Introduction
What is the 'Double-Hop' issue in PowerShell remoting? Let me give an example.
Suppose there are 3 machines named as M1, M2 and M3. Tom can enter a remote PowerShell session from M1 to manage M2 using his credential. Additionally, there is a shared folder on M3 with the UNC path - \\M3\Shared. Tom can access \\M3\Shared in Windows Explorer on both M1 and M2 using the same credential. Now we have the question: Is Tom able to access \\M3\Shared in his remote PowerShell session?
The answer is NO. The root cause is that Tom's credential can be passed from M1 to M2 but cannot be passed the second time from M2 to M3. This is the 'Double-Hop' issue in Windows authentication.
Solution
I assume you have already enabled PowerShell remoting successfully. If not, please refer to this article for setup steps.
The solution includes the following steps. Let me still use M1, M2 and M3 as machine names:
Step#1: Enable CredSSP on M1 to delegate your credentials to M2.
Enable-WSManCredSSP Client –DelegateComputer M2
Step#2: Allow incoming CredSSP connections on M2.
Enable-WSManCredSSP Server
Step#3: Enter a PowerShell remote session from M1 to manage M2 using CredSSP and your credentials.
Enter-PSSession M2 -Authentication CredSSP -Credential Tom
Now you should be able to access \\M3\Shared in the remote PowerShell session.
Important Troubleshooting
When you have applied the solution and try again on M1, you may encounter the following problem.
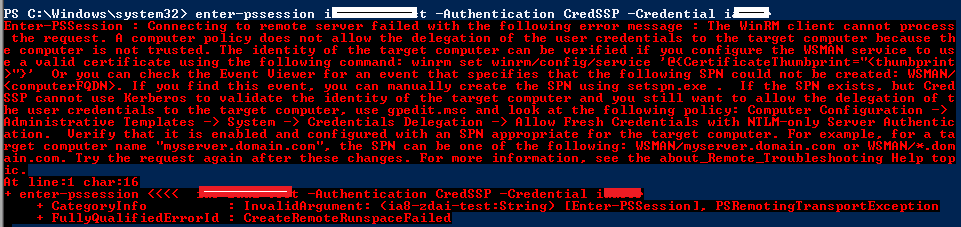
The following steps can fix this problem:
- Run gpedit.msc on M1.
- Expand to Local Computer Policy -> Computer Configuration -> Administrative Templates -> System -> Credentials Delegation.
- Double click Allow Delegating Fresh Credentials.
- Enable Allow Delegating Fresh Credentials.
- Click Show... and add wsman/M2.
- Click several OK to close the popup dialogs.
- If this still does not work, do the same to Allow Delegating Fresh Credentials with NTLM-only Server Authentication.
References
Reference links are listed below:
