When devices are connected via Ethernet cables, traffic can be readout by direct connections or RF leakage. Local wireguard tunnels in all LAN connections will make ethernet cables secure. Connecting the main router to VPN will negate traffic leak on the other side. This article describes achieving both these objectives.
Introduction
Ethernet cables have two problems. 1) They are open to traffic inspection. 2) They are prone to RF leakage, enabling reconstruction of traffic. When we connect our local routers to each other using regular Ethernet cables, we are open to spying on traffic, even though they are HTTPS connections, data mining can be done. This can be mitigated by securing local connections with Wireguard tunnels and enabling WPA3 WiFi on wireless devices. Internet from our ISPs is also insecure as those connections tend to leak data that will lead to internet habit reconstruction, hence people generally use VPNs for mitigating it. This article describes achieving these objectives using OpenWRT routers.
The diagram below shows the general idea of a secure local network.
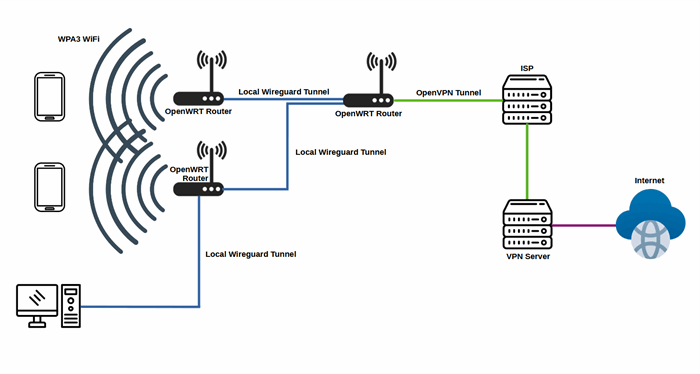
The Wireguard tunnels between local devices is necessary for securing the connections when Ethernet cables are used instead of WPA3 WiFi. The next section of the article describes connecting two OpenWRT routers using a Wireguard connection, so that the Wireguard tunnel will be used as WAN of the other router.
Prerequisites
To implement this article, you need either two routers flashed with OpenWRT or one OpenWRT router and a client with wireguard installed (Windows PC with LAN). You can skip appropriate sections. You need to enable LAN and WiFi on the OpenWRT routers. Install the following packages on OpenWRT routers and restart.
opkg update
opkg install wireguard-tools luci-proto-wireguard
Local Wireguard Tunnel Implementation
First step is to configure Wireguard as a server on a OpenWRT router. We are configuring two servers with a peer each. Read about wireguard further here and here.
Wireguard Server on OpenWRT Router
Add the following lines to /etc/config/network file to create the server, assign the interface to LAN firewall zone.
...
config interface 'wgserver'
option proto 'wireguard'
option private_key '<private key of server1>'
option listen_port '51820'
list addresses '192.168.9.1/24'
option mtu '2000'
config wireguard_wgserver
option description 'desktop'
option public_key '<public key of peer1>'
option private_key '<private key of peer1>'
option preshared_key '<preshared key of peer1>'
list allowed_ips '0.0.0.0/0'
config device
option name 'wgserver'
option ipv6 '0'
option acceptlocal '1'
config interface 'wgserver_r1'
option proto 'wireguard'
option private_key '<private key of server2>'
option listen_port '51821'
list addresses '192.168.91.1/24'
option mtu '2000'
config wireguard_wgserver_r1
option description 'router1'
option public_key '<public key of peer2>'
option private_key '<private key of peer2>'
option preshared_key '<preshared key of peer2>'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
config device
option name 'wgserver_r1'
option ipv6 '0'
option acceptlocal '1'
Add the following lines to /etc/config/firewall, the lines in bold are to be added
...
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wifi24'
list network 'wifi50'
list network 'wgserver'
list network 'wgserver_r1'
...
Restart router, check if interface has indeed appeared and assigned to proper firewall zone in luci.
Wireguard Client on Windows
https://www.wireguard.com/install/ will contain all the clients, please install them. On windows add the following tunnel configuration.
[Interface]
PrivateKey = <private key>
Address = 192.168.9.7/32
DNS = 8.8.8.8
[Peer]
PublicKey = <public key>
PresharedKey = <pre shared key>
AllowedIPs = 0.0.0.0/1, 128.0.0.0/1
Endpoint = 192.168.10.1:51820
Where 192.168.10.1 is replaced by the local gateway of br-lan or similar interface. Check internet access after connecting to tunnel. If successful, your tunnel works properly.

Wireguard Client on OpenWRT router
Follow this section if you have a second OpenWRT router. Wireguard configured as a client replaces WAN as its internet access automatically. This forces all clients of the router to use the tunnel as internet source and internet won't work if tunnel is improperly.
Add the following lines to /etc/config/network of the client router.
...
config interface 'wgc'
option proto 'wireguard'
option private_key '<private key>'
list dns '8.8.8.8'
option mtu '2000'
list addresses '192.168.91.8/32'
config wireguard_wgc
option description 'Imported peer configuration'
option public_key '<public key>'
option preshared_key '<preshared key>'
list allowed_ips '0.0.0.0/0'
option endpoint_host '192.168.10.1'
option endpoint_port '51821'
option route_allowed_ips '1'
option persistent_keepalive '20'
Assign the interface to WAN firewall zone by adding the following lines to /etc/config/firewall
...
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'wgc'
...
Restart the router and check if internet data is flowing through the interface and on the router's WiFi clients.
OpenWRT VPN Installation on OpenWRT Router.
Refer to the following article for instructions to adding resilient VPN to OpenWRT router. Link here. The current section requires the VPN to be setup in the said manner described in the linked article. The remaining steps in this article are to add Wireguard servers to custom table created in the article mentioned, for the Wireguard servers to use the OpenVPN tunnel 'tun0' for internet traffic.
Modifying Kill Switch Scripts
1) Add a file /etc/kill-switch/kill-switch-setup-wgserver.sh with following contents in the router configured for resilient VPN. Make the file executable.
/etc/openvpn/kill-switch/activate-kill-switch-for-interface.sh 192.168.9.0/24 wgserver 192.168.9.1 custom_lan
2) Add a file /etc/kill-switch/kill-switch-setup-wgserver_r1.sh with following contents. Make the file executable.
/etc/openvpn/kill-switch/activate-kill-switch-for-interface.sh 192.168.91.0/24 wgserver_r1 192.168.91.1 custom_lan
3) Modify the /etc/hotplug.d/iface/99-wan-interfaces file with the following lines, leaving other lines as is.
...
wgserverstateret=`cat /tmp/wgserverstate`
wgserver_r1stateret=`cat /tmp/wgserver_r1state`
...
wgserverstarted=`echo "$wgserverstateret" started | awk '{ print ($1 == $2) ? 1 : 0 }'`
wgserver_r1started=`echo "$wgserver_r1stateret" started | awk '{ print ($1 == $2) ? 1 : 0 }'`
...
killswitchwgserverstateret=`cat /tmp/killswitchwgserverstate`
killswitchwgserver_r1stateret=`cat /tmp/killswitchwgserver_r1state`
...
killswitchwgserverstarted=`echo "$killswitchwgserverstateret" started | awk '{ print ($1 == $2) ? 1 : 0 }'`
killswitchwgserver_r1started=`echo "$killswitchwgserver_r1stateret" started | awk '{ print ($1 == $2) ? 1 : 0 }'`
...
activatewgserverkillswitch=0
activatewgserver_r1killswitch=0
...
if [ "${ACTION}" == "ifdown" ] && [ "${INTERFACE}" = "wgserver" ]
then
rm /tmp/killswitchwgserverstate
fi
if [ "${ACTION}" == "ifdown" ] && [ "${INTERFACE}" = "wgserver_r1" ]
then
rm /tmp/killswitchwgserver_r1state
fi
...
if [ "${ACTION}" == "ifup" ] && [ "${DEVICE}" = "wan" ]
then
echo started > /tmp/wanstate
...
if [ $wgserverstarted -eq 1 ] && [ $killswitchwgserverstarted -eq 0 ]
then
activatewgserverkillswitch=1
fi
if [ $wgserver_r1started -eq 1 ] && [ $killswitchwgserver_r1started -eq 0 ]
then
activatewgserver_r1killswitch=1
fi
fi
...
if [ "${ACTION}" == "ifup" ] && [ "${DEVICE}" = "wgserver" ]
then
echo started > /tmp/wgserverstate
if [ $wanstarted -eq 1 ] && [ $killswitchwgserverstarted -eq 0 ]
then
activatewgserverkillswitch=1
fi
fi
if [ "${ACTION}" == "ifup" ] && [ "${DEVICE}" = "wgserver_r1" ]
then
echo started > /tmp/wgserver_r1state
if [ $wanstarted -eq 1 ] && [ $killswitchwgserver_r1started -eq 0 ]
then
activatewgserver_r1killswitch=1
fi
fi
...
if [ $activatewgserverkillswitch -eq 1 ]
then
echo started > /tmp/killswitchwgserverstate
/etc/openvpn/kill-switch/kill-switch-setup-wgserver.sh
fi
if [ $activatewgserver_r1killswitch -eq 1 ]
then
echo started > /tmp/killswitchwgserver_r1state
/etc/openvpn/kill-switch/kill-switch-setup-wgserver_r1.sh
fi
...
exit 0
Now after restarting your router, Wireguard traffic will now use internet from ‘tun0’ VPN tunnel. Check if this is the case by observing traffic data in luci.
WPA3 WiFi
Your WiFi interfaces must be configured to use VPN tunnel, as described in the article mentioned earlier and set to WPA3 security, for client devices to have VPN access. The WiFi password must be kept secure, with a different Guest wireless network if needed.
The End
After implementation of these concepts, local routers and devices connected by Ethernet cables will not leak data, either by connected spyware or RF leakage. Cloud servers can also utilize Wireguard within their LAN networks to improve privacy and add a level of protection to traffic.
