken from my attacker machine you can clearly see that a request has been made of the attacker machine, the payload is being sent, as soon as the user clicks accept a reverse session is opened.

Now all the attacker has to do is figure out which session they want to exploit. As you can see from the image below 3 other people have already fallen victim to the attacker through the exploit the attacker was able to inject on the victim website.

As soon as the attacker picks as session, they now have a backdoor directly into the victim’s computer. So lets Recap for a minute. An attacker found a victim website, was able to get their XSS attack stored, (perhaps) in the database, When victim user’s visited the victimized website, they clicked on the XSS attack which allowed the attacker to open a back door into their machine, therefore the website user has also become a victim and was the real target here. Looking at the image below we can see the attacker already knows some information about their victim.

There’s probably nothing good in the Firefox folder for the attacker, but they can quickly escape the firefox folder and move to the root of the C:\. Or some other more interesting folder. Here the all the files are viewed along with their rights on the victims machine.

Here I exploited a java vulnerability, however there are many other vulnerabilities that I could have used instead, any plugin with firefox a few with chrome. The possibilities are endless. I haven’t needed to guess a password, know a user name, as you can see I can read just about any file and it’s contents, I can execute some I could download some or now that I am in upload my own malicious content. I could access the windows directly and mess up in there. Or attempt to access other computers on the network, that this machine is connected too. This exploit has been brought to you by an XSS attack. Essentially I victimized a website so I could victimized the end users of said website. As you can clearly see XSS vulnerabilities need to be taken a lot more seriously then they have in the past.
Don’t let your users become victims because of your website!
With this particular attack I didn’t need an advanced knowledge of programming networks or security. I needed to find a vulnerable website, have access to the Internet and access to a program called Metasploit. Thus with a few basic tools anybody can become an attacker. It’s easy enough to find a vulnerable website, free proxies such as ZAP will help you find various XSS vulnerabilities, there are tons of tutorials on the Internet explaining how to use the various Metasploit vulnerabilities and Metasploit is freely Available. In this case I used Kali Linux but you don’t even need an understanding of Linux.
If I was interested in being more professional and making that URL look more legitimate what might I do?
Well I would probably create a non suspecting domain name. Point my DNS record at my servers static IP address construct a well thought out path and voila. Remember I had my attacking machine listening on port 80. Which is pretty much going to be open without question so the URL isn’t even going to look suspicious to the unsuspecting user.
If I can do enough to open a back door into your computer without even needing a knowledge of programming chances are that I don’t need a knowledge of programming to find a payload to my liking either. A knowledge of security certainly helps but… with things becoming so easy. It is ever important as Software engineers, developers Be ever vigilant against any XSS vector in our site regardless of how insignificant we might think that it is.
As users however we need to understand engineers are human and are going to make mistakes and therefore we need to be vigilant ourselves. We need to be cautious about what we allow to run on our computers never authorizing something that we are unsure of. As I tell my grandmother in all instances Google is your friend and if you don’t know as a colleague of mine would say ” to the google” beyond not granting permission to security warnings we are unsure of. If you’re on a website say www.domain.com and a link you activate attempts to redirect you or load up something like www.foo.com. You should immediate close the tab or return to a safe corner of the Internet as you know it. So too never ever run anything on the suspect domain. Like ww, foo, Com, especially if you do not recognize it and have not navigated there under your own intention.
