The SQL professionals know that the built-in MS SQL Server encryption mechanism by means of WITH ENCRYPTION T-SQL keyword is ineffective and easily broken. For much more details see also Google’s results e.g.:
{3S} SQL Smart Security is an add-in which can be installed in Microsoft SQL Server Management Studio (SSMS) 2005, 2008, 2008 R2, 2012 and their respective Express versions. It enables software companies to create a secured content for database objects (note: currently, in 1.1 version can be secured only the content of stored procedures, but in the future, there are considered user defined functions, triggers and views as well). It brings much higher level of protection in comparison with SQL Server built in WITH ENCRYPTION mechanism for software companies that want to protect their heavily acquired know-how by creation of application logic on the database server side on a daily basis.
None of the currently available SQL decryptors are capable of cracking {3S} SQL Smart Security. Most importantly, all encrypted database objects remain executable! Moreover, installing {3S} SQL Smart Security does not affect any settings and does not replace default encryption options entirely. The developers (end-users) always have an option to choose which encryption settings to use.
See a short story of a simple hack by means of built-in MS SQL Server WITH ENCRYPTION mechanism on the example bellow.
WARNING: In the following examples, an excellent free tool called dbForge SQL Decryptor by the Devart (formerly known as Core Lab) software development company will be used for educational purposes, only for decrypting the stored procedure.
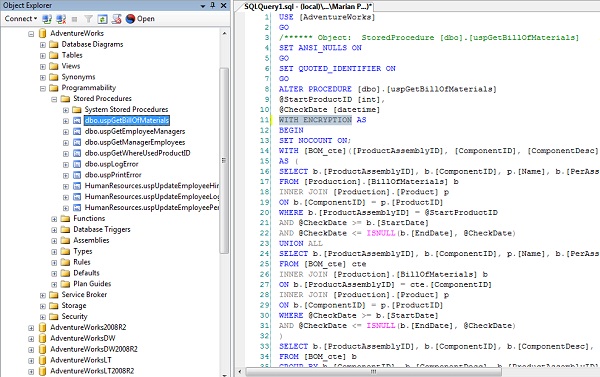
Figure 1: built-in WITH ENCRYPTION hack – stored procedure encryption by means of built-in MS SQL Server WITH ENCRYPTION mechanism
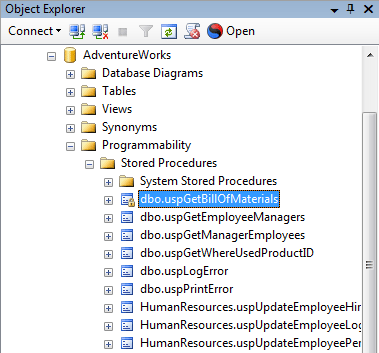
Figure 2: built-in WITH ENCRYPTION hack – lock on encrypted stored procedure by means of built-in MS SQL Server WITH ENCRYPTION mechanism
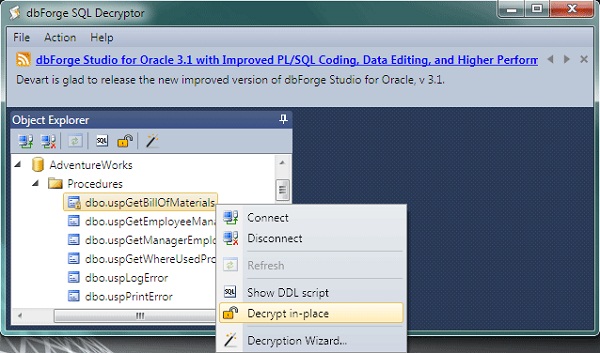
Figure 3: built-in WITH ENCRYPTION hack – stored procedure decrypting by means of dbForge SQL Decryptor
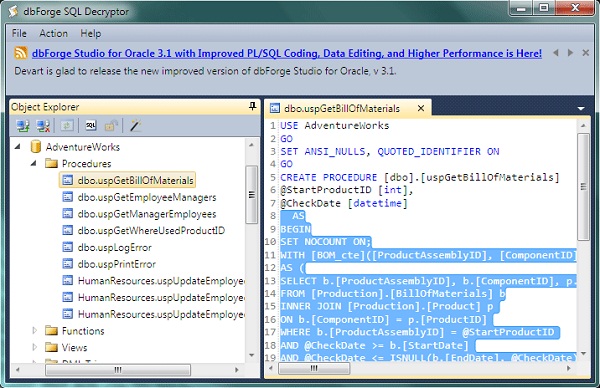
Figure 4: built-in WITH ENCRYPTION hack – decrypted stored procedure by means of dbForge SQL Decryptor
By applying dbForge SQL Decryptor to the encrypted stored procedure by means of built-in MS SQL Server WITH ENCRYPTION mechanism it is possible to see that the stored procedure body IS A PLAIN SOURCE CODE TEXT!!!
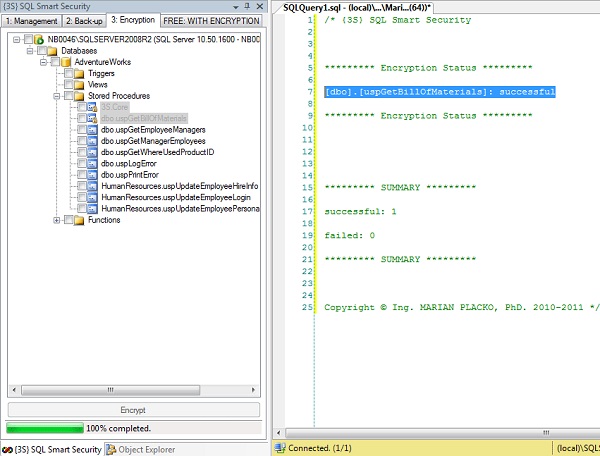
Figure 5: built-in WITH ENCRYPTION hack – encrypted stored procedure by means of {3S} SQL Smart Security
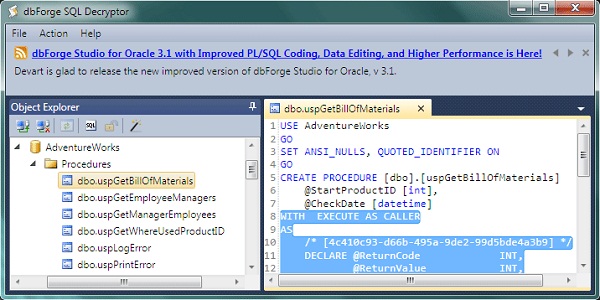
Figure 6: built-in WITH ENCRYPTION hack – decrypted {3S} SQL Smart Security stored procedure by means of dbForge SQL Decryptor
By applying dbForge SQL Decryptor to the encrypted stored procedure by means of {3S} SQL Smart Security it is possible to see that the stored procedure body IS NOT A PLAIN SOURCE CODE TEXT but includes the {3S} SQL Smart Security metadata only!!!
Additional references:
