Introduction
The present article deals with running windows processes using elevated prevliiges.There are also many other techniques for doing the above task like;-
1) The first technique is creating a manifest file and then adding the following given code.
<requestedExecutionLevel
level="asInvoker|highestAvailable|requireAdministrator"
uiAccess="true|false"/>
which is explained in there:http://msdn.microsoft.com/en-us/library/bb756929.aspx
2) Another technique is impersonating a User in your program.
which is explained in there;http://support.microsoft.com/default.aspx?scid=kb;en-us;Q306158
The technique which now I am going to explain is a little bit different from the conventional methodology.A tool created by Mr J.Robbins had made it very easy to perform elevated task with CMD.The details of tools are given in the link below:http://www.wintellect.com/blogs/jrobbins/elevate-a-process-at-the-command-line-in-vista
You need to put the elevate.exe in the follwing location to make it work
x86:C:\Windows\System32
x64:C:\Windows\SysWOW64
Sample usage is demonstrated below
1) Without Elevate Program
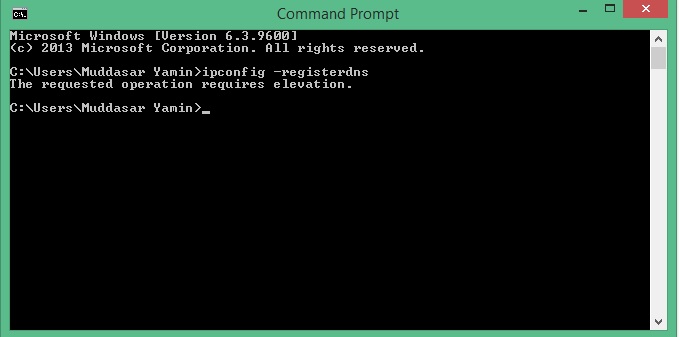
2) With Elevate Program
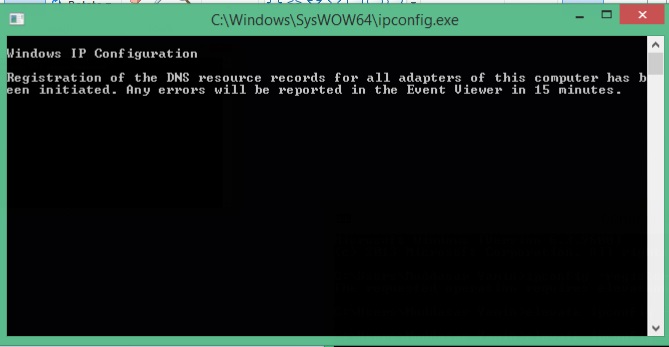
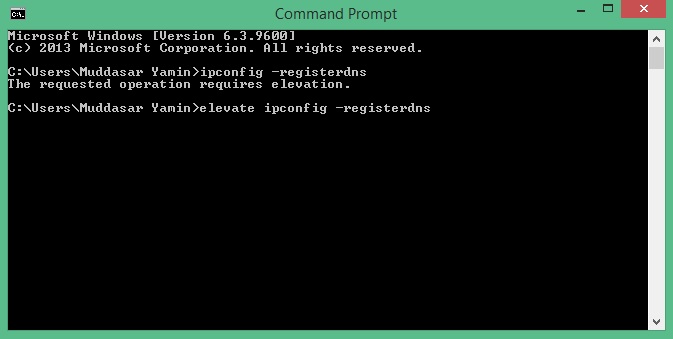
3) And finally the result
Background
I was working on a project in which I have to remotely mange windows firewall through an IOS device. I made a WCF webservice in which windows netshell commands are executed on my server.I donot know why impersonation and websevice manifest techniques did not work when I executed a task therefore I adopted this technique to achive the desired results .Some of the snapshots of IOS client are given below who uses the webservice .

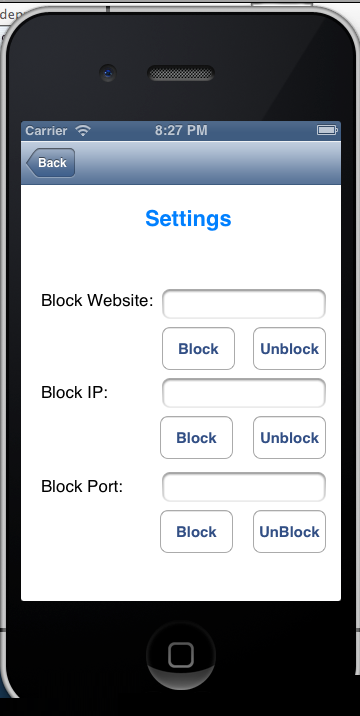
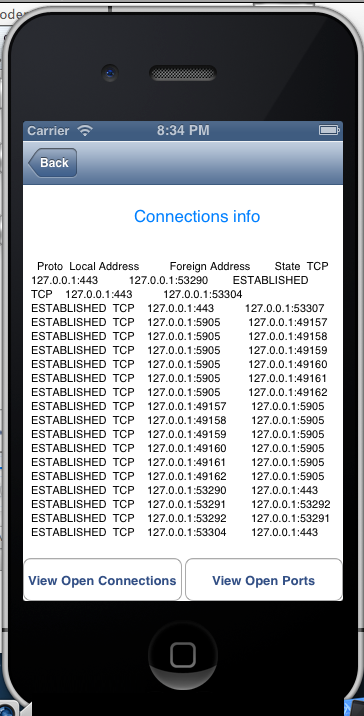
Using the code
The code of the wcf webservice is in c#, for ease I made small function to be executed on the server.Some of the the function which are related for executeing elevated processes are given below.
public string console(string command )
{
string result = "";
string output = string.Empty;
string error = string.Empty;
ProcessStartInfo processStartInfo = new ProcessStartInfo("cmd", "/c "+command);
processStartInfo.RedirectStandardOutput = true;
processStartInfo.RedirectStandardError = true;
processStartInfo.WindowStyle = ProcessWindowStyle.Normal;
processStartInfo.UseShellExecute = false;
Process process = Process.Start(processStartInfo);
using (StreamReader streamReader = process.StandardOutput)
{
output = streamReader.ReadToEnd();
}
using (StreamReader streamReader = process.StandardError)
{
error = streamReader.ReadToEnd();
}
result = output;
if (!string.IsNullOrEmpty(error))
{
result = error;
}
return result;
}<span style="font-size: 9pt;"> </span>
void blockweb(string ipadres)
{
string info = console("elevate netsh advfirewall firewall add rule name=\"" + System.DateTime.Today.Millisecond + "\" protocol=TCP localport=80 action=block dir=IN remoteip=" + ipadres);
}
string netinfo()
{
string info = console("netstat -an");
return info;
}
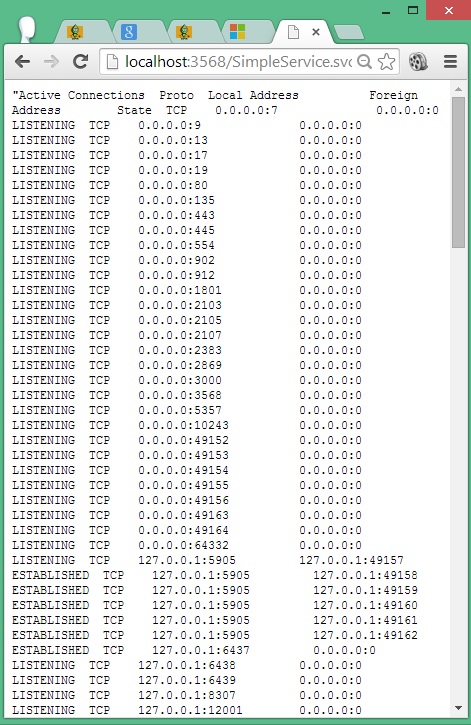
Points of Interest
Server end management tool for firwall is also built which i will explin in my next article
History
First vesion.
