Introduction
Using information technology today gets more and more sophisticated. The information that is being transferred and stored are often classified material of some kind and it is often necessary to prevent it from being read by third parties. The keyword for this particular problem is (both logical and physical) security. A part of the security aspect is encryption. Often people think that security is “just” something you plug in afterwards – it is definitely not!
A few rules of thumb when encryption is going to be included in the final product can be summarised into the following basics:
- Do not base the encryption on the algorithm itself.
- Make the algorithm public and the key private.
RSA Encryption
One of the most well known encryptions today is the RSA encryption. This form for encryption uses asymmetric keys. This means that you cannot evaluate the second key if you have the first one and vice versa.
The RSA encryption is a public-key crypto system, which uses two algorithms (E, D), one for encryption and one for decryption. You have a key pair containing: a secret key (sk) and a public key (pk).
m = D sk (E pk (m))
m = cd mod n AND c = me mod n <=>
m = (me mod n)d mod n
CBC Mode
The RSA encryption is typically using CBC mode (Cipher Block Chaining mode) when encrypting. This means the text that is being encrypted is divided into blocks. Each block is chained together, using the XOR operator, and then encrypted.
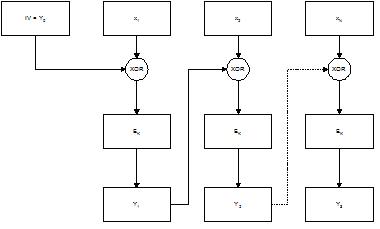
When using the CBC mode of operation it is required that all blocks have the same size. If the last block has a size less than the others then it will be necessary to use padding. The padding will then fill the block until it has the same size as the others. Formally the CBC mode operates in the following way, where we start with y0, which is a 64-bit initialisation vector:
y i = e k (y i-1 XOR x i), i >= 1
Doing the decryption, the entire operation is just reversed. This means that the cipher blocks are decrypted and then XORed. In this way we will end up with the clear text again.
x i = y i-1 XOR (d k (y i)) , i >= 1
Using the code
The Win32 Crypto API does provide some functionality, which can be used to perform an encryption. The advantage using the Crypto API is that you don’t need to use/find any third party cryptographic provider and figure out how it is installed and used. Simply use the one that sticks to the operating system. The disadvantage is clear – it is not simple to change to another operation system.
Before any functionality can be used it is necessary to create a context. This context is used several times when doing the encryption, so it is important that the handle is kept open until the encryption is done.
if (!CryptAcquireContext(&hProv, NULL, MS_DEF_PROV, PROV_RSA_FULL, 0))
{
dwResult = GetLastError();
if (dwResult == NTE_BAD_KEYSET)
{
if (!CryptAcquireContext(&hProv,
NULL, MS_DEF_PROV, PROV_RSA_FULL,
CRYPT_NEWKEYSET))
{
dwResult = GetLastError();
MessageBox("Error [0x%x]: CryptAcquireContext() failed.",
"Information", MB_OK);
return;
}
}
else {
dwResult = GetLastError();
return;
}
}
When we get the context, we need to get a (session) key, which we are going to use when doing the encryption. The key can be created from scratch or it can be imported from a file. In the following code snip, the pbBlob is (if not NULL) a binary that contains the key, which is fetched from a file.
if (pbBlob) {
if (!CryptImportKey(hProv, pbBlob, cbBlob, 0, 0, &hSessionKey))
{
dwResult = GetLastError();
MessageBox("Error [0x%x]: CryptImportKey() failed.",
"Information", MB_OK);
return;
}
}
else {
if (!CryptImportKey(hProv, PrivateKeyWithExponentOfOne,
sizeof(PrivateKeyWithExponentOfOne), 0, 0, &hKey))
{
dwResult = GetLastError();
MessageBox("Error CryptImportKey() failed.",
"Information", MB_OK);
return;
}
if (!CryptGenKey(hProv, CALG_RC4, CRYPT_EXPORTABLE, &hSessionKey))
{
dwResult = GetLastError();
MessageBox("Error CryptGenKey() failed.",
"Information", MB_OK);
return;
}
}
It is always a good idea to use the PKCS#7 standard, when storing the key. Please note that the project enclosed with this article does not use it.
After the key is imported or generated, it is now time to perform the encryption or decryption. The encryption and decryption depends on a session key, which is based on the key we just imported or generated previously.
void Encrypt()
{
unsigned long length = m_clear.GetLength() +1;
unsigned char * cipherBlock = (unsigned char*)malloc(length);
memset(cipherBlock, 0, length);
memcpy(cipherBlock, m_clear, length -1);
if (!CryptEncrypt(hSessionKey, 0, TRUE, 0, cipherBlock, &length, length))
{
dwResult = GetLastError();
MessageBox("Error CryptEncrypt() failed.", "Information", MB_OK);
return;
}
m_cipher = cipherBlock;
m_clear = "";
free(cipherBlock);
}
The decryption does not vary much from the encryption. Like with the encryption it is done with just one invocation and the cipher text is then decrypted.
void Decrypt()
{
unsigned long length = m_cipher.GetLength() +1;
unsigned char * cipherBlock = (unsigned char*)malloc(length);
memset(cipherBlock, 0, length);
memcpy(cipherBlock, m_cipher, length -1);
if (!CryptDecrypt(hSessionKey, 0, TRUE, 0, cipherBlock, &length))
{
dwResult = GetLastError();
MessageBox("Error CryptDecrypt() failed.",
"Information", MB_OK);
return;
}
m_clear = cipherBlock;
m_cipher = "";
free(cipherBlock);
}
Points of interest
The clear text / data is typically a string containing any text. Before performing the encryption it is a good idea to copy the data into an unsigned char pointer to avoid future problems with casts when the encryption is performed.
Finally, when using the Win32 Crypto API, please notice that it might not necessary compile as is. This is because a pre-processor definition is missing in the project.
#define _WIN32_WINNT 0x0400
When defining the above globally to the project, it will be possible to compile code that is using the Crypto API. My suggestion is to place the definition in the StdAfx.h file.
