1. Scope
The purpose of this project is to create a simple but neat steganography application that will enable users to hide their messages into seemingly "boring" data. In that way the "competitors" (or the spies...) who are stalking you will not be able to take notice of the message and your ultra-valuable secrets will be safe. Common technologies were used to create the application so as to keep it as simple as possible.
2. About Steganography
Steganography is the scientific art of concealing the presence of covert communications. In general, steganography approaches hide a message in a cover (e.g., text, image, audio file, etc.) in such a way that is assumed to look innocent and therefore not raise suspicion. Fundamentally, the steganographic goal is not to hinder an adversary from decoding a hidden message, but to prevent an adversary from suspecting the existence of covert communications.
There are many types of steganography. To name some of them:
- Textual steganography can be classified as textual format manipulation (TFM) and textual fabrication (TF). In TFM, comparing the original text with the modified text will reveal the hidden message. On the other hand, textual fabrication techniques hide a message either by generating an entire text cover, by employing methods such as null cipher and mimic functions, or manipulating an existing text using such methods as NICETEXT and SCRAMBLE, translation-based techniques.
- Image steganography is based on manipulating digital images to conceal a message. Such manipulation often renders the message as noise.
- Audio covers have also been pursued. Examples of audio steganography techniques include LSB, spread spectrum coding, phase coding, and echo hiding.
However contemporary steganography schemes either introduce noise to the original document used as a cover, or exploit noise in the data-hiding process. This entails various problems plus the danger of opponents being able to detect the message through various techniques (e.g. by analyzing the image and finding out that "noise" you put in it). For example image steganography suffers from several issues, such as the potential of distortion, the significant size limitation of the messages that can be embedded and the increased vulnerability of detection through contemporary image processing techniques.
This is why new methods of noiseless steganography are developed. Nostega conceals data in a steganographic cover that looks legitimate and is like any other ordinary material. The cover is then transmitted through an established covert channel such as the legitimate and innocent relationship between the sender and the receiver.
This is a paradigm of Noiseless Steganography (Nostega).
The way I use to implement that is called GraphStega: Graph Steganography Methodology (Graphstega) is the science and art of avoiding the arousal of suspicion in covert communications by concealing a message in a novel cover type, namely graph cover. We will use a simple Excel graph to do that.
Other methodologies of Nostega include:
- Chess Steganography Methodology (Chestega) exploits popular games such as chess, checkers, crosswords, dominoes, etc., to embed data in steganographic game cover
- Automatic Joke Generation Based Steganography (Jokestega). Who does not joke? The obvious answer is no one. Yet, when someone is joking, anything can be said. This legitimizes the use of joke-based steganography. Jokestega methodology takes advantage of recent advances in Automatic Joke Generation (AJG) techniques to automate the generation of textual steganographic cover.
- Summarization-Based Steganography Methodology (Sumstega) takes advantage of recent advances in automatic summarization techniques to generate a text cover [23,34]. Sumstega does not exploit noise (errors) to embed a message nor produce a detectable noise. Instead, it pursues the variations among the outputs of auto-summarization techniques to conceal data.
- and many others...
[source: "Noiseless Steganography: The Key to Covert Communications" by Abdelrahman Desoky, Auerbach Publications © 2012]
3. Application description
The application is consisted of two major functionalities:
1. Hiding a typed message into an Excel graph. [sending message]
2. Reading back an Excel graph (previously generated with the application) so as to decypher the hidden message. [receiving message]
3.1 Sending message
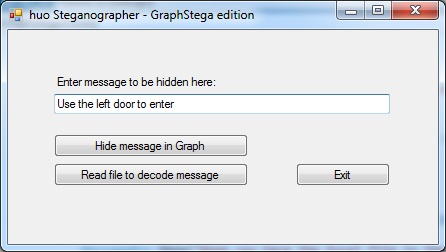
In order to send a message the user must first type it into the textBox available. Then all he has to do is press the button "Hide message in Graph".
When this happens, the program does the following:
1. It creates a new Excel file.
Excel.Application xlApp;
Excel.Workbook xlWorkBook;
Excel.Worksheet xlWorkSheet;
object misValue = System.Reflection.Missing.Value;
xlApp = new Excel.Application();
xlWorkBook = xlApp.Workbooks.Add(misValue);
xlWorkSheet = (Excel.Worksheet)xlWorkBook.Worksheets.get_Item(1);
2. It reads through every letter in the message.
3. Creates (gets) the ASCII code value of that letter.
4. Stores that value into a graph in the Excel file.
Byte[] encodedBytes = ascii.GetBytes(userMessage);
foreach (Byte b in encodedBytes)
{
xlWorkSheet.Cells[rowCounter, 1] = generalCounter.ToString();
xlWorkSheet.Cells[rowCounter, 2] = b.ToString();
rowCounter++;
generalCounter++;
} In that way the message is actually hidden in the data of the graph, as shown in the figure below.

The program then saves the file and the operation of "steganography" is complete.

If someone sees at the Excel file the only thing he will "see" will be a seemingly "innocent" graph with the pageview stats of a blog (Harmonia Philosophica is my philosophy blog by the way - take a look if philosophy is in your interests...). Who cares?
Right?
Wrong!
3.2 Receiving message
The receiver of the important message does care!
And all he has to do in order to read the hidden message is to take the file, put it into the same directory as the program and execute the program.
The application then will:
1. Open the Excel file
2. Read the values in the graph (these are the ASCII values stored before)
var fileName = string.Format("{0}\\fileNameHere", Directory.GetCurrentDirectory());
var connectionString = string.Format("Provider=Microsoft.Jet.OLEDB.4.0; data source={0}; Extended Properties=Excel 8.0;", "skakos-steganography.xls");
var adapter = new OleDbDataAdapter("SELECT * FROM [Sheet1$]", connectionString);
var ds = new DataSet();
adapter.Fill(ds, "anyNameHere");
DataTable data = ds.Tables["anyNameHere"]; 3. Create the relative char letter from the ASCII value
for (counter = 0; counter < data.Rows.Count; counter++)
{
valueReadFromExcel = data.Rows[counter][1].ToString();
MessageBox.Show(string.Concat("Reading inside Excel: ", valueReadFromExcel));
asciiValue = Int32.Parse(data.Rows[counter][1].ToString());
completeMessageDecoded = string.Concat(completeMessageDecoded, Convert.ToChar(asciiValue).ToString());
MessageBox.Show(string.Concat("Message up to now is: ", completeMessageDecoded));
} 4. Present the deciphered message to the user.

The code is very simple and intuitive.
It has comments, although they are not so much needed.
4. Possible improvements
Using the ASCII values is a very simple way of doing things and was done for educational purposes.
The program could enhance the way it encodes the data into the Excel file.
For example, it could use an algorithm to somehow change the ASCII values so as to avoid easy detection. It could for example convert those ASCII values into something else, by getting the binary value of the message (it is currently displayed for educational purposes in a messageBox), then split that binary value into segments of 7 characters and then use these values to create the Excel graph.
The possibilities are endless.
History
First version of article posted: 9/2012.
