CSRF stands for Cross site request forgery. So if you see the dictionary meaning of forgery:
“It’s an act of copying or imitating things like signature on a cheque, official documents to deceive the authority source for financial gains.”
So when it comes to website this forgery is termed as CSRF(Cross Site Request Forgery).
CSRF is a method of attacking a website where the attacker imitates a.k.a forges as a trusted source and sends data to the site. Genuine site processes the information innocently thinking that data is coming from a trusted source.
For example, consider the below screen of an online bank. End users use this screen to transfer money.
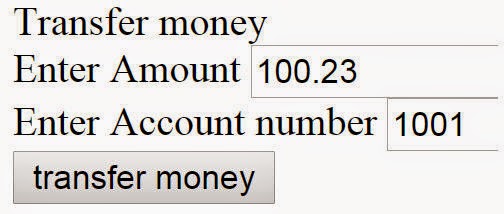
Below is a forged site created by an attacker which looks a game site from outside, but internally it hits the bank site for money transfer.

The internal HTML of the forged site has those hidden fields which have the account number and amount to do money transfer.
Win 1000000 US$ <form action="http://localhost:23936/Genuine/Transfer"
method=post> <input type=hidden name="amount" value="10000" />
<input type=hidden name="account" value="3002" />
<input type=submit value="Play the ultimate game" />
</form>
Now let’s say the user has logged into the genuine bank site and the attacker sent this forged game link to his email. The end user thinking that it’s a game site clicks on the “Play the Ultimate Game” button and internally the malicious code does the money transfer process.

So a proper solution to this issue can be solved by using tokens:
- End user browses to the screen of the money transfer. Before the screen is served, server injects a secret token inside the HTML screen in form a hidden field.
- Now henceforth when the end user sends request back, he has to always send the secret token. This token is validated on the server.

Implementing token is a two-step process in MVC:
First apply “ValidateAntiForgeryToken” attribute on the action.
[ValidateAntiForgeryToken]
public ActionResult Transfer()
{
return Content(Request.Form["amount"] +
" has been transferred to account "
+ Request.Form["account"]);
}
Second in the HTML UI screen, call “@Html.AntiForgeryToken()” to generate the token.
Transfer money <form action="Transfer" method=post>
Enter Amount <input type="text" name="amount" value="" />
Enter Account number <input type="text" name="account" value="" />
@Html.AntiForgeryToken() <input type=submit value="transfer money" /> </form>
So now henceforth when any untrusted source sends a request to the server, it would give the below forgery error.

If you do a view source of the HTML, you would find the below verification token hidden field with the secret key.
<input name="__RequestVerificationToken" type="hidden"
value="7iUdhsDNpEwiZFTYrH5kp/q7jL0sZz+CSBh8mb2ebwvxMJ3eYmUZXp+uofko6eiPD0fmC7Q0o4SXeGgRpxFp0i+
Hx3fgVlVybgCYpyhFw5IRyYhNqi9KyH0se0hBPRu/9kYwEXXnVGB9ggdXCVPcIud/gUzjWVCvU1QxGA9dKPA=" />
For further reading do watch the below interview preparation videos and step by step video series.
CodeProject
